
2019-08-19 01:01:00 Author: xz.aliyun.com(查看原文) 阅读量:145 收藏
说明
修改nmap的特征流量,过 emergingthreats 的公开ids规则。
参考
前置资料
ip 包格式

tcp 包格式

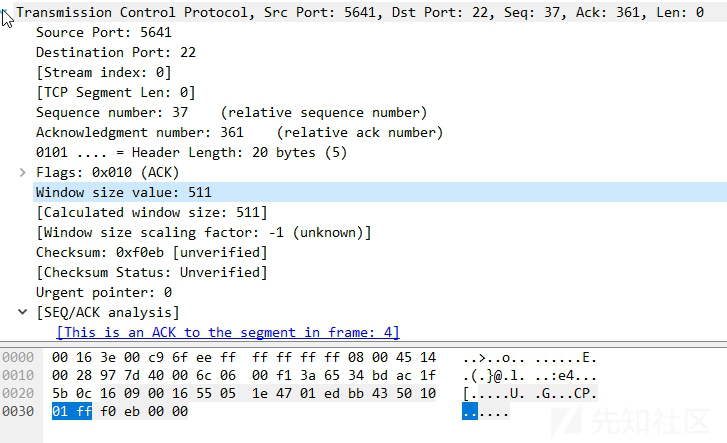
tcp 三次握手四次挥手
规则
规则语法
https://redmine.openinfosecfoundation.org/projects/suricata/wiki/Suricata_Rules
http://manual-snort-org.s3-website-us-east-1.amazonaws.com/node33.html
nmap 扫描说明
nmap-service-probes 文件
https://www.cnblogs.com/liun1994/p/6986544.html
https://nmap.org/book/vscan-fileformat.html
查询不同服务的探测报文和解析识别响应的匹配表达式。面向行进行解释。
语句
Exclude Directive
Exclude <port specification>
此指令从版本扫描中排除指定的端口,仅使用一次,在所有探针之前,文件的顶部。
当前为Exclude T:9100-9107--allports指令,可以覆盖Exclude指令。
这里尝试了下载9103端口开了个http服务,运行nmap -sV 127.0.0.1 -p9000-9200 --script=http-headers
结果如下,明显没进行服务识别。将自己的服务开在9100-9107 端口 也是个增加攻击者筛选成本的好办法PORT STATE SERVICE VERSION 9103/tcp open jetdirect? Excluded from version scan
- Probe Directive
Probe <protocol> <probename> <probestring>- protocol TCP或UDP
- probename probe的名称 描述
- probestring 告诉nmap发送什么数据包
q|.....|例如get 请求q|GET / HTTP/1.0\r\n\r\n|
支持转义\\ \0, \a, \b, \f, \n, \r, \t, \v, and \xHH (hex编码)
match Directive
match <service> <pattern> [<versioninfo>]- service 服务名 ssh, smtp, http...
- pattern
m/[regex]/[opts]regex格式采用Perl语言格式;目前opts支持“i”,代表的含义是匹配不区分大小写;“s”:代表在‘.’字符后面有新行 versioninfo
| Field format | Value description |
| -------------------- | --------------------------------------------------------- |
| p/vendorproductname/ | 供应商或者服务明 |
| v/version/ | 应用的版本信息,$1的意思由match指令中第一个()的内容替换; |
| i/info/ | 其他进一步的信息 |
| h/hostname/ | 主机名 |
| o/operatingsystem/ | 服务在什么操作系统之上 |
| d/devicetype/ | 服务运行的设备类型 |
| cpe:/cpename/[a] | nmap通用的指纹格式 |在某些情况下,帮助函数可以用在替换之前, i/$P(3)/ $P()函数将会过滤掉不可打印的字符;另一个帮助函数是 $SUBST().在打印之前做替换; v/$SUBST(1,"_",".")/ 意思是在打印$1之前,将'_'替换成'.'打印。
- softmatch Directive
softmatch <service> <pattern>
示例:与match一样,不过softmatch之后,扫描继续,但是服务名作为已知条件。softmatch ftp m/^220 [-.\w ]+ftp.*\r\n$/i softmatch smtp m|^220 [-.\w ]+SMTP.*\r\n| softmatch pop3 m|^\+OK [-\[\]\(\)!,/+:<>@.\w ]+\r\n$|
- ports and sslports Directives
ports <portlist>
示例:告诉Nmap探针所要发送数据的端口,在每个probe下面,仅使用一次ports 21,43,110,113,199,505,540,1248,5432,30444 ports 111,4045,32750-32810,38978
- totalwaitms Directive
totalwaitms <milliseconds>
等待时间 - tcpwrappedms Directive
tcpwrappedms <milliseconds>
该指令仅用于NULL探针。 如果服务在此计时器用尽之前关闭TCP连接,则该服务标记为tcpwrapped。 否则,匹配继续照常。 - rarity Directive
rarity <value between 1 and 9>
大致对应于这种探测很少会返回有用结果。 数字越大,探测器就越罕见,对服务的可能性就越小。 更多细节可以在“探针选择和稀有度”一节中找到。
--version-intensity 用来调整使用哪些等级的Probenmap -sV --version-intensity <intensity level between 0 and 9> 设置0—9 对应的Probe 做匹配 nmap -sV --version-light 设置intensity 为 2 nmap -sV --version-all 设置intensity 为 9 即全部匹配 - fallback Directive
fallback <Comma separated list of probes>
此指令用于指定哪个探针作为回退,如果当前探针没有匹配项;由于前一个探针可能返回数据很慢,因此可以开启新的探针,将新探针的结果与前面的匹配。
示例
# This probe sends a SIP OPTIONS request.
# Most of the numbers, usernames, and hostnames are abitrary.
##############################NEXT PROBE##############################
Probe TCP SIPOptions q|OPTIONS sip:nm SIP/2.0\r\nVia: SIP/2.0/TCP nm;branch=foo\r\nFrom: <sip:[email protected]>;tag=root\r\nTo: <sip:[email protected]>\r\nCall-ID: 50000\r\nCSeq: 42 OPTIONS\r\nMax-Forwards: 70\r\nContent-Length: 0\r\nContact: <sip:[email protected]>\r\nAccept: application/sdp\r\n\r\n|
rarity 5
ports 406,5060,8081,31337
sslports 5061
fallback GetRequest
# Some VoIP phones take longer to respond
totalwaitms 7500
match atalla m|^<00#020035#0101##>\r\n<00#020035#0101##>\r\n<00#020035#0101##>\r\n| p/Atalla Hardware Security Module payment system/ d/specialized/
match honeypot m|^HTTP/1\.0 200 OK\r\nAllow: OPTIONS, GET, HEAD, POST\r\nContent-Length: 0\r\nConnection: close\r\n\r\n| p/Dionaea Honeypot httpd/
match honeypot m|^SIP/2\.0 200 OK\r\nContent-Length: 0\r\nVia: SIP/2\.0/TCP nm;branch=foo\r\nFrom: sip:[email protected];tag=root\r\nAccept: application/sdp\r\nTo: sip:[email protected]\r\nContact: sip:[email protected]\r\nCSeq: 42 OPTIONS\r\nAllow: REGISTER, OPTIONS, INVITE, CANCEL, BYE, ACK\r\nCall-ID: 50000\r\nAccept-Language: en\r\n\r\n| p/Dionaea Honeypot sipd/
......检测规则以及对应修改
ping 扫描
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"GPL SCAN PING NMAP"; dsize:0; itype:8; reference:arachnids,162; classtype:attempted-recon; sid:2100469; rev:4; metadata:created_at 2010_09_23, updated_at 2010_09_23;)
- dsize 检查包的数据部分大小 0
- itype 检测icmp type 值
基本用不到ping 扫描
-sS (TCP SYN扫描)
发送一个SYN报文, 就像您真的要打开一个连接,然后等待响应。 SYN/ACK表示端口在监听 (开放),而 RST (复位)表示没有监听者。如果数次重发后仍没响应, 该端口就被标记为被过滤。如果收到ICMP不可到达错误 (类型3,代码1,2,3,9,10,或者13),该端口也被标记为被过滤。
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -sS window 2048"; fragbits:!D; dsize:0; flags:S,12; ack:0; window:2048; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000537; classtype:attempted-recon; sid:2000537; rev:8; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -sS window 1024"; fragbits:!D; dsize:0; flags:S,12; ack:0; window:1024; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2009582; classtype:attempted-recon; sid:2009582; rev:3; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -sS window 3072"; fragbits:!D; dsize:0; flags:S,12; ack:0; window:3072; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2009583; classtype:attempted-recon; sid:2009583; rev:3; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -sS window 4096"; fragbits:!D; dsize:0; flags:S,12; ack:0; window:4096; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2009584; classtype:attempted-recon; sid:2009584; rev:2; metadata:created_at 2010_07_30, updated_at 2010_07_30;)- fragbits 检查ip头的分片标志位 !D
- dsize 检查包的数据部分大小 0
flags 检查tcp flags的值 S,12
这个和速率有关系
保留位“1”和“2”分别用“C”和“E”代替,以匹配RFC 3168,“向IP添加显式拥塞通知(ECN)”。 “1”和“2”的旧值对于flag关键字仍然有效,但现在已弃用。| flag | 说明 |
| ---- | ----------------|
| F | FIN - Finish (LSB in TCP Flags byte) |
| S | SYN - Synchronize sequence numbers |
| R | RST - Reset |
| P | PSH - Push |
| A | ACK - Acknowledgment |
| U | URG - Urgent |
| C | CWR - Congestion Window Reduced (MSB in TCP Flags byte) 简单来说就是网络不是很畅通了,通知对方减少阻塞窗口,发包速度发慢一点。 |
| E | ECE - ECN-Echo (If SYN, then ECN capable. Else, CE flag in IP header is set) ECN两个作用,在TCP三次握手时表明TCP端是否支持ECN;在传输数据时,发送方是无法知道网络是否畅通的,但是经过重重的路由后,路由根据网络的情况可以知道是否阻塞,路由会设置在IP层会设置的相应的标志,即接收端发现了拥塞。CWR为发送端缩小拥塞窗口标志,用来通知发送端它已经收到了设置ECN标志,应该减慢发包速度。关于ECN的详细描述请参考 |
| 0 | No TCP Flags Set The ollowing modifiers can be set to change the match criteria: |
| 2 | Reserved bit 2 |
| 1 | Reserved bit 1 (MSB in TCP Flags byte) |
| + | match on the specified bits, plus any others |
| * | match if any of the specified bits are set |
| ! | match if the specified bits are not set |
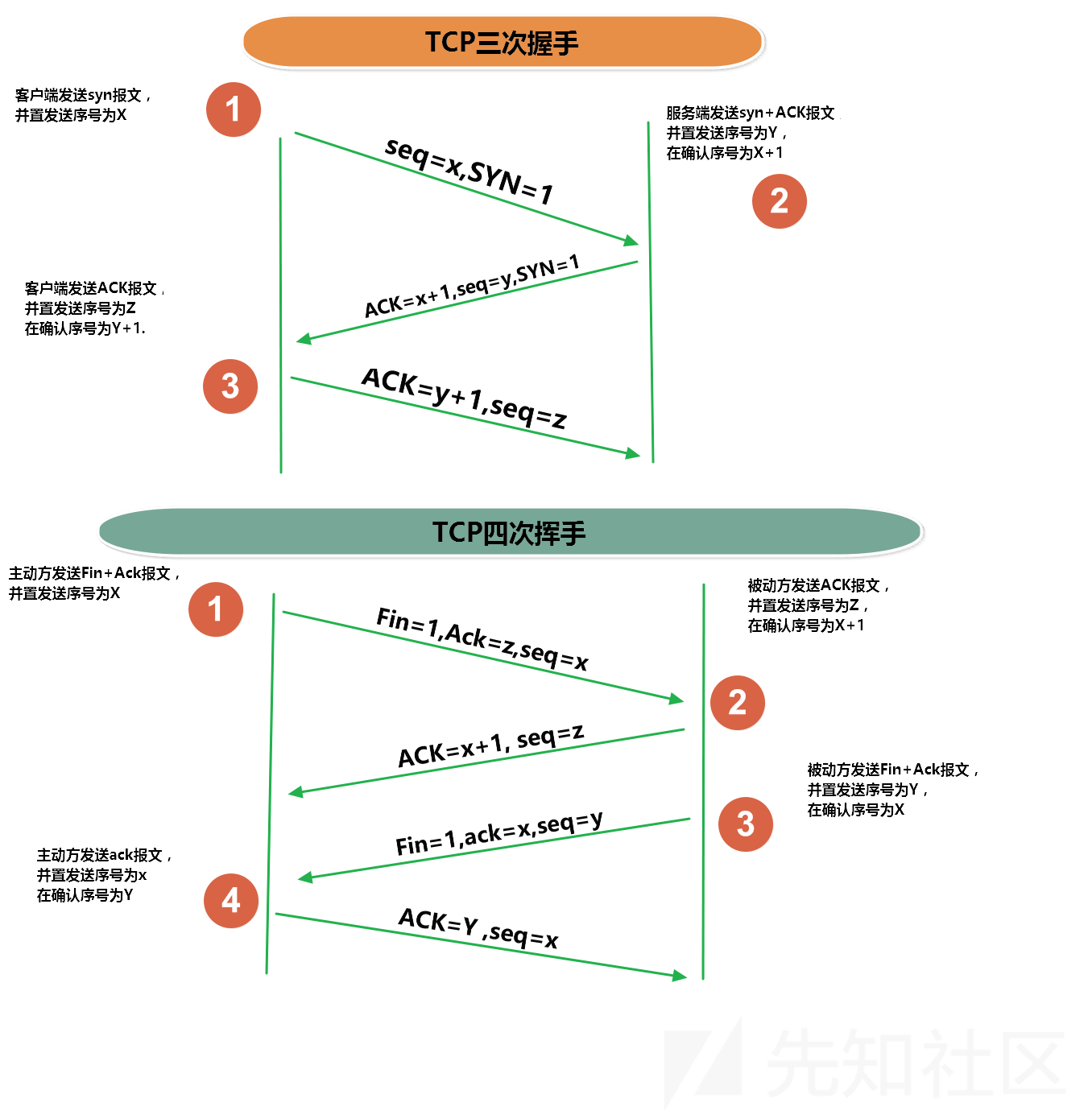
- ack 检查tcp应答(acknowledgement)的值 0
- window 关键字用于检查特定的TCP窗口大小。 2048 1024 3072 4096
扫描报文
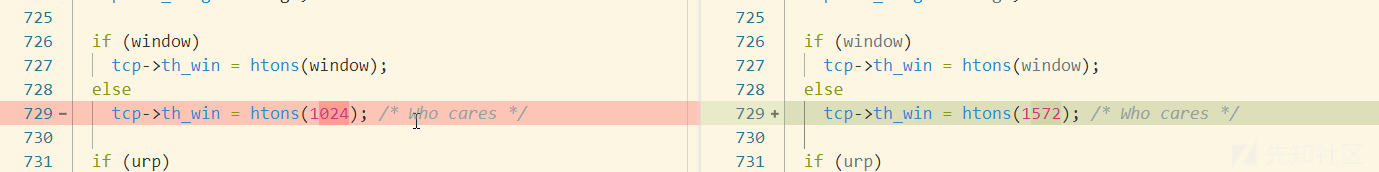
修改tcp窗口大小即可
修改 tcpip.cc
-sT (TCP connect()扫描)
创建connect() 系统调用进行扫描。
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"GPL SCAN nmap TCP"; ack:0; flags:A,12; flow:stateless; reference:arachnids,28; classtype:attempted-recon; sid:2100628; rev:8; metadata:created_at 2010_09_23, updated_at 2010_09_23;)
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"GPL SCAN nmap XMAS"; flow:stateless; flags:FPU,12; reference:arachnids,30; classtype:attempted-recon; sid:2101228; rev:8; metadata:created_at 2010_09_23, updated_at 2010_09_23;)
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"GPL SCAN nmap fingerprint attempt"; flags:SFPU; flow:stateless; reference:arachnids,05; classtype:attempted-recon; sid:2100629; rev:7; metadata:created_at 2010_09_23, updated_at 2010_09_23;)flags:A,12 只检查了标志位,应该降速扫描即可。
-sU (UDP扫描)
-sN; -sF; -sX (TCP Null,FIN,and Xmas扫描)
这三种扫描类型 (甚至用下一节描述的 --scanflags 选项的更多类型) 在TCP RFC 中发掘了一个微妙的方法来区分open(开放的)和 closed(关闭的)端口。第65页说“如果 [目标]端口状态是关闭.... 进入的不含RST的报文导致一个RST响应。” 接下来的一页 讨论不设置SYN,RST,或者ACK位的报文发送到开放端口: “理论上,这不应该发生,如果您确实收到了,丢弃该报文,返回。 ”
如果扫描系统遵循该RFC,当端口关闭时,任何不包含SYN,RST,或者ACK位的报文会导致 一个RST返回,而当端口开放时,应该没有任何响应。只要不包含SYN,RST,或者ACK, 任何其它三种(FINPSH,and URG)的组合都行。Nmap有三种扫描类型利用这一点:
Null扫描 (-sN)
不设置任何标志位(tcp标志头是0)
FIN扫描 (-sF)
只设置TCP FIN标志位。
Xmas扫描 (-sX)
设置FIN,PSH,和URG标志位,就像点亮圣诞树上所有的灯一样。alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -f -sF"; fragbits:!M; dsize:0; flags:F,12; ack:0; window:2048; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000543; classtype:attempted-recon; sid:2000543; rev:7; metadata:created_at 2010_07_30, updated_at 2010_07_30;) alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -f -sN"; fragbits:!M; dsize:0; flags:0,12; ack:0; window:2048; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000544; classtype:attempted-recon; sid:2000544; rev:7; metadata:created_at 2010_07_30, updated_at 2010_07_30;) alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -f -sX"; fragbits:!M; dsize:0; flags:FPU,12; ack:0; window:2048; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000546; classtype:attempted-recon; sid:2000546; rev:7; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
除了探测报文的标志位不同,这三种扫描在行为上完全一致。 如果收到一个RST报文,该端口被认为是 closed(关闭的),而没有响应则意味着 端口是open|filtered(开放或者被过滤的)。 如果收到ICMP不可到达错误(类型 3,代号 1,2,3,9,10,或者13),该端口就被标记为 被过滤的。
这些扫描的关键优势是它们能躲过一些无状态防火墙和报文过滤路由器。 另一个优势是这些扫描类型甚至比SYN扫描还要隐秘一些。但是别依赖它 -- 多数 现代的IDS产品可以发现它们。一个很大的不足是并非所有系统都严格遵循RFC 793。 许多系统不管端口开放还是关闭,都响应RST。 这导致所有端口都标记为closed(关闭的)。 这样的操作系统主要有Microsoft Windows,许多Cisco设备,BSDI,以及IBM OS/400。 但是这种扫描对多数UNIX系统都能工作。这些扫描的另一个不足是 它们不能辨别open(开放的)端口和一些特定的 filtered(被过滤的)端口,从而返回 open|filtered(开放或者被过滤的)。-sA (TCP ACK扫描)
这种扫描与目前为止讨论的其它扫描的不同之处在于 它不能确定open(开放的)或者 open|filtered(开放或者过滤的))端口。 它用于发现防火墙规则,确定它们是有状态的还是无状态的,哪些端口是被过滤的。
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -sA (1)"; fragbits:!D; dsize:0; flags:A,12; window:1024; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000538; classtype:attempted-recon; sid:2000538; rev:8; metadata:created_at 2010_07_30, updated_at 2010_07_30;) alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -sA (2)"; fragbits:!D; dsize:0; flags:A,12; window:3072; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000540; classtype:attempted-recon; sid:2000540; rev:8; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
可以通过修改 tcp window
-sV -sO
nmap使用-O参数扫描时会发送tcp,udp,icmp 然后在根据响应的tcp window,TTL,IPID等对比指纹库识别操作系统。
- ip_proto ip协议号 21
- content CCCCCCCCCCCCCCCCCCCC
alert ip $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -sO"; dsize:0; ip_proto:21; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000536; classtype:attempted-recon; sid:2000536; rev:7; metadata:created_at 2010_07_30, updated_at 2010_07_30;) alert udp $EXTERNAL_NET 10000: -> $HOME_NET 10000: (msg:"ET SCAN NMAP OS Detection Probe"; dsize:300; content:"CCCCCCCCCCCCCCCCCCCC"; fast_pattern:only; content:"CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC"; depth:255; content:"CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC"; within:45; classtype:attempted-recon; sid:2018489; rev:3; metadata:created_at 2014_05_20, updated_at 2014_05_20;) alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN NMAP -f -sV"; fragbits:!M; dsize:0; flags:S,12; ack:0; window:2048; threshold: type both, track by_dst, count 1, seconds 60; reference:url,doc.emergingthreats.net/2000545; classtype:attempted-recon; sid:2000545; rev:8; metadata:created_at 2010_07_30, updated_at 2010_07_30;)
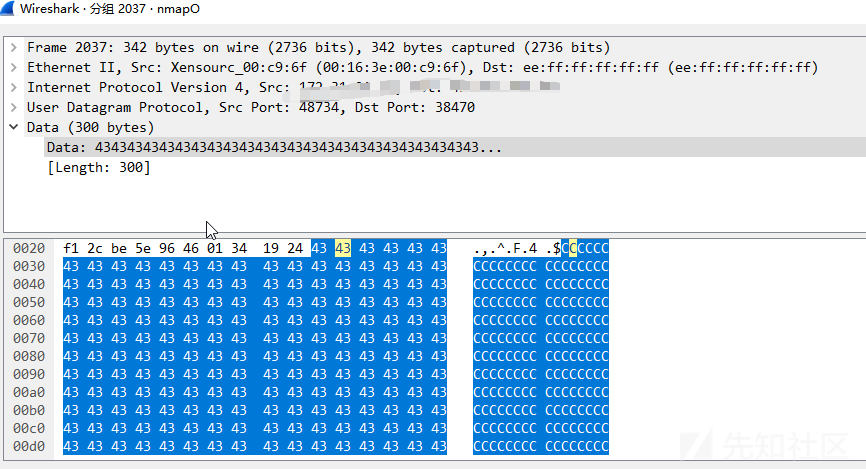
osscan2.cc
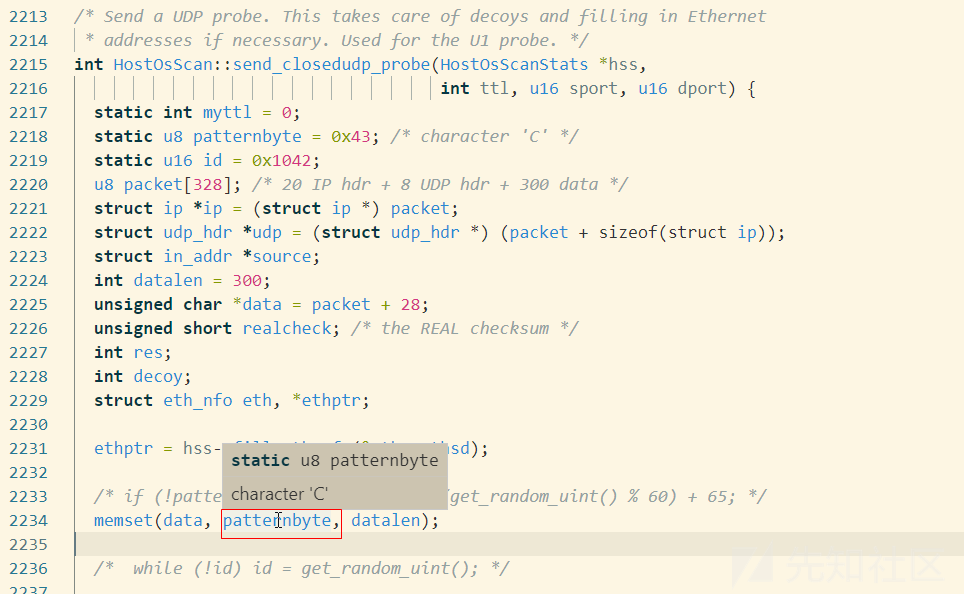
查看注释,发现 nbase\nbase_rnd.c有生成随机bytes的函数get_random_bytes,进行修改,随机生成填充。
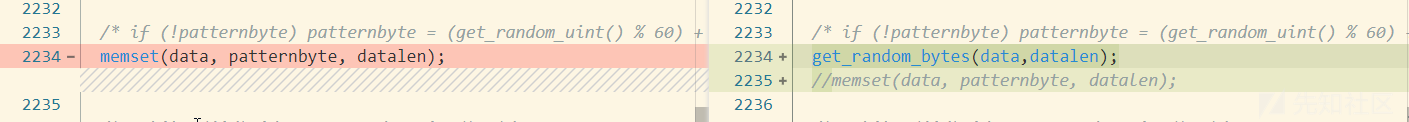

sip
alert tcp $EXTERNAL_NET any -> $HOME_NET $HTTP_PORTS (msg:"ET SCAN NMAP SIP Version Detect OPTIONS Scan"; flow:established,to_server; content:"OPTIONS sip|3A|nm SIP/"; depth:19; classtype:attempted-recon; sid:2018317; rev:1; metadata:created_at 2014_03_25, updated_at 2014_03_25;) alert tcp $EXTERNAL_NET any -> $HOME_NET 5060:5061 (msg:"ET SCAN NMAP SIP Version Detection Script Activity"; content:"Via|3A| SIP/2.0/TCP nm"; content:"From|3A| <sip|3A|nm@nm"; within:150; fast_pattern; classtype:attempted-recon; sid:2018318; rev:1; metadata:created_at 2014_03_25, updated_at 2014_03_25;)
替换nmap-service-probes中
nm@nm nm2@nm2 nmap 等关键词
scripts
alert http $EXTERNAL_NET any -> $HTTP_SERVERS any (msg:"ET SCAN NMAP SQL Spider Scan"; flow:established,to_server; content:"GET"; http_method; content:" OR sqlspider"; http_uri; reference:url,nmap.org/nsedoc/scripts/sql-injection.html; classtype:web-application-attack; sid:2013778; rev:2; metadata:created_at 2011_10_19, updated_at 2011_10_19;) alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN Nmap Scripting Engine User-Agent Detected (Nmap Scripting Engine)"; flow:to_server,established; content:"Mozilla/5.0 (compatible|3b| Nmap Scripting Engine"; nocase; http_user_agent; depth:46; reference:url,doc.emergingthreats.net/2009358; classtype:web-application-attack; sid:2009358; rev:5; metadata:created_at 2010_07_30, updated_at 2010_07_30;) alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"ET SCAN Nmap Scripting Engine User-Agent Detected (Nmap NSE)"; flow:to_server,established; content:"Nmap NSE"; http_user_agent; reference:url,doc.emergingthreats.net/2009359; classtype:web-application-attack; sid:2009359; rev:4; metadata:created_at 2010_07_30, updated_at 2010_07_30;) alert tcp any any -> $HOME_NET any (msg:"ET SCAN Nmap NSE Heartbleed Request"; flow:established,to_server; content:"|18 03|"; depth:2; byte_test:1,<,4,2; content:"|01|"; offset:5; depth:1; byte_test:2,>,2,3; byte_test:2,>,200,6; content:"|40 00|Nmap ssl-heartbleed"; fast_pattern:2,19; classtype:attempted-recon; sid:2021023; rev:1; metadata:created_at 2015_04_28, updated_at 2015_04_28;) alert tcp $HOME_NET any -> any any (msg:"ET SCAN Nmap NSE Heartbleed Response"; flow:established,from_server; content:"|18 03|"; depth:2; byte_test:1,<,4,2; byte_test:2,>,200,3; content:"|40 00|Nmap ssl-heartbleed"; fast_pattern:2,19; classtype:attempted-recon; sid:2021024; rev:1; metadata:created_at 2015_04_28, updated_at 2015_04_28;) alert http $HOME_NET any -> any any (msg:"ET SCAN Possible Nmap User-Agent Observed"; flow:to_server,established; content:"|20|Nmap"; http_user_agent; fast_pattern; metadata: former_category SCAN; classtype:web-application-attack; sid:2024364; rev:3; metadata:affected_product Any, attack_target Client_and_Server, deployment Perimeter, signature_severity Audit, created_at 2017_06_08, performance_impact Low, updated_at 2017_06_13;)
完成重新编译
./configure make make install /nmap# ./nmap -version Nmap version 7.70SVN ( https://nmap.org ) Platform: x86_64-unknown-linux-gnu Compiled with: nmap-liblua-5.3.5 openssl-1.0.2g nmap-libssh2-1.8.2 libz-1.2.8 nmap-libpcre-7.6 libpcap-1.7.4 nmap-libdnet-1.12 ipv6 Compiled without: Available nsock engines: epoll poll select
如有侵权请联系:admin#unsafe.sh