2021-06-03 19:00:26 Author: securelist.com(查看原文) 阅读量:119 收藏
Introduction
In a nutshell, email spoofing is the creation of fake emails that seem legitimate. This article analyzes the spoofing of email addresses through changing the From header, which provides information about the sender’s name and address.
SMTP (Simple Mail Transfer Protocol, the main email transmission protocol in TCP/IP networks) offers no protection against spoofing, so it is fairly easy to spoof the sender’s address. In fact, all the would-be attacker needs is a tool for choosing in whose name the message will arrive. That can be another mail client or a special utility or script, of which there is no shortage online.
Email spoofing is used in both fraudulent schemes and targeted attacks against organizations. Cybercriminals use this technique to convince victims that a message came from a trusted sender and nudge them into performing a specific action, such as clicking a phishing link, transferring money, downloading a malicious file, etc. For added credibility, attackers can copy the design and style of a particular sender’s emails, stress the urgency of the task, and employ other social engineering techniques.
In some cases, fake emails form part of a multistage attack, the first phase of which requires no suspicious actions on the part of the victim. For examples of such attacks, see our article on corporate doxing.
Legitimate Domain Spoofing
The simplest form of the technique is legitimate domain spoofing. This involves inserting the domain of the organization being spoofed into the From header, making it extremely difficult for the user to distinguish a fake email from a real one.
To combat spoofing, several mail authentication methods have been created that enhance and complement each other: SPF, DKIM and DMARC. By various means, these mechanisms verify that the message was actually sent from the stated address.
- The SPF (Sender Policy Framework) standard allows a mail domain owner to restrict the set of IP addresses that can send messages from this domain, and lets the mail server check that the sender’s IP address is authorized by the domain owner. However, SPF checks not the From header, but the sender’s domain specified in the SMTP envelope, which is used to transmit information about the email’s route between the mail client and the server, and is not shown to the recipient.
- DKIM solves the problem of sender authentication by means of a digital signature generated on the basis of a private key stored on the sender’s server. The public key for authenticating the signature is placed on the DNS server responsible for the sender’s domain. If in reality the message was sent from a different domain, the signature will be invalid. However, this technology has a weakness: an attacker can send a fake email without a DKIM signature, and the message will be impossible to authenticate.
- DMARC (Domain-based Message Authentication, Reporting and Conformance) is used to check the domain in the From header against a DKIM/SPF-validated domain. With DMARC, a message with a spoofed legitimate domain fails authentication. However, if the policy is strict, DMARC can also block wanted emails (see here for how our solutions augment this technology and minimize false positives).
Naturally, with the widespread implementation of the above-described technologies, attackers faced a tough choice: to hope that the company they are impersonating did not configure mail authentication properly (still common, sadly), or to use From-header spoofing methods that bypass authentication.
Display Name Spoofing
The display name is the name of the sender that gets shown in the From header before the email address. In the case of corporate mail, it is usually the real name of the relevant individual or department.
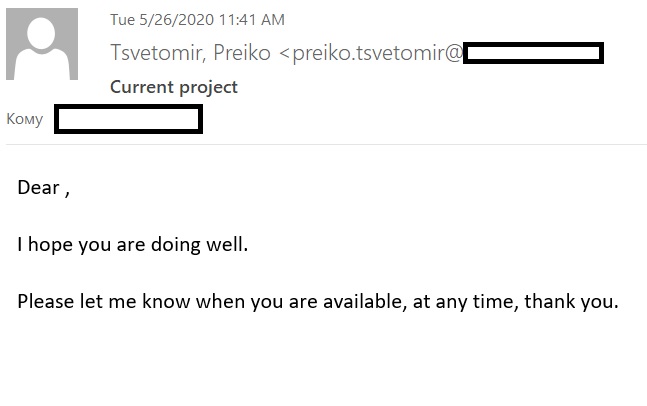
Example of a display name
To make the email less cluttered for the recipient, many mail clients hide the sender’s address and show only the display name. This allows cybercriminals to substitute the name, but leave their real address in the From header. And this address is often protected by a DKIM signature and SPF, so the authentication mechanisms see the message as legitimate.
Ghost Spoofing
The most common form of the above method is known as ghost spoofing. Here, the attacker specifies as the name not only the name of the person or company being spoofed, but also the address of the supposed sender, as in the example in the screenshot below.
Example of ghost spoofing
In actual fact, the message comes from a completely different address.
Real sender address in ghost spoofing, and mail authentication.
AD Spoofing
AD (Active Directory) spoofing is another form of display name spoofing, but unlike the ghost version, it does not involve specifying the spoofed address as part of the name. What’s more, the address from which the cybercriminals send messages features the name of the person being imitated.
Example of AD spoofing
This method looks more primitive than ghost spoofing, but some scammers prefer it for several reasons. First, if the recipient’s mail agent does display the contents of the From header in its entirety, the double sender address will make the user more suspicious than the address on the public domain. Second, ghost spoofing is technically easier to block with spam filters: it is enough to consign to the spam folder emails where the displayed sender name contains the email address. It is not generally feasible to block all incoming emails sent from addresses with the same names as colleagues and contractors.
Lookalike Domain Spoofing
More sophisticated attacks use specially registered domains, similar to the domain of the target organization. This requires a bit more effort, since finding and buying a specific domain, then setting up mail, DKIM/SPF signatures and DMARC authentication on it, is rather more difficult than simply modifying the From header slightly. But it also complicates the task of recognizing a fake.
Primary Lookalike
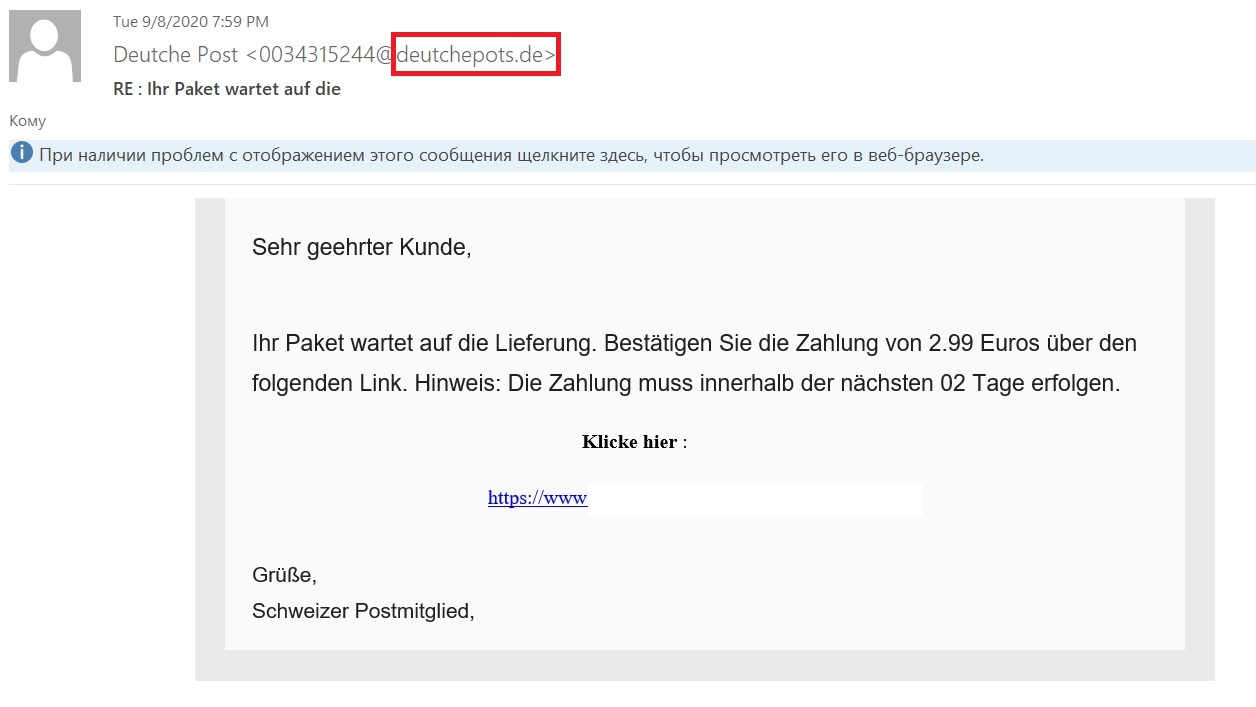
A lookalike domain is a domain name that looks similar to that of the organization being spoofed, but with a couple of alterations. We discussed such domains in detail in our article Lookalike domains and how to outfox them. For example, the email in the screenshot below came from the domain deutschepots.de, which can easily be confused with the domain of the German mail company Deutsche Post (deutschepost.de). If you follow the link in such an email and try to pay for delivery of a parcel, you will not only lose 3 euros, but also hand your card details to the fraudsters.
Example of a message from a lookalike domain
However, with the right level of vigilance, it is possible to spot misspelled domains. But in other cases, simple attentiveness is no longer sufficient.
Unicode Spoofing
Unicode spoofing is a type of spoofing in which an ASCII character in the domain name is replaced with a physically similar character from the Unicode set. Understanding this technique requires knowledge of how domains that use non-Latin characters (for example, Cyrillic or umlauts) are encoded. To use them, Punycode was created — a method that converts Unicode characters to an ASCII Compatible Encoding (ACE) representation, consisting of letters of the Latin alphabet, hyphens and numbers from 0 to 9. At the same time, many browsers and mail clients display the Unicode version of the domain. For example, this Russian domain:
is converted to:
xn--80akjebc7ajgd.xn--p1ai |
However, in the browser you will most likely see that same касперский.рф. Since this technology provides for partial encoding (individual characters are encoded, not the whole string), the domain can contain both ASCII and Unicode characters, which cybercriminals actively utilize.
Example of an email with Unicode spoofing
In the screenshot above, we see a message supposedly sent from the domain apple.com. It looks legitimate, and the email passed mail authentication. The email design is unusual, but since the average user rarely receives messages about blocking, there is little by way of comparison. If an unsuspecting user clicks the link, they are taken to a fake site that asks for their account details.
A look at the message headers (which can be done in most mail clients for PC and web versions of mail services) shows a completely different picture:
Punycode domain record
The fact is that the apple.com domain we saw above would look very different in Punycode, since the first three characters are in fact the Cyrillic letters “а” and “р”. But the mail client that opened the email converted that Punycode representation into Unicode for the convenience of the user, and the message displayed “apple.com”.
It should be noted that some mail clients warn the user about non-standard characters used in the domain name, or even display Punycode in the From header. However, such protection mechanisms are not universal, which plays into the hands of fraudsters.
Conclusion
There are various ways to convince the recipient of an email that it came from a trusted sender. Some of them seem primitive, yet they enable cybercriminals to successfully bypass mail authentication. At the same time, the technique of spoofing is used to carry out various types of attacks, from standard phishing to advanced BEC. They, in turn, can be just one step in a more sophisticated targeted attack. Accordingly, the damage from spoofing, even if restricted to a single attack, can range from identity theft to business downtime, loss of reputation and multi-million dollar losses.
There is also a variety of anti-spoofing protection methods, from simple (but not very reliable) vigilance to special components in business solutions. Kaspersky solutions for mail servers running on Microsoft Exchange, and Linux and in virtual environments contain such a module, plus we offer a standalone product for Microsoft Office 365.
如有侵权请联系:admin#unsafe.sh