
5 Steps to SASE Virtual Series: Step 5 July 7
Step 5 in our #5steps2sase series and part of our ongoing thread about SASE.
To round out our #5steps2sase series, we’re looking at one of the less commonly discussed techniques that is quickly becoming the lynchpin of the next generation of cybersecurity: continuous monitoring of how people use data. While just about all SASE solutions focus on securing access to data, very few go beyond giving lip service to protecting data once it’s been downloaded. As we discussed in part 3 of our series, Safeguarding the Usage of Data Everywhere, that leaves data exposed to theft or misuse. On July 7, I'll have the privilege to sit down with Sean O’Sullivan, one of Forcepoint’s global experts on data protection and insider risk solutions, to talk about how behavioral intelligence is closing this vulnerability and changing the way cybersecurity is done.
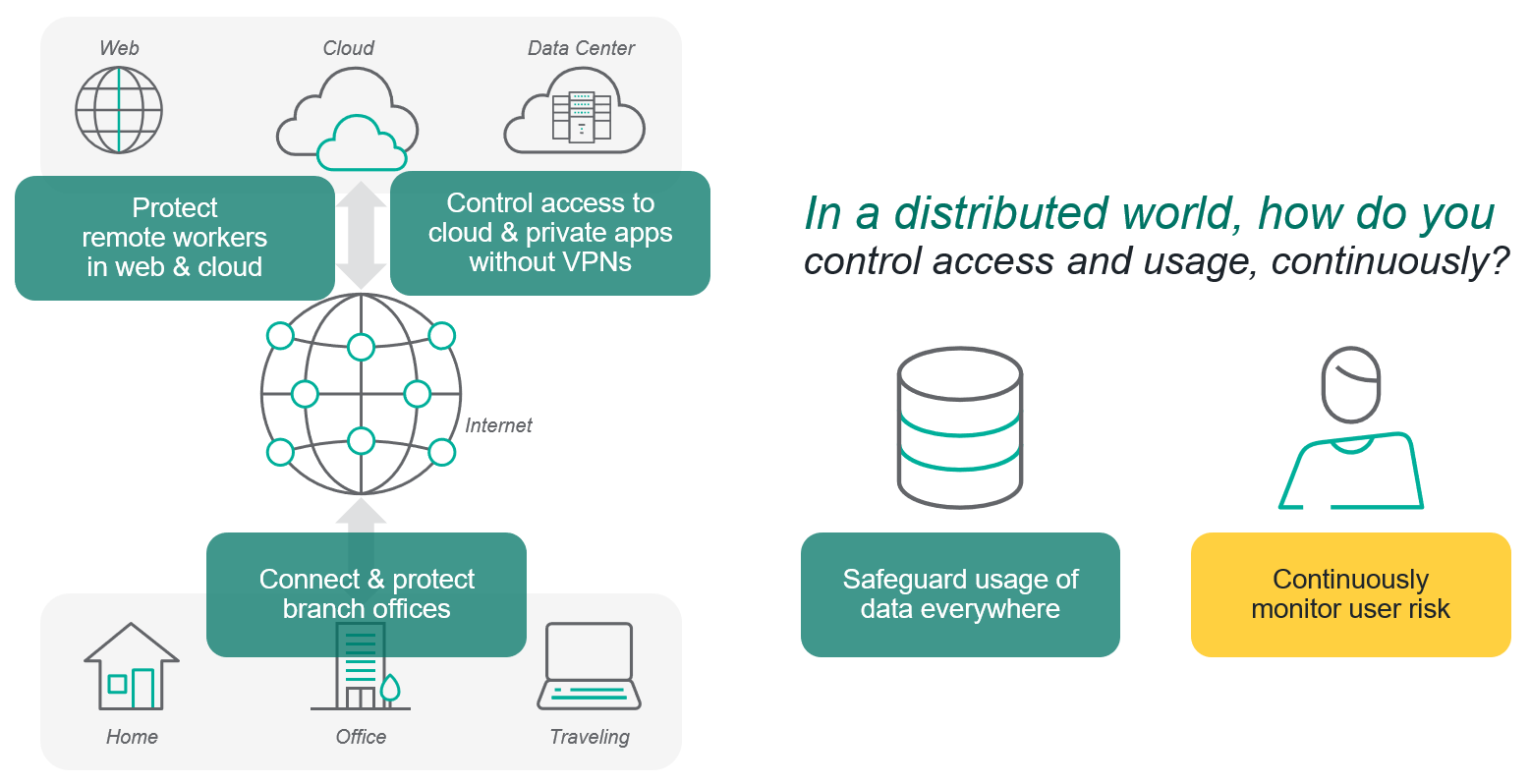 Forcepoint sees SASE as the best way to deliver enterprise-class data protection based on Zero Trust principles to everywhere people are working and over whatever channels of communication they are using. What makes our SASE platform “data-first” is the way it makes sure that organizations can retain control over how data that has been downloaded from business applications is used. This is in line with the US National Institute of Standards and Technology’s (NIST) Special Publication 800-207 on Zero Trust that specifically talks about the importance of continuously monitoring and controlling how people use resources.
Forcepoint sees SASE as the best way to deliver enterprise-class data protection based on Zero Trust principles to everywhere people are working and over whatever channels of communication they are using. What makes our SASE platform “data-first” is the way it makes sure that organizations can retain control over how data that has been downloaded from business applications is used. This is in line with the US National Institute of Standards and Technology’s (NIST) Special Publication 800-207 on Zero Trust that specifically talks about the importance of continuously monitoring and controlling how people use resources.
Sean and I will talk about how examining users’ behavior across many different systems enables cybersecurity to operate more like security in the real world. It frees organizations from having to choose between overly simplistic “always allow or always block” or overly complicated policies that try to encompass the exponential combination of users, applications, places, times, and many other factors. Instead, behavior-based systems enable you to trust your employees, keeping security out of the way so that they can get their jobs done. Then, if someone starts making mistakes or demonstrating potentially malicious behavior, the system can automatically apply tighter progressively controls. This new approach protects productivity and ensures that the harshest measures are only applied in the specific circumstances that merit them. That’s what Data-first SASE is all about.
As always, no slides, just a good conversation. We hope you enjoy it as well. Register for the step 5 conversation today.
Forcepoint is the leading user and data protection cybersecurity company, entrusted to safeguard organizations while driving digital transformation and growth. Our solutions adapt in real-time to how people interact with data, providing secure access while enabling employees to create value.

Jim Fulton
Jim Fulton is Forcepoint’s Senior Director of Product Marketing, focused on Data-first SASE and Zero Trust Data Protection solutions. He has been delivering enterprise access and security products for more than 20 years and holds a degree in Computer Science from MIT.
