
Welcome back amazing hackers in this blog I came with another interesting topic RootMe walkthrough which is based on file upload and gaining shell find the flags.
Without wasting time let's get into the walkthrough. Firstly I perform a Nmap scan whether any useful information was obtained or not.

I had two open ports which were ports 22 and 80 opened. Then I opened 80 on the browser which was not interesting information.
I use the Gobuster tool for any hidden directory or some useful directories.

Then I find useful directories such as /uploads and /panel.
I redirected to /panel directory in a browser and checked out information and I saw one upload functionality there. I took PHP-reverse shell.php and modify the IP with my IP and I change the port number and started listening to Netcat.
nc -lvnp 4444
I Upload the PHP-reverse-shell.php but unfortunately couldn’t work.

So I refer to some bypassing techniques from googling it made me bypassed.
Instead of .php i use .phtml extension.
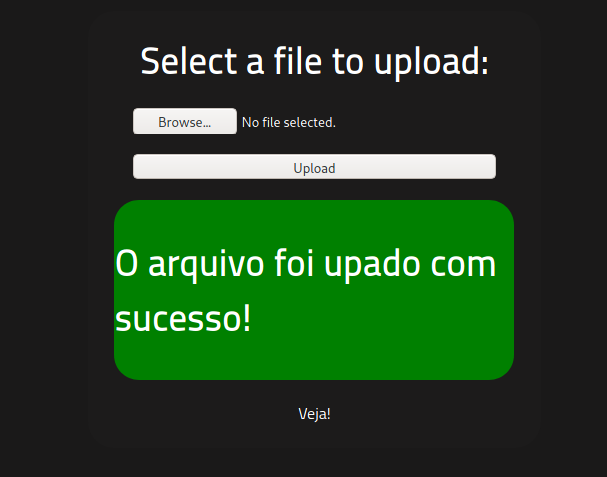
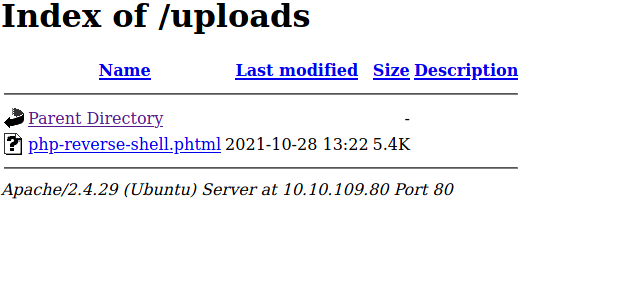
Then I navigated to /uploads location and I clicked the file Vola!!!
Then use python -c ‘import pty;pty.spawn(“/bin/bash”);’ for priviledge escalation for finding user flag

find / -type f -name user.txt where the file user.txt located

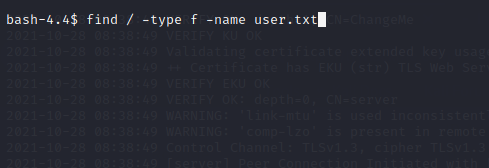
I found the location of user.txt using the above command.

I navigated that location and found the user flag.
The next task is to find the root flag. We know that for accessing the root directory we need SUID.
This time I use reverse shell based on accessing the root directory.
Firstly dug into target any strange files for gaining access to the root
To look for the files with SUID permission we can use the command:
find / -type f -user root -perm -4000 2>/dev/null

I use GTFObins site python reverse shell which escalates SUID permission.

Python -c ‘import os; os.execl(“/bin/sh”,”sh”,”-p”);’
which made me gain root access.

I finally found out root flag too.

如有侵权请联系:admin#unsafe.sh