

Introduction: My name is Kabir Suda alias MR-SINISTER, mrsinister1501 or mrsinister15 and welcome to my third blog. This is about different types of dorking in bug bounties to get more information about your targets, find leaked information and basically just more Recon. This write-up will shed light mainly to Shodan Dorking.
Feel free to shoot me a DM on my Twitter account!
Join my Discord server- Hack The Planet
Join a super active and helping server- Bounty Hunters
I am very active in both of them, you can ping me anytime and anywhere :)
(1) Google Dorking
(2) Shodan Dorking
(3) Github Dorking
1) Google Dorking:

Google is a powerful tool. It is available for anybody with an internet connection. It is massive.
Google Dorking is basically searching through the internet to attain the desirable information with the help of some queries or dorks. This will help you find whatever you want from the deep cracks of the internet!
How to Google Dork?
Google Dorking is actually really simple. You just need to know some basics about the dorks that can get you the information you want.
This is a really basic and simple Google Dork that can find you login pages:
site:target.com intext:login intext:username intext:password
If the scope of your program has*.target.com then you should add a “*.” in the dork like so:
site:*.target.com
This will fetch you login pages from all of the subdomains of target.com listed on the internet.
This has information about most google dorks- Google Dorking Cheatsheet
- You should start small and then slowly build your dork depending on the search results. Eg-
site:target.com intext:Logingives a login page that has nothing interesting again and again. You should add some more specific words to your query. Eg-site:target.com intext:Login intitle:Jira - You should add the operator
-in your query if you want to remove something specific from your result. Eg-site:target.com intext:Login
gives login errors in the result. Then you should use-to remove the word “error” from the result like so:site:target.com intext:Login -errorSimilarly, if you use the operator+you can add specific words to your query.site:target.com intext:Login -error +username
Also, you should useextfor specifying the extension. Eg-site:target.com intext:Login -error +username ext:php - Check out the Google-Hacking-Database which has a lot of google dorks which you can use for reference.
Resources for Google Dorking
1) The Google Hacking Database contains a lot of ready-made google dorks that can find vulnerabilities or signs of a CVE.
2) A Google Dorking cheatsheet with a lot of information about the most basic dorks.
3) List of a number of useful Google Dorks.
4) YouTube Videos.
5)There are several tools available like Dorks-eye.
Some Dorks to find something juicy with Google:
Dork to find Admin Panels:
site:"*.target.com" intitle:admin intext:login intext:username | email intext:password -help -docs -support -news
Dork to find PII:
site:"*.target.com" intext:"phone"|number intext:"email"|address intext:"personal" intext:address intext:name|last -support -news -vendor -docs -help
2) Shodan Dorking:
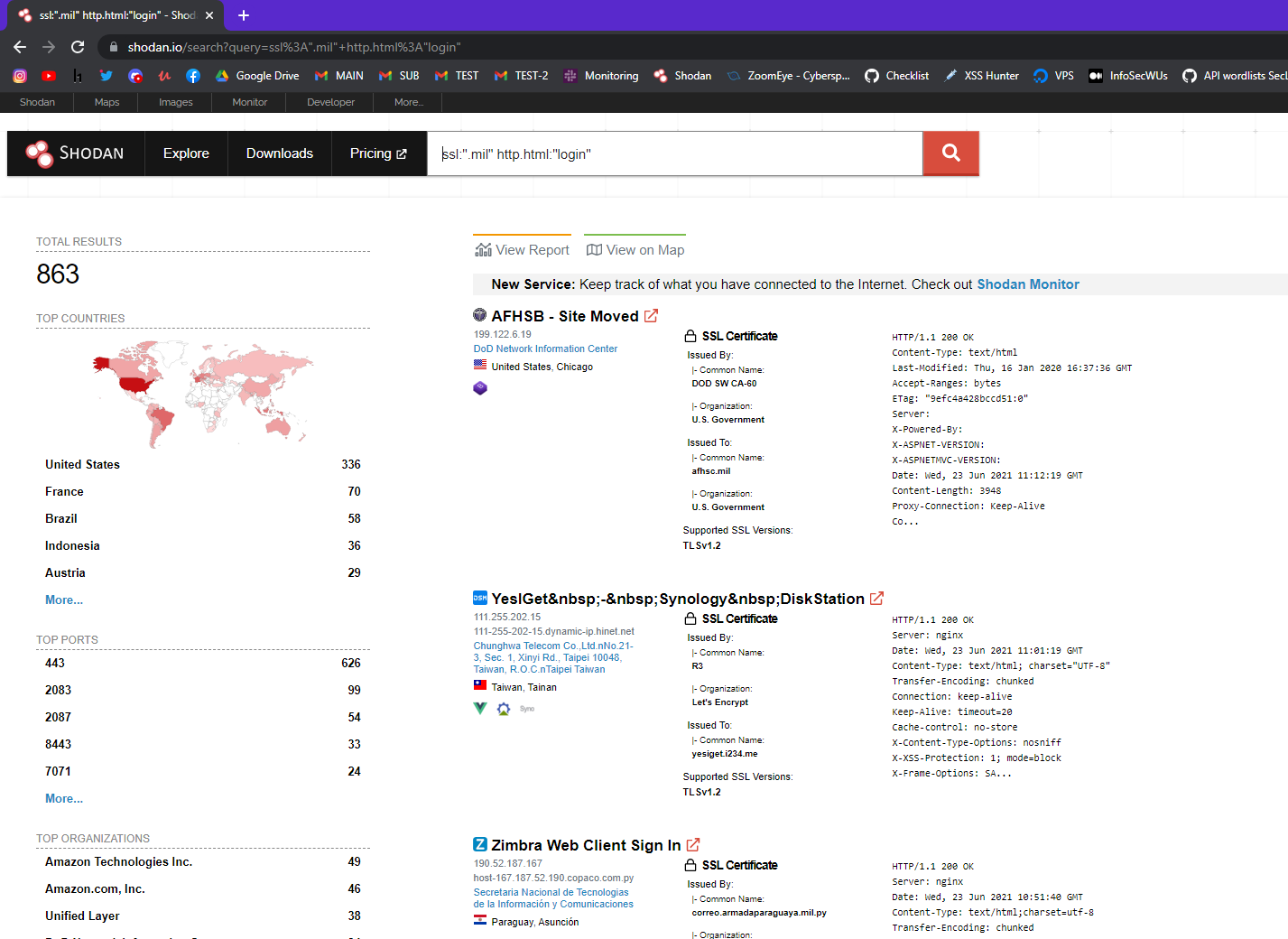
Shodan is a massive platform that gives information about all devices connected to the internet! This is my personal favorite. We can dork more, we can get more information and if you buy the subscription you can query with Shodan all day long without any warnings!
How to use Shodan for Dorking?
This is a bit harder than Google Dorking, but I believe it is more rewarding.
It is a bit similar to Google Dorking though.
A really basic and simple Shodan dork:
ssl:"target.com" http.html:"Login, username, password"
You can use “*.” in this one as well, but it really doesn’t matter to Shodan.
Why is Shodan better than Google for dorking?
According to me, it is much better because Shodan gives you all of the machines running that match your query along with open ports, services and the SSL certificate!
- Checkout some useful Shodan Dorks for reference here.
- In Shodan, if you want to remove some results you can use this
“-http.html:SOMETHING_TO_REMOVE” Eg:ssl:"target.com" http.html:"Login, username,password" -http.html:"403 Forbidden" - The dork “http.html” is not the only way to work with Shodan!
You can usehttp.title:"Admin"to finds results with title. This works like the google dorkintitle. - “http.html” searches the provided keyword in the entire html page and returns only those machines/ips/domains that have that particular word in their HTML Page!
- Use ports for searching too!
Eg-ssl:"target.com" port:"2082"This query should give you all hosts that have services running on port 2082 which is usually a cPANEL port. - You can do so much more! Like adding different organizations in your query to get those hosts who have that instance running!
Eg-ssl:"target.com" org:"Cloudflare, Inc."
I don’t usually guess, or put Cloudflare by default. I first just search forssl:"target.com"and then in the left hand side I get all of the available organizations, you should just click on them rather than type them out. - Just like organizations, you can filter with products! Like
ssl:"target.com" product:"nginx"You will find these products in the left hand side as well. - The
sslflag searches for the domain or keyword provided in the SSL Certificate. You can also put words like-targetcompanyin the ssl flag instead of a domain for different or more results. - The
sslflag is NOT the limit! You can use a popular dork like-orgas well for different results. This will give you all of the hosts running with that organization. When you check the whois data of a target, you see the organization right? Thisorgdork searches by that only! - You can also search by the status codes like so:
ssl:"target.com" org:"Cloudflare, Inc." product:"nginx" 200Just by typing “200” you will get the requests of the hosts with “200” in it. Shodan will search for 200 in the request and most probably it is the status code, so you will get the results of hosts with the status 200. - Shodan has a limit for queries. So you can’t just go try different queries forever with one account! You will need to get the Shodan subscription which is paid. But it is worth it!
Note: These are not ALL of the Shodan tips and tricks, I just shared some that can help you with bug bounties. Shodan is much more than just this. You can search for CVEs with Shodan too. For example, if a specific URL is vulnerable to XSS according to a CVE, you can just paste that URL in Shodan and include your target by ssl or by org. This way, you can easily find and exploit a CVE using Shodan.
Resources for Shodan Dorking:
- Find Some Shodan Dorks here.
- This blog by Security Trails.
- Some great YouTube Videos.
- A browser extension for Shodan.
- More Shodan Dorks and Queries here.
- A tool for Shodan(Although manual Shodan Dorking is the best)
PS- I was paid out for reporting a bug in the start of June that I found by Shodan Dorking:

Dork to find something Juicy with Shodan:
ssl.cert.subject.CN:"*.target.com" http.html:"Log in, username, password" http.title:"Admin" 200 http.html:"Test, news, support"
3)GitHub Dorking

GitHub Dorking is basically finding leaks in the code pushed by the target organization or its employees and the last topic that I’ll be covering in this write-up.
GitHub like Shodan and Google also contains leaks, hence more attack surface for Bug Hunters! :)
How to GitHub dork?
There are basically four main parameters that you need to specify while Github Dorking:
1) Specify a target, and always use double quotes as best practice. Eg “target.com”
2) Specify a Keyword that you want to Dork for. Eg: “password” or “secret”
3) Specify a language. This means, the programming language.Eg:language:"bash"`
4) Specify the keywords that you don’t want to see in the response:org:targetCompany language:"bash" "password" "secret" NOT test
When you dork, always click on the “Code” tab. Most of the leaks are found here from the dorks you use.
There are 2 basic approaches for GitHub Dorking:
1) Using the org flag. This way, you will only see code that was published by the organization itself and no one else. Using this, you can never go out of scope. But this doesn’t have much scope either, because the organization doesn’t push too much code itself.
2) Don’t use the org flag at all. Use this instead- "target.com" <the rest of your dork here> . This way, you will find more leaks. But at the same time, there is scope for the results being out of scope for your program. So it would be the best to test the leaks you find and verify them :)
Eg: "target.com" language:"bash" "password" "secret" NOT test
These are some Keywords you should use while GitHub Dorking:
Jenkins
Jira
OTP
oauth
authoriztion
password
pwd
ftp
ssh
dotfiles
JDBC
token
user
pass
secret
SecretAccessKey
AWS_SECRET_ACCESS_KEY
credentials
config
security_credentialsWhat to do if I still can’t find leaks? You do this:) -
SECRET GITHUB DORKING METHODOLOGY UNRAVELLED! 🤫1. When you go to do Github Dorking, what is the first thing you do?
==> You find your target's Github Page.2. Then 50% of the time, you won't find leaks on their main github page, are there any other in-scope pages for github dorking?
==> Yes! When you go to the target's github page, if you scroll down you will see a tab called People.
It has the employees that are officially working with your target.3. Now from the People tab go to any employee's github page.
==> All of the Employees mentioned in the People tab are in-scope for Github dorking! How cool is that?! You just got more attack surface!Now remember that these employees have a life other than working for your target.
Means they can push sensitive leaks but they might be of the employee's private project.(maybe his personal projects)
So don't get too hyped when you see a leak by an employee, try to verify that it is information for your target, and not an external/private project of the employee.4. The best tip:Sometimes you wont be able to find leaks by the employees in the People tab, don't worry there is still a little something to get you more attack surface :)==>
Fact- If any of the employees have leaked sensitive information in their Github Repo which is related to the company, that's a bug!Now we are gonna find the external yet still in-scope employees :)
Use this google dork-site:linkedin.com intext:software engineer at TargetORGThis will find you employees that work for your target company, but still are not listed in People tab. Why? ==>
Maybe because they are meant to kept secret and they post sensitive stuff... You never know. Now that you found some more employees, you will find their Github Pages. Usually all Software engineers have a github page.
To find their Github page use this google dork:site:github.com intext:the_employee_here
or simply search "github the_employee_here"Now you got a lot of stuff to github dork to! Now you might actually find leaks!!
Dork to find some Juicy leaks using Github:
"target.com" language:python "secret" "password" "key" NOT support NOT docs NOT sandbox NOT docker NOT container NOT test NOT fake
I hope, I have explained a ton of Dorking now. With this I would like to end this blog. If you read it this far, then thanks! I hope you learned something!!
Regards,
MR-SINISTER
如有侵权请联系:admin#unsafe.sh