Introduction to SocialPhish – An Open-Source Phishing ToolkitIn the fol 2021-06-15 22:32:45 Author: www.vmray.com(查看原文) 阅读量:152 收藏
Introduction to SocialPhish – An Open-Source Phishing Toolkit
In the following Malware Analysis Spotlight, we will take a look at phishing campaigns that are likely generated by abusing an open-source phishing toolkit – SocialPhish. SocialPhish’s README states that at least some of its phishing templates were generated by SocialFish (another phishing tool with a very similar name) which is able to clone a target website. We’ll see that based on the generated templates, we can find a link to many other derivative phishing kits (some of them also open source). SocialPhish being a project hosted on Github makes it very easy to reuse and abuse. Threat actors can directly grab it, integrate into their own tools, and use it for nefarious purposes. From our observations, at the very least the templates are still being actively used to generate phishing pages for social media platforms.
Recently, we’ve mostly observed it being used to target Instagram and Protonmail, but the kit includes templates for over 30 platforms including such as Facebook, Google, Snapchat, Github, Yahoo, Spotify, Netflix, Linkedin, WordPress, and Microsoft. In this blog post, we are going to look at how VMRay Analyzer is able to detect and stop such phishing attempts before any harm is done.
SocialPhish’s server-side files are kept simple. They are only responsible for collecting the IP address, user agent, and browser of the connecting user and saving it together with the harvested credentials to a local file (Figure 2). When those tasks are finished, the user is redirected to the official page, e.g., of Instagram, and is led to believe that the password was typed incorrectly. Interestingly, we found multiple kits that can be linked based on the phishing templates found in SocialPhish (Figure 3). Some of those were integrated into different tools that provide more than just phishing capabilities. Some of those tools contain backdoor code.
SocialPhish Analysis
The VMRay Analyzer is able to detect the phishing attempt and return a malicious verdict (Figure 4). It also provides a phishing kit-specific detection, as well as a heuristic-based approach.
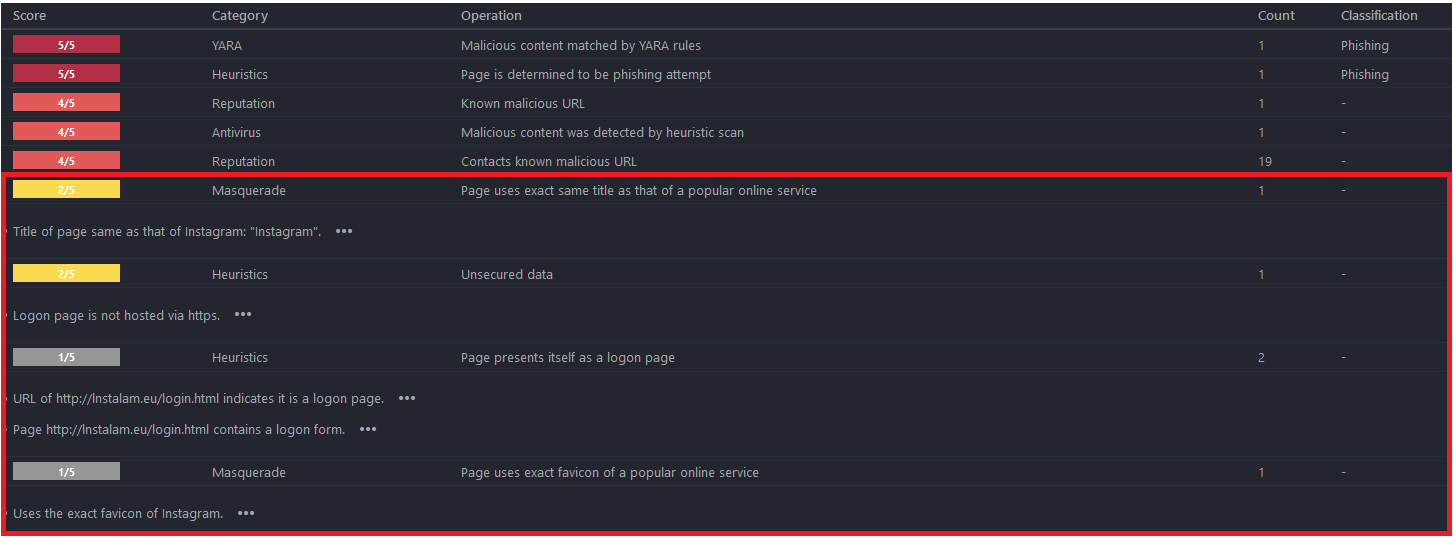
VMRay Analyzer’s heuristic detection manages to determine that the page is trying to impersonate the official Instagram login page. From the matched VTIs, we can confirm, that it uses the exact same page title and favicon, but the data is sent over an unsecured channel, i.e., there is no SSL/TLS encryption (Figure 5). Combining multiple detections, it’s able to determine, that the presented webpage is masquerading as Instagram and is in fact a phishing attempt.
During analysis, all the related requests and downloaded resources are scanned and analyzed for any suspicious content or behavior. The sequential behavior can be followed in the Behavior Tree. It allows an analyst to group each stage of a phishing attack and work on the specific part. This can be especially useful when a phishing page also tries to collect additional data, like credit card information, besides the initial login credentials. We can also observe that in this case a YARA rule matched and was able to associate it with a phishing kit. In our analysis, we determined this to be either SocialFish or one of its many derivatives (Figure 6). This is also the tool that SocialPhish uses to generate its templates.
Figure 6: VMRay Analyzer – YARA matching a specific threat (top) and the Behavior Tree displaying the requests and resources (bottom).
The analysis also produces actionable IOCs which can be directly used to enhance any existing detection tools (Figure 7).
Conclusion
Phishing is becoming one of the most common cybercrime. According to Verizon’s 2021 Data Breach Investigations Report (DBIR), 43% of breaches involved phishing. Many organizations and individuals around the world are being targeted by the constantly increasing amount of phishing campaigns. A good understanding of the phishing landscape is critical. With VMRay Analyzer’s capabilities to detect suspicious URLs based on many different indicators and heuristics, an organization is able to prepare and protect itself and its employees. Future attacks can be detected and mitigated before they cause any harm.
SocialPhish – IOCs
hxxp://lnstalam[.]eu/index_files/sdk.js.download hxxp://lnstalam[.]eu/index_files/b67d172d5783.js.download hxxp://lnstalam[.]eu/login.html hxxp://lnstalam[.]eu/index_files/96f2557117a2.js.download hxxp://lnstalam[.]eu/index_files/8e2c2a606042.js.download hxxp://lnstalam[.]eu/index_files/2d9d7248af43.jpg hxxp://lnstalam[.]eu/index_files/aafd8c6b005d.jpg hxxp://lnstalam[.]eu/index_files/629d23a3c7b2.jpg hxxp://lnstalam[.]eu/index_files/001bc33056c1.jpg hxxp://lnstalam[.]eu/index_files/4b70f6fae447.png hxxp://lnstalam[.]eu/index_files/f5ae123ab1e2.jpg hxxp://lnstalam[.]eu/index_files/f06b908907d5.png hxxp://lnstalam[.]eu/index_files/d1f0f06b39df.js.download hxxp://lnstalam[.]eu/index_files/f9e5c0ca0804.js.download hxxp://lnstalam[.]eu/index_files/f55c258e826e.png hxxp://lnstalam[.]eu/static/images/homepage/home-phones.png/38825c9d5aa2.png hxxp://lnstalam[.]eu/index_files/fb48443ec9d3.png hxxp://lnstalam[.]eu/index_files/login.html hxxp://lnstalam[.]eu/static/images/homepage/home-phones.png/login.html hxxp://lnstalam[.]eu/index_files/lY4eZXm_YWu.html
如有侵权请联系:admin#unsafe.sh