
2021-03-09 19:46:54 Author: infosecwriteups.com(查看原文) 阅读量:268 收藏

Hello Everyone!
This write-up about Dunzo Sensitive Information Disclosure Vulnerability.
The vulnerability could have allowed an attacker to access the internal monitoring dashboard of Dunzo.
Coming to the first part…
Subdomain Enumeration:
I started with subdomain enumeration. For subdomain enumeration, I used crt.sh.
what is crt.sh:
It’s a web interface. that lets you search for certs that have been logged by CT.
In this case, I got only a few subdomains. So I manually checked each subdomain. If you found a large number of subdomains you can use the Httpx tool from project discovery.
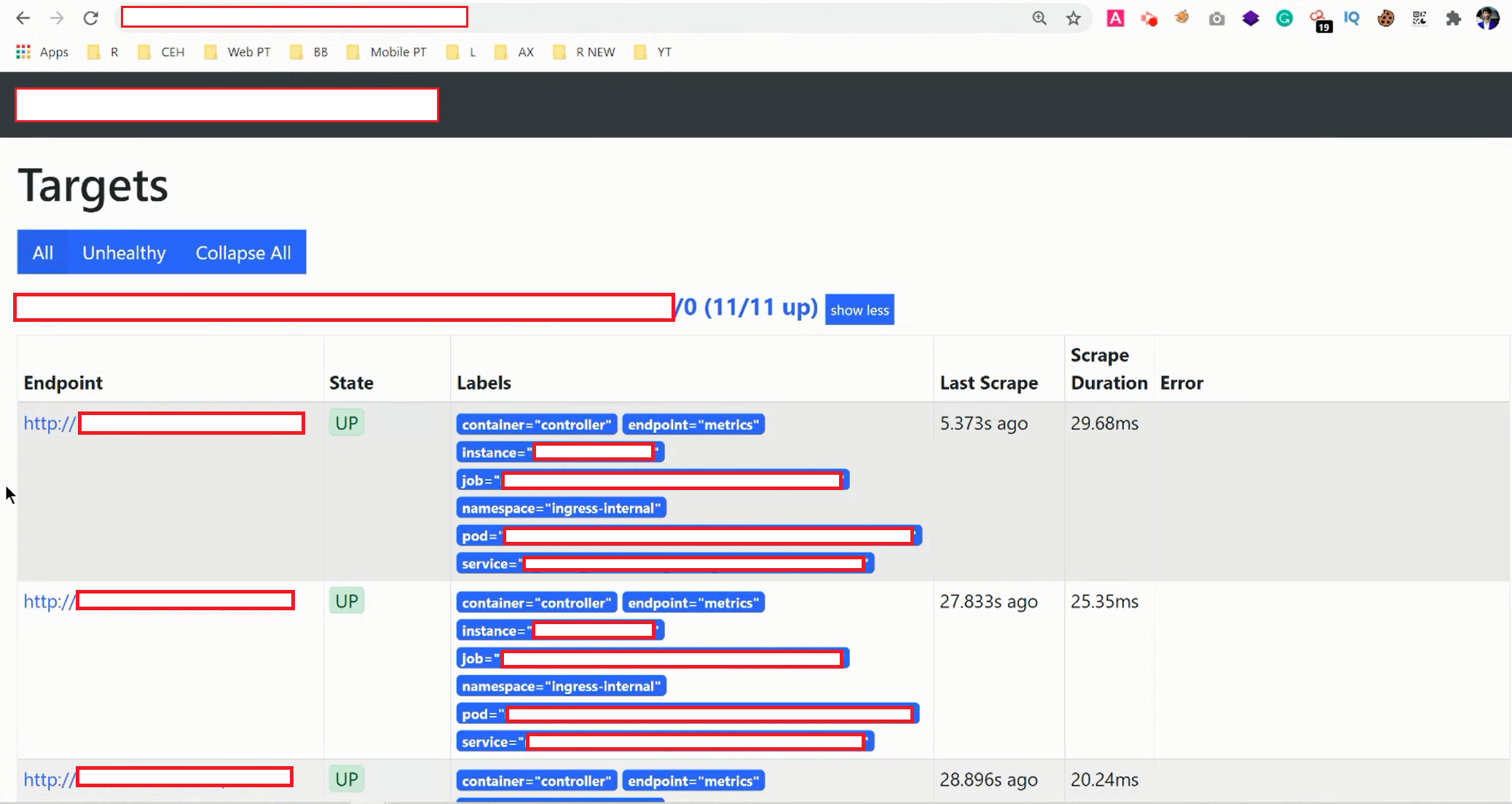
One of those domains able to access the internal dashboard without authentication. Here I got internal ip, logs detail (production servers).
Small Advice: Hunting on any bug bounty program or any other organization if you found any internal ip other details, don’t exploit more. Because the entire production environment running on these servers. So kindly create a detailed POC and report it to the respective team.
POC of my findings….

Appreciation from Dunzo

Report Details:
· Mon, 11 Jan 2021 — Reported to Dunzo Security Team.
· Mon, 11 Jan 2021- Immediately got a response from the team
· Tue, 12 Jan 2021-Issue Fixed
· Tue, 12 Jan 2021 — Re-tested and confirmed the fix
· Tue, 12 Jan 2021 — This time Now Bounty only Appreciation! (Because dunzo don't have a bug bounty program)
Thanks for reading!……Happy Hacking!
Linkedin: Lohith Gowda M
Twitter: lohigowda_in
Portfolio: https://www.lohigowda.in/
如有侵权请联系:admin#unsafe.sh