
2021-12-08 17:04:12 Author: infosecwriteups.com(查看原文) 阅读量:25 收藏
Oct 3 · 3 min read
Content Spoofing is an injection in which user input is reflected as it is in the application response which can be used in phishing attacks.
During the recon phase, I found itunesconnect.apple.com, a subdomain of apple and after digging into it, I had observed that the content of the error key parameter was reflecting back to the page as shown below

With normal inline Cross-Site Scripting(XSS) payloads, the application was giving a blank pop-up. After trying different scenarios, I have observed that dangling markup injection is possible on the vulnerable parameters (errorKey)
Let’s understand the concept of Dangling Markup Injection
Dangling markup injection is very useful where we can’t find a way to execute our JavaScript due to input filters, content security policy, or other obstacles payloads but we can inject some HTML tags. It is used to steal the contents of the page without script by using resources such as images to send the data to a remote location that an attacker controls.
For our exploitation, I had used CSS @import as a payload. The main purpose of the @import method is to use multiple style sheets on a page.
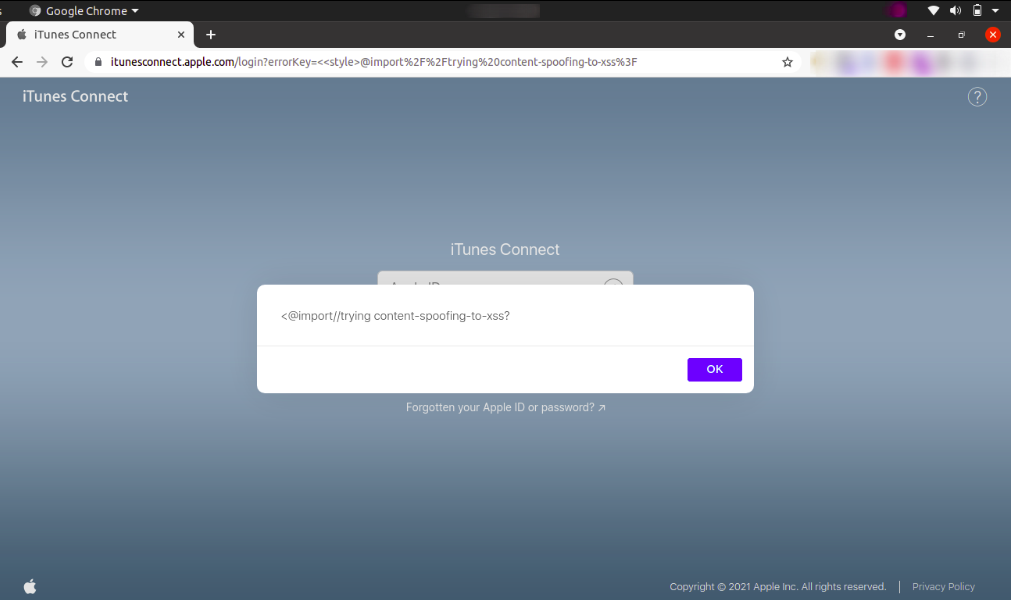
Time for the final payload to have a broken image linked to itunesconnect.apple.com itself which led to HTML injection.

Timeline
28th July 2021- Reported the issue to Apple Product Security Team.
29th July 2021- Got a reply from Apple with the Follow-up ID.
14th September 2021- The issue was patched. Asked Apple Team for an update.
20th September 2021- Apple team acknowledged and asked for the details to mention on their credit page in the next update cycle. The required details were shared the same day.
22nd September 2021- Mailed Apple Team for approval to publish a blog around this issue.
23rd September 2021- Apple Team wanted to review and provide feedback on the blog. Replied with the draft blog to Apple.
1st October 2021- Apple Team provided the go-ahead to publish the blog.

Reference
如有侵权请联系:admin#unsafe.sh