Installation of GCP Inspector and basics about enumerating publicly exposed GCP buckets.While playin 2021-08-11 05:17:33 Author: infosecwriteups.com(查看原文) 阅读量:30 收藏
Installation of GCP Inspector and basics about enumerating publicly exposed GCP buckets.

While playing Thunder CTF I created a simple python tool that can audit publicly accessible GCP storage buckets.
Thunder CTF allows players to practice attacking vulnerable cloud projects on the Google Cloud Platform (GCP) environment. At each level, players are tasked with exploiting a cloud deployment to find a “secret” integer stored within it.
This blog also walks you through install GCP Inspector which is a python tool For enumerating publicly accessible GCP Buckets.

Assumptions
- Already have the list of GCP buckets.
- Already have GCP console access (shell) with a billing account.
- ‘gsutil’ installed on the local.
- Access to the list of buckets from the environment which needs to be audited. This requires default scope: https://www.googleapis.com/auth/devstorage.full_control . This will give list access to all the buckets for given project.
These buckets can be saved in the file.txt for later use in the GCP Inspector.
1. Open the shell of audit environment.
2. Run gcloud config set project [PROJECT_ID]
3. gsutil lsSteps To Enumerate GCP Bucket
- Install python3 and gsutil via
python3 -m pip install gsutil. - Log in to another GCP account (external attacker). This will be required after running gsutil config.
- Configure the terminal to use gsutil via
gsutil config. If not configured or the credentials are expired then it will show an error.

4. Authenticate the GCP and complete the required details like authorization code, etc.
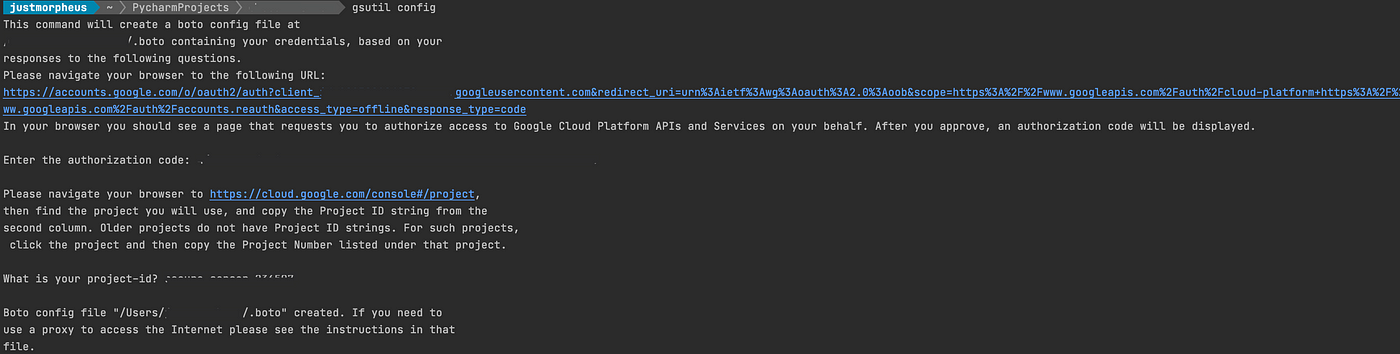
5. Once complete we are good to go, run the below-mentioned commands to activate virtual-env and run the GCP Inspector.
git clone https://github.com/justmorpheus/GCP-Inspector
cd GCP-Inspector
mkdir gcp_inspect
virtualenv -v gcp_inspect
source gcp_inspect/bin/activate
python3 -m pip install -r requirements.txt
python3 gcp_inspector.py -r sample_file.txt6. Sample_file.txt is the file with GCP buckets saved from the audit environment.

Reference Commands For Google Storage
- The command for copying GCP public bucket data to local:
gsutil cp -r gs://[BucketName] .2. The command to list the total size of files in a bucket (human-readable).
gsutil du -h gs://[BucketName]3. The command to preview a file in Google Cloud Storage.
gsutil cat gs://[BucketName]/folder/filename4. Accessing publicly accessible GCP Bucket via an endpoint.
http://BUCKET_NAME.storage.googleapis.com/OBJECT_NAMEor http://storage.googleapis.com/BUCKET_NAME/OBJECT_NAME
Finally, we can run grep or any other tool for finding secrets and any other critical data inside the google storage.
Note: This is an audit tool for checking publicly exposed GCP Buckets in the GCP environment.
Honourable Mentions
- https://docs.google.com/presentation/d/1R7mSTbra24z5uj9N6botjkaXuneSvVV6AK5siKnFrcw/htmlpresent
- https://github.com/clario-tech/s3-inspector
- https://github.com/NicholasSpringer/thunder-ctf
Disclaimer: Do not perform the scan on the production environment without the prior consent of the owners. All information provided is for educational purposes only.

如有侵权请联系:admin#unsafe.sh