
2021-09-05 17:22:10 Author: infosecwriteups.com(查看原文) 阅读量:135 收藏
Hey, Today I will showcase how I found a file upload vulnerability which I bypassed and popped a reverse shell .

Initially being a private program, lets call it xyz.com. They had a functionality to upload a profile pic which only accepts jpg, png, jpeg images.
Starting with I tried uploading a php-reverse shell file which you can get from pentestmonkey
Tricks I tried to upload a reverse-shell but miserably failed :
- Just uploading .php file instead of jpg file.
- Trying double extensions to bypass and upload php file pic.jpg.php or pic.php.jpg
- Changing Content-type filtering i.e., changing Content-Type: txt/php to image/jpg
- Tried Case sensitives — pic.PhP also tried pic.php5, pHP5.
- Tried special characters to bypass pic.php%00 , pic.php%0a, pic.php%00
All the above scenarios didn’t worked at all, obvious they are the basic security remediations companies keep it.
Now lets try something new, Have you heard of magic numbers ?
Basically every file extension has its own magic number, and I took a php-reverse-shell.php file and using hex editor I added the magic number of jpeg i.e., FF D8 FF E0 at start of the php file using the hex tool.
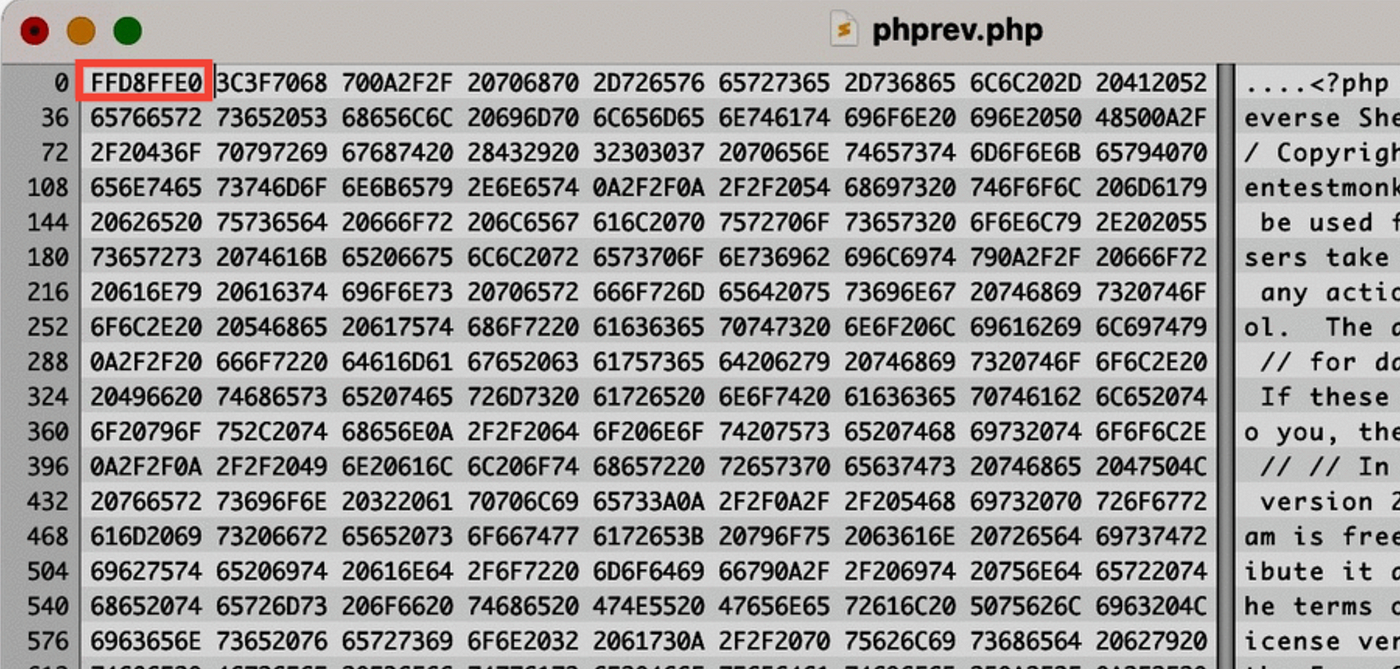
I just uploaded the file and it worked!
Then just by clicking on view profile got me an access to the reverse shell.
Reason behind this worked is because,
“ the image filters are looking at the ‘Magic Number’ at the beginning of a file to determine if it is a valid image and that is where we just bypassed. ”
Reported, Rewarded — $*****
Hope you like this sweet and short story of file upload vulnerability I have found.
If you have questions and anything about the post you want to ask me, please contact me via Twitter(security_donut) My DMs are always open.
See you soon with next article!
如有侵权请联系:admin#unsafe.sh