
2021-05-27 21:42:32 Author: www.forcepoint.com(查看原文) 阅读量:121 收藏
A Modern Approach to Zero Trust
But what is “Zero Trust”? How is it defined? What are its key components?
Confusion around Zero Trust
The EO doesn’t really go into a great amount of detail regarding the components that should be included in a Zero Trust architecture. It does specifically say that agencies should “incorporate, as appropriate, migration steps that the National Institute of Standards and Technology (NIST)…has outlined in standards and guidance.” That is a good start and provides a framework upon which agencies can and should build.
That is important, because to this point there has been no standardized definition of a Zero Trust architecture. Indeed, although many government agencies have already begun to adopt their own versions of Zero Trust, there has been very little consistency amongst different models. For example, earlier this year the Pentagon introduced a zero-trust architecture for the Department of Defense that includes a complex capabilities taxonomy tailored specifically to the DoD’s unique requirements. Meanwhile, other agencies, including NIST, the Air Force, the General Services Administration (GSA) and others have their own Zero Trust models.
The Department of Defense’s Zero Trust architecture (Source:Department of Defense Zero Trust Reference Architecture)
A survey from Forcepoint and the Ponemon Institute shows the various approaches that organizations are using to create their own Zero Trust architectures. According to respondents, 47% are basing their approach on NIST 800-207; 39% on the Forrester Zero Trust Model; 32% on Gartner’s Continuous Adaptive Risk and Trust Assessment (CARTA); and 25% on Gartner’s Secure Access Service Edge (SASE). The rest have created their own. The results are a testament to the lack of uniformity when it comes to building a Zero Trust environment.
But as we know, consistency and standardization simplify complex challenges, and cybersecurity is one of the most complex challenges facing government today. Having too many variations only adds greater complexity and confusion, both of which inhibit agencies’ abilities to successfully implement Zero Trust.
A Zero Trust architecture requires a balanced approach to security
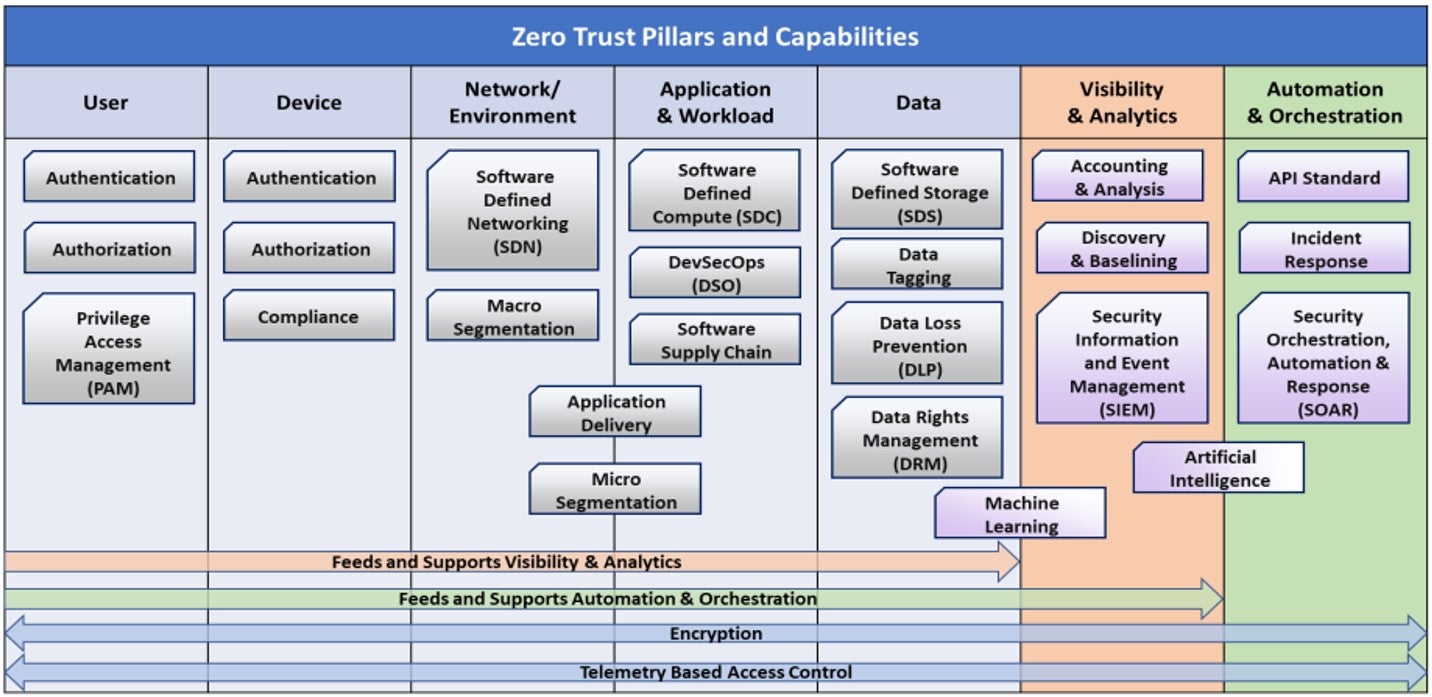
In the absence of Zero Trust standards, agencies should ensure they take a balanced approach when adopting a Zero Trust architecture. Ultimately the end goal is not about compliance, but about the results of the pieces of the architecture coming together. Many technologies can offer important pieces toward Zero Trust, but ultimately inter-dependency of behaviors across users, devices, applications, and data matter.
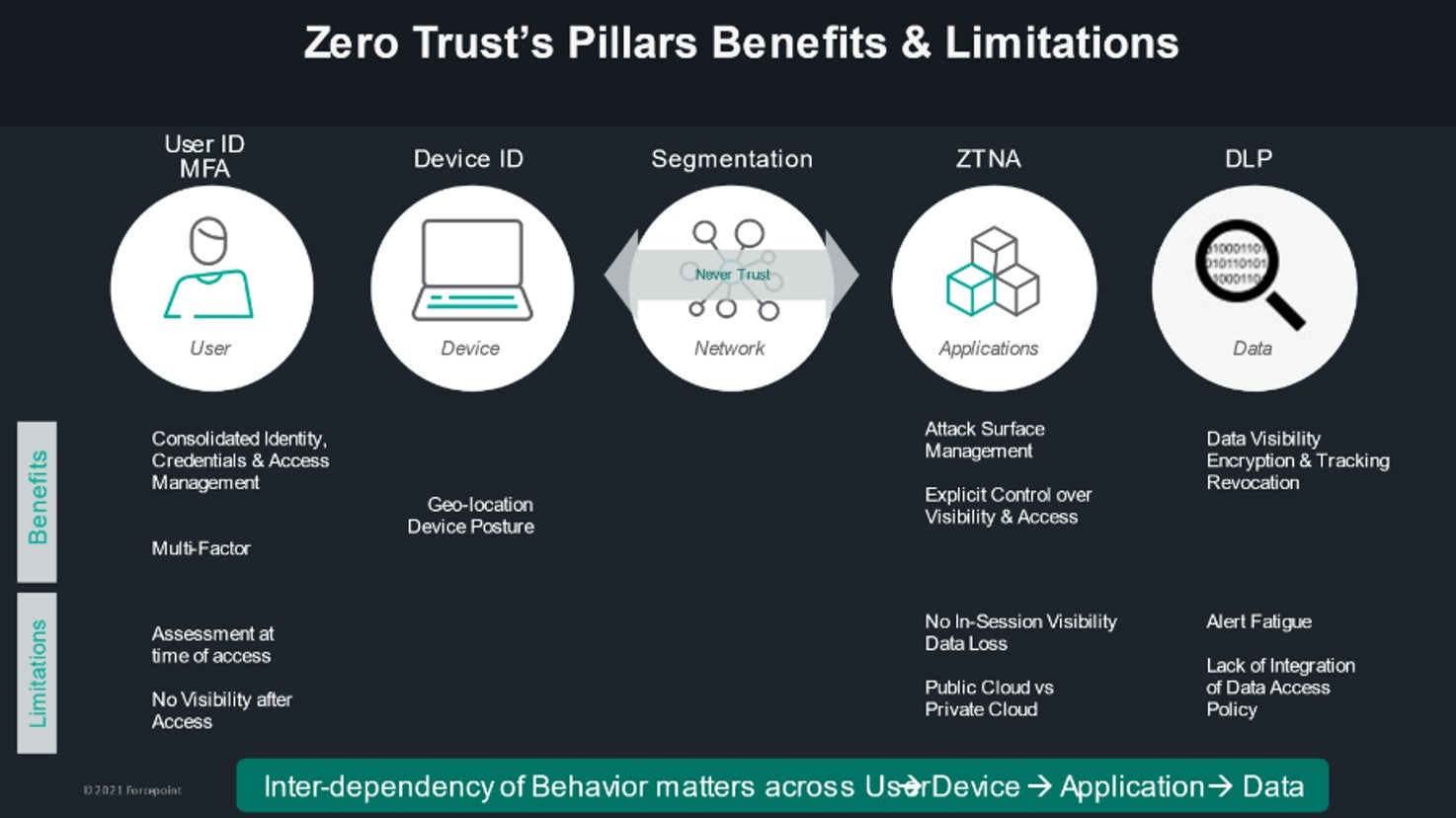
A complete Zero Trust architecture integrates Continuous Risk Adaptive Policies with user and device ID, ZTNA and DLP
Zero Trust is not just a means of controlling who is able to access a government network, but there’s much more to Zero Trust than just user and device identification. For example, the methodology has evolved to also include Zero Trust Network Access (ZTNA), which provides better attack surface management by encrypting applications and segregating them from the wider Internet.
Over-rotating toward a single technology as part of a Zero Trust architecture leaves holes in your security architecture. NIST 800-207 recognizes this and as one of the tenets for Zero Trust suggests “Access to resources is determined by dynamic policy—including the observable state of client identity, application, and the requesting asset—and may include other behavioral attributes…Behavioral attributes include automated user analytics, device analytics, and measured deviations from observed usage patterns.”
Improving the effectiveness of data loss prevention with behavioral attributes for continuous adaptive Zero Trust
With Zero Trust there’s still the problem of data visibility. A single user could be downloading one file or billions. Unfortunately, since DLP is often siloed off from the rest of a Zero Trust architecture, administrators may know who’s accessing their applications or network, but they do not have a clear picture of who’s downloading what or how much. Without integrating DLP into the rest of the architecture, administrators can’t accurately determine whether or not their data is secure.
An effective Zero Trust architecture drives agencies towards a more data and user-centric approach while moving away from being perimeter-centric. Integrating DLP with behavioral analytics enables your Zero Trust architecture to have:
- Individualized adaptive data policies
- Behavioral analytics driven insights
- Data discovery and classification
- Maximizing security analyst efficiency and reducing fatigue
Using behavior-based cybersecurity, your security adapts to changing levels of risk. This includes enterprise-wide visibility (network, endpoints, and cloud). This enables detection when people are exhibiting risky behavior: their risk score changes depending how they behave at any time, allowing security to tighten targeted policies and block actions if required. This helps security teams decides what is innocent or suspicious based on behavior in context, reducing false positives by leveraging intelligent data security to revisit decisions as you and your machines learn.
An effectively implemented Zero Trust architecture incorporates user identification and behavioral analysis, attack surface mitigation and data management for continuous and adaptive Zero Trust. Together, these components are important to helping agencies achieve the Biden Administration’s goal to “identify, deter, protect, and respond” to cyber threats.
如有侵权请联系:admin#unsafe.sh