
2021-12-28 14:25:52 Author: infosecwriteups.com(查看原文) 阅读量:29 收藏

This article is going to be about how I found my 1st RCE on one of India’s biggest e-commerce sites(+ a few more bugs).
Oswaal Books is a very popular company among high schoolers in India and the ones studying for competitive exams like JEE, NEET etc. They make guides, sample question papers, question banks etc. The story begins with a simple XSS bug. As I was trying to log in to my account one day, and I typed in the wrong password by mistake it displayed an error message saying that the password was invalid. The weird thing I noticed was that the error message was the same as the input given to the ‘errmsg’ parameter in the URL.

For those of you who have even just read the first few pages of the XSS chapter in the Web Hacker’s handbook know what to do. I just replaced the error message with my XSS payload and found another XSS bug.

A few months later as I was wandering on the site again, I decided to come back to this. This bug was now fixed, I edited my profile and saw that there was a success message but this was from the ‘errmsg’ parameter too. Tested for XSS here and got one. I realised that the ‘errmsg’ parameter is used in multiple places. I ran waybackurls on the domain and filtered all queries that had the ‘errmsg’ parameter.

If you look closely at these links, you will realise that I didn’t just find multiple links vulnerable to XSS but I also found a secret login page which I couldn’t find using directory brute force(URL 1).

I was quite excited looking at this page and tried all the basic textbook methods like trying to bypass captcha(failed), response code manipulation(failed), default credentials(failed). The last option was to try SQLi but it was a long shot as it didn’t work anywhere on the main website. I also realised that I had only tried GET based SQLi so I decided to go for POST based SQLi.
Try 1:
user = admin’
pass = test
And the error was triggered!
Try 2:
user = admin’ OR 1=1 --
pass = testAnd….. I was web admin!!!

Privileges:
1)Change password
2)Edit member details
3)View orders and tamper with its settings(cancel orders, initiate refund etc)
4)Edit books details(even prices)
5)Edit blogs, news etc
6)Look at resumes uploaded from the portal on the main site.
7)Edit SEO settings
8)View private customer info(address, phone number etc)


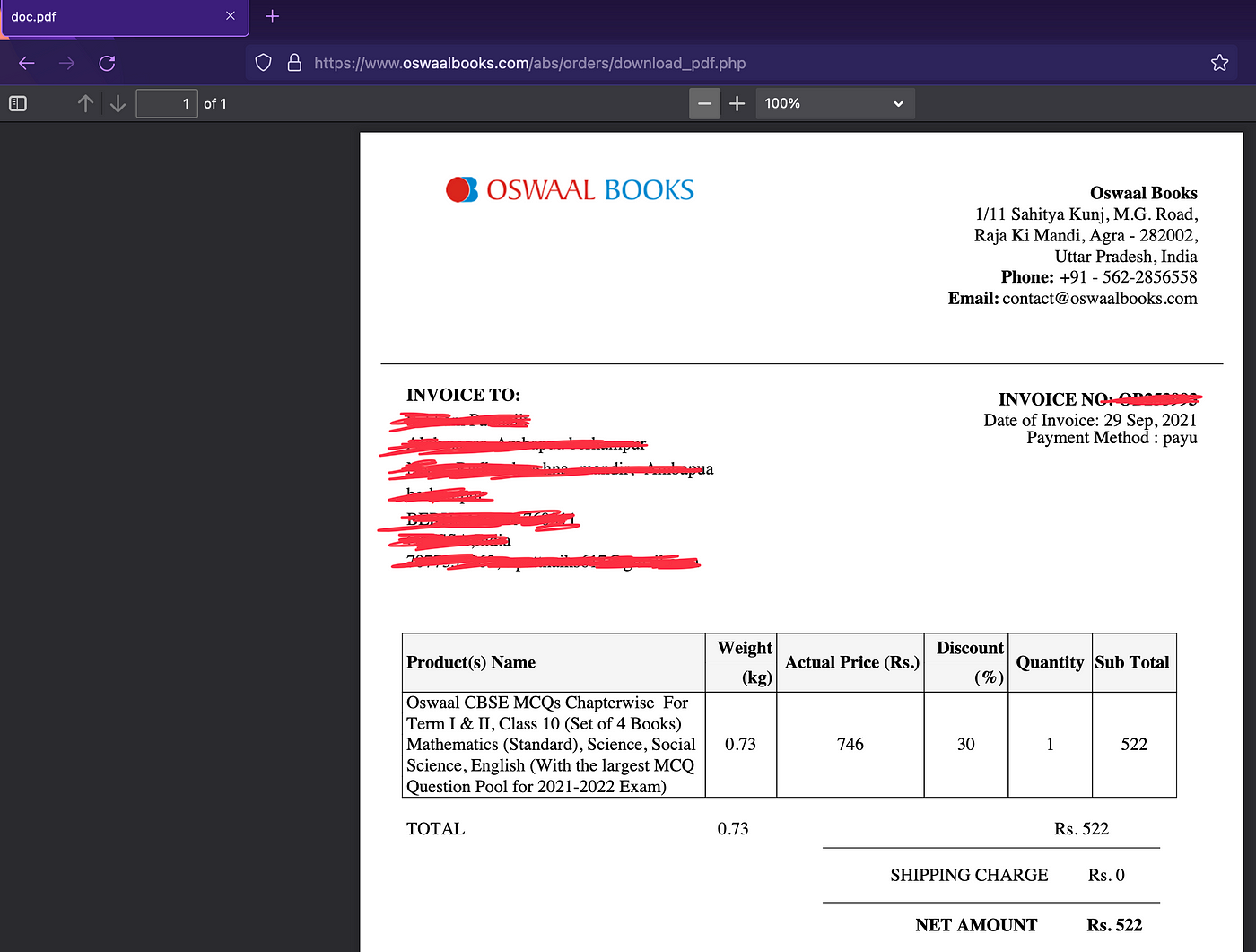
Moving on, getting into the admin panel was could but I wanted to see if I could do more. With all the new functionality I now have a higher chance at something big like an RCE. I explored the panel and navigated to the manage blog section. I chose an old and disabled blog for the test. I went to the edit section and tried tampering with the photo upload section.

Methodology:
- I first tried uploading a sample photo to see if the file was getting renamed, but it wasn’t(win 1)
- Tried to see what extensions it accepted(.php, .php5, .php4, .phtml, .php.jpg didn't work)
- Tried to see if the mime type was triggering any alerts.
- Finally changing the extension to ‘.PhP’ did the job
Here we go…

Bug 2: Price Manipulation [P2]
This bug was inspired by another writeup on the Infosec Write-ups page(can’t find the link now, please mention it in the comments if you know about it). All products were linked with a product ID so I couldn’t change the price by editing the request. However I could edit the quantity so I decided to place a negative integer in there, and that was bug 2…
Case 1:
Price: Rs 1000
Quantity: 1
Subtotal: 1000 x 1 = Rs 1000Case 2:
Price: Rs 1000
Quantity: 2
Subtotal: 1000 x 2 = Rs 2000Case 3:
Price: Rs 1000
Quantity: 3
Subtotal: 1000 x -2 = Rs -2000
With a negative cart value(eg: Rs 2000), I will not be able to reverse the transaction process and extract the amount from their account with a negative cart value, its like I have a discount coupon. So I can fill my cart up with all the products I want till I reach the minimum cart value.

3 books and a total amount of Rs. 0(This may not work in all cases and you may need to satisfy the minimum cart value to proceed).
Bug 3: Cross-Site Request Forgery[P3]
There is not a lot of explanation required here. The fact is that CSRF tokens were being used nowhere, even for sensitive actions.
Bug 4: Authentication bypass by response code manipulation[P3]
This vulnerability exists on the main login page. After entering my number I choose to sign in with my OTP.


Then I enter a test OTP and intercept the response. I get the response as ‘2’.

And here I just guessed(normally you would add the correct OTP and see what the right response is and then try to replicate it with a wrong OTP to see if authentication can be bypassed) and decided to change the response to ‘1’.

And that’s bug number 4…

Beyond bug hunting
Companies, especially with a large user base need to understand the importance of security. The above methods are some of the most basic methods used for pen-testing(I’d say this was like playing a CTF) and bug hunting. I just needed a few steps to get access on the site. Sensitive details could be leaked and harmful things like defacing of the website were also possible. This wouldn’t just affect the company or its brand value but also the users that trust it. That is why with great power comes great responsibility. Companies need to take responsibility for the data their customers trust to store with them.
Cyber security services might be costly but your users’ trust and security are worth every penny.
Reported: 29th September, 2021
Patched: 17th December, 2021
If you too are/were an Indian high-school student and used their products and enjoyed this write-up, please feel free to clap, follow me on Medium and Twitter.
Twitter: https://twitter.com/vikaran101
Thank you.
如有侵权请联系:admin#unsafe.sh