2021-09-28 22:05:00 Author: www.synopsys.com(查看原文) 阅读量:70 收藏
BSIMM12 gathers research on software security activities from real-life firms to create a guide that helps you navigate your software security initiative.
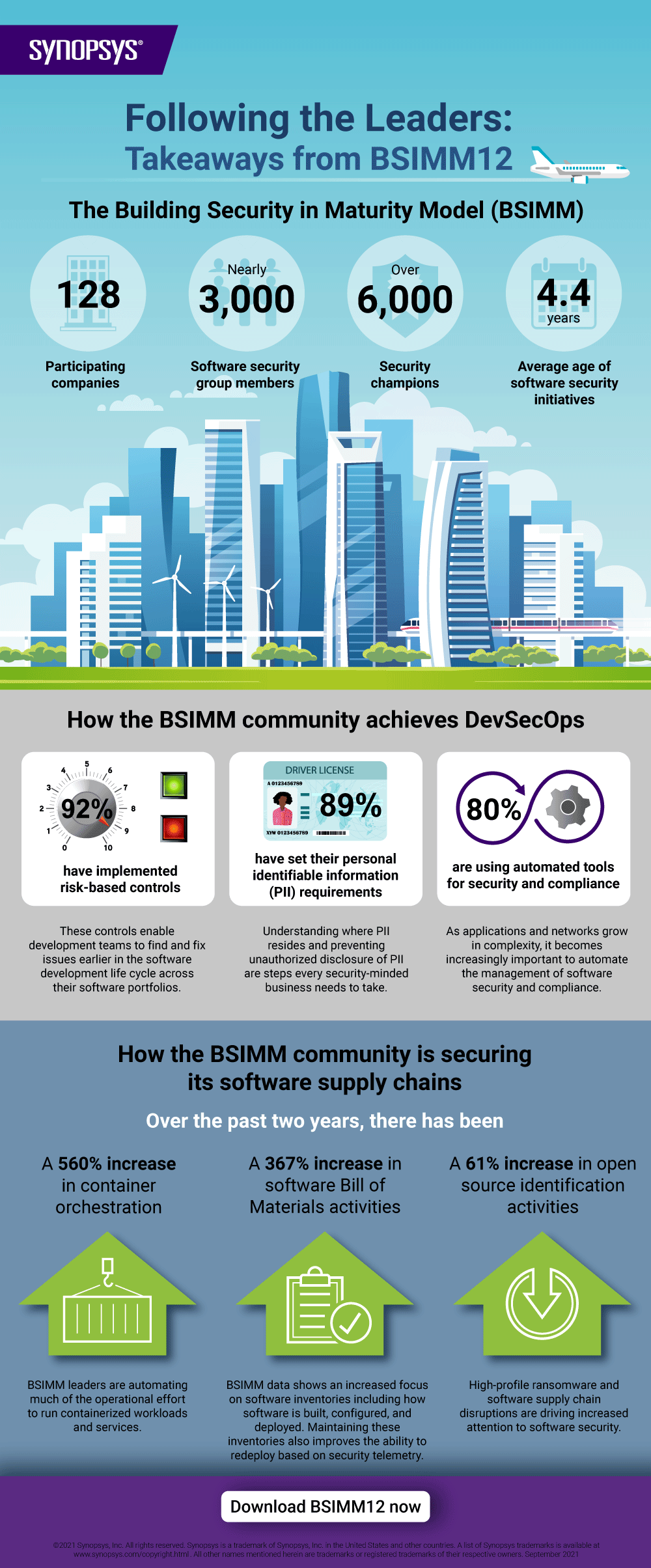
The popular business book, “The 7 Habits of Highly Effective People,” explores the theory that successful individuals share common qualities in achieving their goals, and that these qualities can be identified and applied by others. Applying the premise to software security, the Building Security In Maturity Model project, better known as BSIMM, examines organizations’ software security initiatives, conducts in-person interviews on those organizations’ activities, and publishes its findings annually. Now in its 12th iteration, the BSIMM report has grown from nine participating companies in 2008 to 128 in 2021, representing nearly 3,000 software security group members and over 6,000 satellite (aka Security Champion) members working with nearly 400,000 developers on over 150,000 applications.
The 2021 edition of the BSIMM report—BSIMM12—examines anonymized data from the software security activities of 128 organizations across various verticals, including financial services, FinTech, independent software vendors, IoT, healthcare, and technology organizations. Participating organizations include industry leaders such as Aetna, Bank of America, Citigroup, Freddie Mac, and Johnson & Johnson.
BSIMM12 demonstrates that every business is in the software business
Many of the organizations examined in BSIMM12 identify with traditional verticals, but all recognize that they are fundamentally in the software business. Software plays a leading role in every organization’s operations. Delays in software development and deployment affect product release dates, the lifeblood that drives revenue and profit. Businesses that sell software or sell products that include embedded software can’t afford to have security, compliance, or quality issues compromise their products.
Even businesses not directly engaged in selling software or software-driven products are just as dependent on software quality and security. Software drives the administrative systems for their payroll, billing, receivables, sales tracking, and customer records. Software controls their production, manages inventories, directs warehousing, and runs the distribution systems that keeps a business running. In service industries, software is used to analyze, optimize, model, interact with, and support customers.
The BSIMM12 findings tell us that software risk is business risk, and to effectively manage the second, you have to address the first.
Four top software security trends in BSIMM12
Software security groups are increasingly lending resources, staff, and knowledge to DevOps.
There is a shift away from mandating software security behaviors to having security teams forge partnerships with development teams—with an objective of proactively including security efforts into the critical path for software delivery.
Continuous testing is on the rise.
BSIMM12 data indicates that more firms are favoring continuous monitoring and reporting rather than using a point-in-time defect discovery approach and are then using security telemetry to drive improvements in software development and governance processes.
Decomposing tests into smaller, timely checks and running these more frequently.
The imperative to identify software issues as early as possible remains, driving the need to decompose big testing events into smaller, timely checks. But there is also a growing realization among software security groups that sometimes deployment orchestration or the post-deployment environment reflects the earliest, best opportunity for some tests.
Applying policy-as-code, or governance-as-code, is sharply increasing.
Governance-as-code moves security practices and adherence with compliance policies away from a manual approach to a more consistent, efficient, repeatable, and automated approach. BSIMM data collected in earlier years indicated that organizations were beginning the process of replacing manual, human-driven governance activities with automation. BSIMM12 observations now indicate the sole source of software security standards and policy is increasingly becoming human-readable configuration code or simplified code that conducts vulnerability discovery—the essence of software-defined life cycle governance.
Register for the BSIMM12 webinar to learn more
Following the leaders: What BSIMM12 indicates for security initiatives
Based on BSIMM12 data, organizations in the process of creating a software security initiative should consider the following key actions:
- Use security testing telemetry whenever possible to gather data such as what testing was performed and what issues were discovered to drive improvements in your software development life cycle (SDLC) and governance processes.
- Move toward automating security decisions with the end goal of auditable governance-as-code. Governance-as-code moves security practices and adherence to compliance away from a manual approach to a more consistent, efficient, and repeatable automated approach.
- Create a comprehensive software inventory (including a software bill of materials or BOM) of your assets, detailing both in-house created code as well as open source and third-party code.
- Implement small, phased, security activities throughout the SDLC, rather than using large, slow pass/fail gates that delay pipeline progress.
- Put automated security tools into place that can identify and help you remediate defects, vulnerabilities, and malicious code in your organization’s critical software, whether that software was developed in-house or by contractors, is commercial third-party software, or is open source.
Your roadmap to a better software security initiative starts here
Over the last 12 years, the BSIMM report has been used by organizations around the world as a measuring stick to compare their own SSIs against the broader BSIMM community. Organizations can evaluate their maturity, from “emerging,” (or getting started) to “maturing,” (meaning up and running) to “enabling,” or fine-tuning their existing security practices to improve their security posture.
Wherever your organization is on its journey, let BSIMM12 provide a roadmap to help you achieve your goals.
![]()
如有侵权请联系:admin#unsafe.sh