2021-08-25 01:50:46 Author: infosecwriteups.com(查看原文) 阅读量:114 收藏
Hello Security Researchers & Hackers
In this article I will talk about how you can get your Own Private Collaborator without the needs to buy a new domain or use any other tool
Pr-requirements
All you need is BurpSuite Pro / VPS 5$ is enough , you can get yourself one from DigitalOcean with 100$ Balance for 2 Months Here, We will also need Wireshark you can download it from Here
Open Burp-suite and go to Project-Options and Enable Poll over unencrypted HTTP and open Wireshark as well
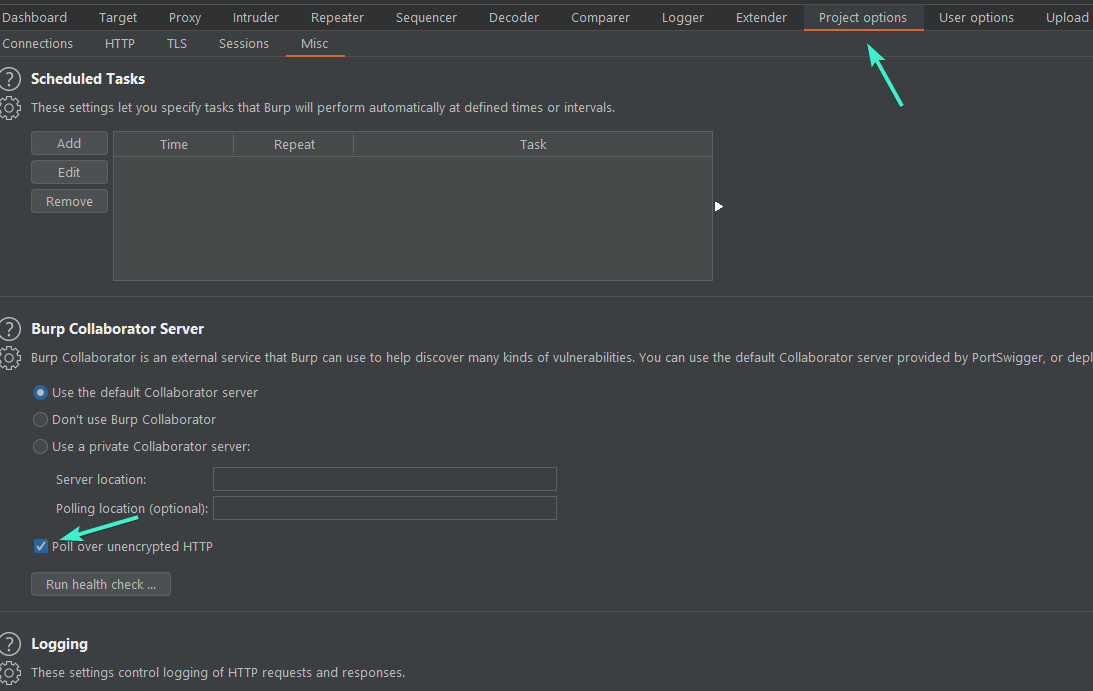
Before clicking Run Health Check check your connection devise in Wireshark (WIFI / Ethernet) It should look like the one that has spikes which means traffic on for my case I used Ethernet so I click on it

Now go back to burp and Run the Health check and wait a little bit
Once it’s done it will look like this

Now you can go back to Wireshark and in the filter search type HTTP and look for a results that has /burpresults?biid= it should normally be the burp request intercepted
Right Click on it and click on Follow HTTP, it should look like this below
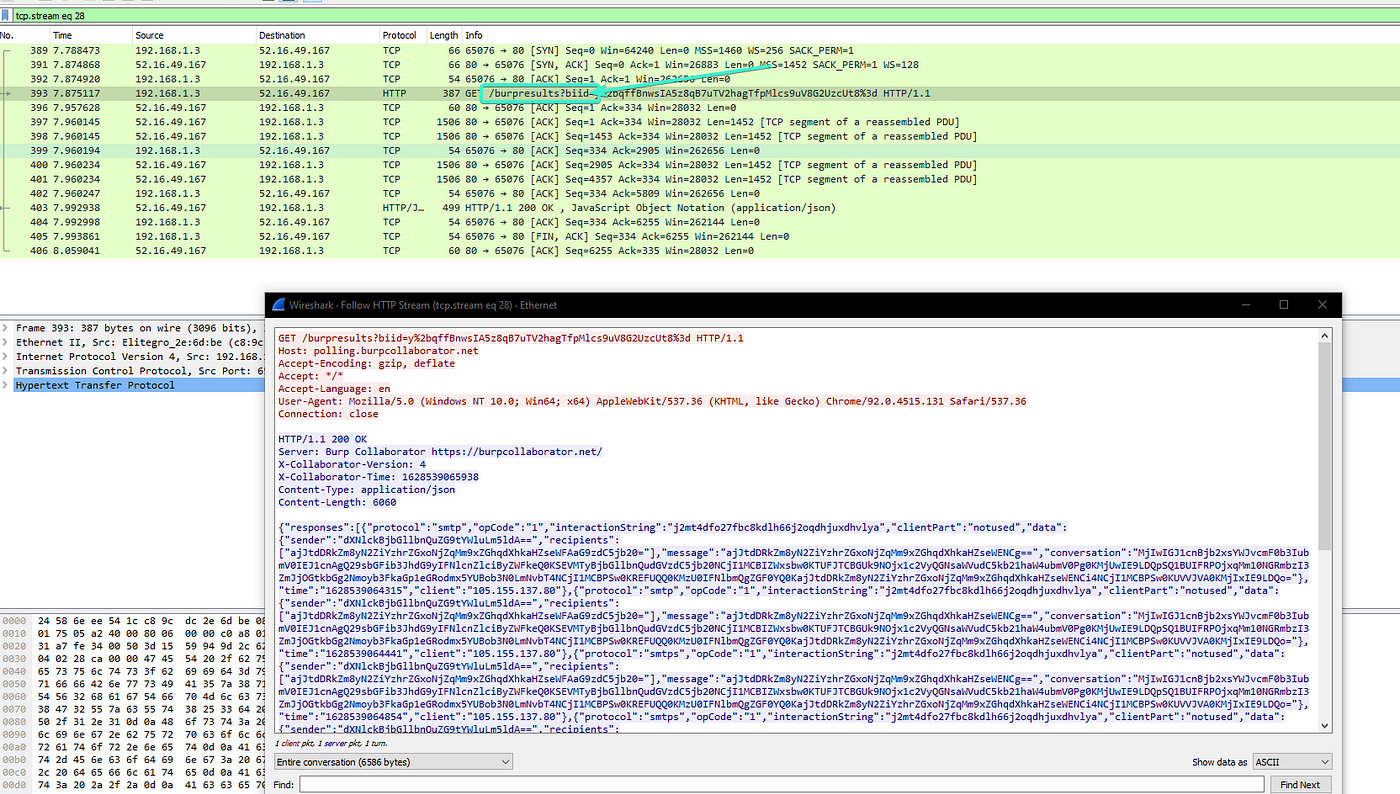
Copy the whole response and search for burp domain under DNS or HTTP and also copy the token in BIID parameter we will need it to use it in the poll request endpoints
Once you’ve done all that you can clone this repo in your VPS Here
Open the index.php and add the BIID token where it’s mentioned

Now send the index.php to your Apache directory and active Apache service
and go to your browser with the burp collaborator we copied from earlier and if all goes well you will see the callbacks

N.B: If you have missed a step or something went wrong with the setup , I have recorded a video where I show all the steps together Here
Hope you enjoyed reading this catch you till next time
Happy Hunting
如有侵权请联系:admin#unsafe.sh