2021-09-15 21:48:29 Author: www.forcepoint.com(查看原文) 阅读量:46 收藏
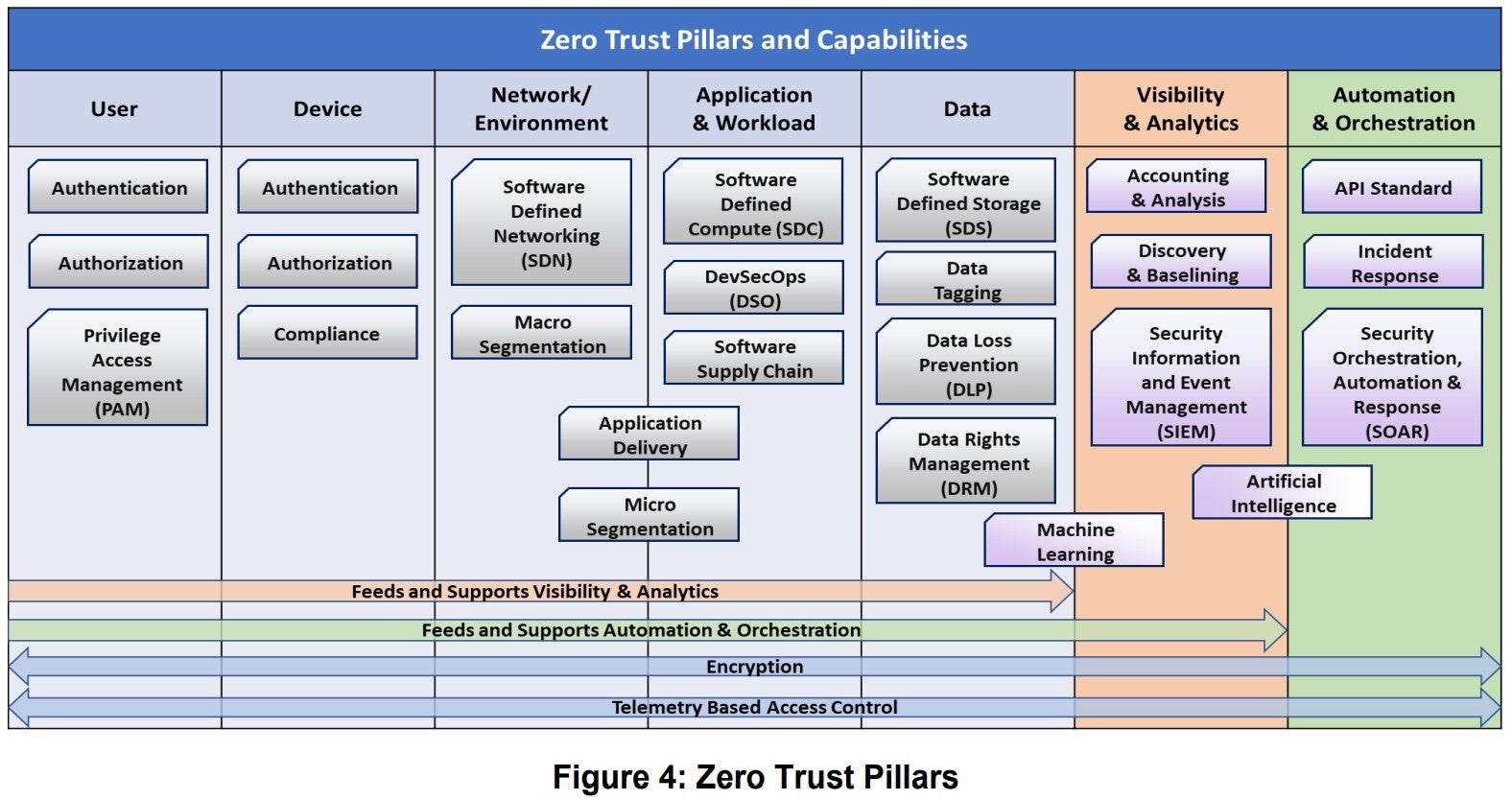
The Department of Defense breaks Zero Trust into seven pillars, each of which is a key focus area for implementation of Zero Trust controls. The first five pillars are users, devices, networks, applications, and data. As seen below, the last two pillars build on the first five.
With regard to data, federal agencies must have comprehensive data management strategy (i.e. encrypting data at rest and in transit) as well as data loss prevention (monitoring, analysis, and control of data whether in use, in transit, or at rest) strategies in place. DLP tools are endpoint protection systems that watch what a user does when they interact with data. But as the existence of other pillars suggests, a true Zero Trust approach doesn’t stop there.
The DoD’s sixth pillar is analytics: breaking down silos between the first five pillars to have a holistic or unified understanding of data, applications, networks, users, and devices. A data-first approach to Zero Trust integrates DLP into the broader architecture with an eye towards the continuous evaluation of threats—and the ability to automatically and quickly respond to them.
Put another way, agencies must be able to contextualize the use of data (how users interact with data and what data they’re accessing) for any given user over the entirety of the Zero Trust framework, including how the user interacts with devices, networks, and apps. Even when access is granted to a particular user, Zero Trust means continuing to monitor that access for red flags. By integrating DLP into a broader Zero Trust architecture, agencies can engage in forensic analysis, confidence scoring, and policy automation.
If an authorized user starts to access sensitive data they normally don’t interact with, or starts doing so at odd hours or from a suspicious location, that anomalous behavior—likely an indicator of a data breach—will be flagged. The seventh and final pillar is automation and orchestration: dynamically modifying that user’s access privileges to stop the breach in real time. Sometimes, that may mean requiring additional authentication steps. Other times, further access to data may be barred altogether.
In its early stages, Zero Trust focused heavily on identity and access. Now, organizations are increasingly realizing that data protection is paramount. Many agencies are turning to Secure Access Service Edge (SASE) to handle access to applications, networks, and devices—what’s coming in and out—through a converged cloud service. But agencies must also know what’s going on inside the network: who’s looking at data and how. That means not just implementing DLP and related tools but integrating them with the other focus areas.
Protecting data is top of mind for federal agencies, and for good reason. By taking a data-first approach to Zero Trust architecture, agencies can continuously vet and monitor users and data, keeping users safe wherever and however they log in. This enables agencies to deploy dynamic data policies, as opposed to relying on the outdated traditional perimeter and its all-or-nothing approach.
如有侵权请联系:admin#unsafe.sh