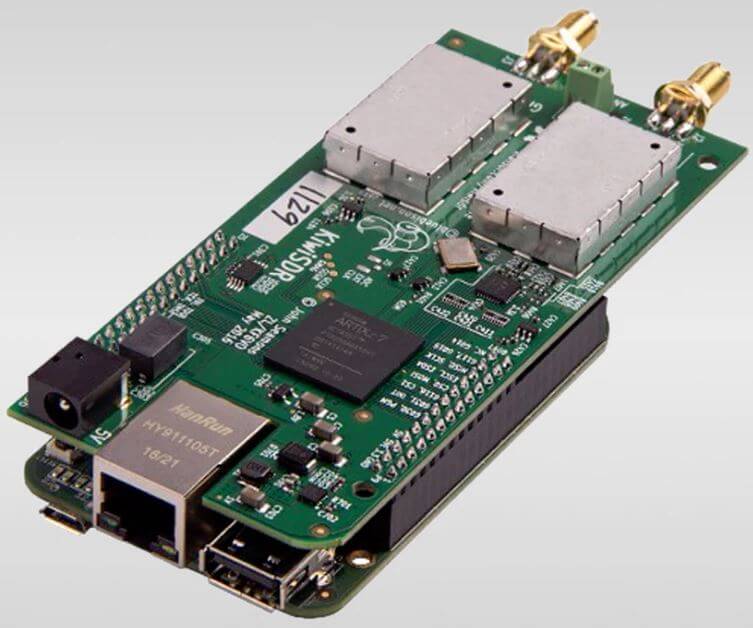
Since it's announcement in early 2016 we've posted many times about the KiwiSDR, a 14-bit wideband RX only HF software defined radio created by John Seamons (ZL/KF6VO). The KiwiSDR has up to 32 MHz of bandwidth, so it can receive the entire 10 kHz - 30 MHz VLF/LF/MW/HF spectrum all at once.
Compared to most other SDRs the KiwiSDR is a little different as it is designed to be used as a public web based SDR, meaning that KiwiSDR owners can optionally share their KiwiSDR online with anyone who wants to connect to it. The public functionality allows for some interesting distributed applications, such as TDoA direction finding, which allows users to pinpoint the location of unknown HF transmissions such as numbers stations.
In order to implement this online capability, the KiwiSDR runs custom open source software on a Beaglebone single board computer which connects to your home network. Recently there has been vocal concern about a security flaw in the software which could allow hackers to access the KiwiSDR. The flaw stems from the fact that the KiwiSDR has 'backdoor' remote admin access that allows the KiwiSDR creator to log in to the device and troubleshoot or make configuration changes if required. This backdoor has been public knowledge in the KiwiSDR forums since 2017, although not advertised and explicit consent to have it active and used was not required.
Interesting post on the KiwiSDR forums. Seems to imply the KiwiSDR author has remote access to all KiwiSDRs? Post has since been modified to remove the last paragraph and the thread locked :-/ https://t.co/cAi5dS7J49 pic.twitter.com/elqSsaUJ65
— Mark Jessop (@vk5qi) July 14, 2021
The intent of the backdoor is of course not malicious, instead rather intended as an easy way to help the creator help customers with configuration problems. However, as KiwiSDR owner Mark Jessop notes, the KiwiSDR operates in HTTP only, sending the admin master password in the clear. And as KiwiSDR owner and security researcher @xssfox demonstrates, the admin page gives full root console access to the Beaglebone. These flaws could allow a malicious party to take over the Beaglebone, install any software and perhaps work their way onto other networked devices. Another tweet from xssfox implies that the password hashes are crackable, allowing the main admin password to be easily revealed.
— xssfox (@xssfox) July 15, 2021Quick video showing how the backdoor on the kiwisdr works.
I've also tested that touch /root/kiwi.config/opt.no_console mitigates the issue
Thanks @the6p4c for helping me test :) pic.twitter.com/0xKD1NfvwL
Creator John Seamons has already released a patch to disable the admin access, and as of the time of this article 540 out of 600 public KiwiSDRs have already been auto-updated. Owners of KiwiSDR clones should seek out updates from the cloner.
It is clear that the KiwiSDR is a passion project from John who has dedicated much of his time and energy to consistently improving the technical RF engineering side of the device and software. However we live in an age where malicious hacking of devices is becoming more common, so anyone releasing products and software that network with the internet should be reminded that they have a responsibility to also dedicate time to ensuring security.
John has reached out to us in advance and noted that he currently cannot yet comment publicly on this topic due to legal advice.