SleepStudy logsMay 3, 2021 in Forensic Analy 2021-05-03 20:09:25 Author: www.hexacorn.com(查看原文) 阅读量:206 收藏
![]()
SleepStudy logs
May 3, 2021 in Forensic Analysis
A few days ago I came across ETL logs I have not seen before. They are residing inside c:\WINDOWS\System32\SleepStudy and I posted about them on Twitter. Not sure if anyone looked at them from a forensic perspective in the past – quick Twitter and Google search returned nothing of interest, hence decided to quickly describe it here.
The logs originate from “Microsoft-Windows-Kernel-Power” and “Microsoft-Windows-UserModePowerService” ETW providers. Files that can be found inside the directory are as follows:
- c:\WINDOWS\System32\SleepStudy\
- ScreenOn\ScreenOnPowerStudyTraceSession-YYYY-MM-DD-HH-MM-SS.etl
- UserNotPresentSession.etl
- user-not-present-trace-YYYY-MM-DD-HH-MM-SS.etl
These marked with a YYYY-MM-DD-HH-MM-SS patterns include timestamps, meaning multiple files following the same file naming pattern exist in the folder.
The user* files can be quickly converted from ETL to XML format by using the following commands:
tracerpt.exe <etlfile>
or
tracerpt.exe -of csv
if you prefer CSV output. The resulting files are dumpfile.xml or dumpfile.csv.
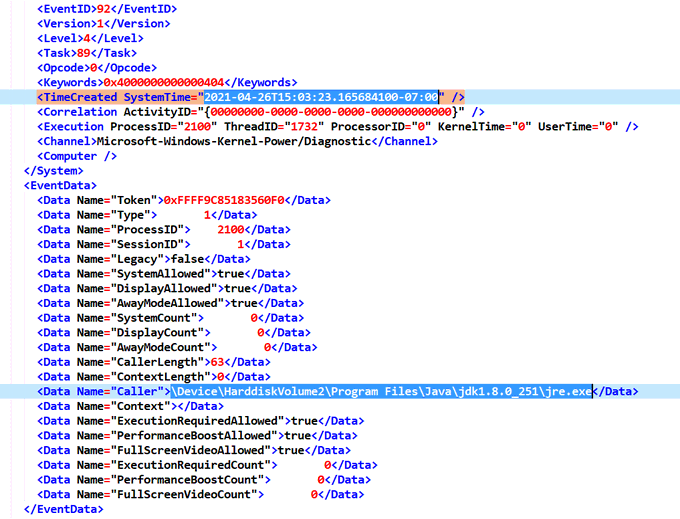
What triggered my interest was the fact we can see both paths and timestamps inside the output user* files:
I don’t know exactly what these log mean, but it can be yet another source of process execution telemetry.
如有侵权请联系:admin#unsafe.sh
