Microsoft previously blogged our strong recommendation that customers upgrade their on-premises Exchange environments to the latest supported version. For customers that are not able to quickly apply updates, we are providing the following alternative mitigation techniques to help Microsoft Exchange customers who need more time to patch their deployments and are willing to make risk and service function trade-offs.
These mitigations are not a remediation if your Exchange servers have already been compromised, nor are they full protection against attack. We strongly recommend investigating your Exchange deployments using the hunting recommendations here to ensure that they have not been compromised. We recommend initiating an investigation in parallel with or after applying one of the following mitigation strategies. This blog also contains a nmap script to help you discover vulnerable servers within your own infrastructure.
Customers should choose one of the following mitigation strategies based on your organization’s priorities:
Recommended solution:
Install the security patch
- This method is the only complete mitigation and has no impact to functionality.
- The following has details on how to install the security update: https://techcommunity.microsoft.com/t5/exchange-team-blog/released-march-2021-exchange-server-security-updates/ba-p/2175901
- This will not evict an adversary who has already compromised a server.
Interim mitigations if unable to patch Exchange Server 2013, 2016, and 2019:
Implement an IIS Re-Write Rule and disable Unified Messaging (UM), Exchange Control Panel (ECP) VDir, and Offline Address Book (OAB) VDir Services
- These mitigations have some known impact to functionality described below in detail.
- These mitigations are effective against the attacks we have seen so far in the wild but are not guaranteed to be complete mitigations for all possible exploitation of these vulnerabilities.
- This will not evict an adversary who has already compromised a server.
- This should only be used as a temporary mitigation until Exchange servers can be fully patched.
IIS Re-Write rule – CVE-2021-26855
Description: This mitigation will filter https requests that contain malicious X-AnonResource-Backend and malformed X-BEResource cookies which were found to be used in the SSRF attacks in the wild. This will help with defense against the known patterns observed but not the SSRF as a whole.
Note: The IIS Rewrite rules will be removed after Exchange is upgraded and the mitigation will need to be reapplied if the security patch has not been installed.
Impact: No known impact to Exchange functionality, however, limited testing has been performed.
Requirements:
- URL Rewrite Module: https://www.iis.net/downloads/microsoft/url-rewrite[JH1]
- PowerShell script to create URL rewrite rules to mitigate the SSRF (CVE-2021-26855):
- CSS-Exchange/BackendCookieMitigation.ps1 at main · microsoft/CSS-Exchange (github.com)
Example Usage:
To apply with MSI install via PowerShell:
.\BackendCookieMitigation.ps1 -FullPathToMSI “" -WebSiteNames "Default Web Site" -Verbose
PowerShell command to create IIS rewrite rule without installing the IIS rewrite module:
.\BackendCooieMitigation.ps1 -WebSiteNames "Default Web Site" -Verbose
To revert changes:
.\BackendCookieMitigation.ps1 -WebSiteNames "Default Web Site" -RollbackMitigation -Verbose
Validation: Rewrite rules can be found in C:\inetpub\wwwroot\web.config or in the IIS UI of the “Default Web Site”:



Disable UM Services – CVE-2021-26857
Description: Disabling the UM Service will mitigate CVE-2021-26857.
Impact to Exchange: Unified Messaging/Voicemail outage when these services are disabled.
Via Exchange Management Shell:
Set-ServerComponentState -Component UMCallRouter -Identity -Requester Maintenance -State Inactive
Stop-Service MSExchangeUM
Set-Service MSExchangeUM -StartupType Disabled
Stop-Service MSExchangeUMCR
Set-Service MSExchangeUMCR -StartupType Disabled
Validation:
Get-Service MSExchangeUM
Get-Service MSExchangeUMCR
Get-ServerComponentState -Identity -Component UMCallRouter | fl

Rollback:
Set-ServerComponentState -Component UMCallRouter -Identity -Requester Maintenance -State Active
Set-Service MSExchangeUM -StartupType Automatic
Start-Service MSExchangeUM
Set-Service MSExchangeUMCR -StartupType Automatic
Start-Service MSExchangeUMCR
Disable ECP Application Pool- CVE-2021-27065
Disabling ECP Virtual Directory will prevent CVE-2021-27065 from executing successfully as the API will no longer respond and return a 503 when calling the Exchange Control Panel (ECP).
Impact to Exchange: Exchange Control Panel will be offline and return a 503. All Exchange Administration can be done via Remote PowerShell while the Exchange Control Panel is disabled.
Via Exchange Management Shell:
Set-ServerComponentState -Component EcpProxy -Identity -Requester Maintenance -State Inactive
Import-module WebAdministration
$AppPoolName = "MSExchangeECPAppPool"
$AppPool = Get-Item IIS:\AppPools\$AppPoolName
$AppPool.startMode = "OnDemand"
$AppPool | Set-Item -Verbose
Stop-WebAppPool -Name $AppPoolName
Validation: Confirm the App Pool is stopped in IIS.

Get-WebAppPoolState -Name "MSExchangeECPAppPool"

Confirm Server Component State EcpProxy is Inactive:
Get-ServerComponentState -Component EcpProxy -Identity <ComputerName> | fl

Browse to https://127.0.0.1/ecp from the Exchange server:

Rollback:
Set-ServerComponentState -Component EcpProxy -Identity -Requester Maintenance -State Active
Import-module WebAdministration
$AppPoolName = “MSExchangeECPAppPool”
$AppPool = Get-Item IIS:\AppPools\$AppPoolName
$AppPool.startMode = “OnDemand”
$AppPool | Set-Item -Verbose
Start-WebAppPool -Name MSExchangeECPAppPool
Get-WebAppPoolState -Name “MSExchangeECPAppPool”
Get-ServerComponentState -Component EcpProxy -Identity | fl
Disable OAB Application Pool – CVE-2021-26858
Disabling OAB Application Pool will prevent CVE-2021-26858 from executing successfully as the API will no longer respond and return a 503 when calling OAB, which will mitigate the Arbitrary Write exploit that occurs with OAB. After stopping the WebApp Pool you will also need to set the OabProxy Server Component state to InActive.
Impact to Exchange: Calls to OAB will fail and return a 503 error. Downloads of the Offline Address Book by Outlook clients will fail which may result in stale address book results in some scenarios and configurations.
Via Exchange Management Shell:
Set-ServerComponentState -Component OabProxy -Identity -Requester Maintenance -State Inactive
Import-module WebAdministration
$AppPoolName = "MSExchangeOABAppPool"
$AppPool = Get-Item IIS:\AppPools\$AppPoolName
$AppPool.startMode = "OnDemand"
$AppPool | Set-Item -Verbose
Stop-WebAppPool -Name MSExchangeOABAppPool
Validation:
Confirm IIS App Pool is stopped:

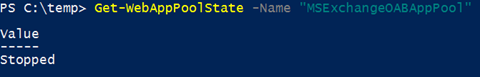
Get-WebAppPoolState -Name "MSExchangeOABAppPool"

Confirm Server Component State OabProxy is Inactive:
Get-ServerComponentState -Component OabProxy -Identity <ComputerName> | fl

Rollback:
Set-ServerComponentState -Component OabProxy -Identity -Requester Maintenance -State Active
Import-module WebAdministration
$AppPoolName = "MSExchangeOABAppPool"
$AppPool = Get-Item IIS:\AppPools\$AppPoolName
$AppPool.startMode = "OnDemand"
$AppPool | Set-Item –Verbose
Start-WebAppPool -Name MSExchangeOABAppPool
Get-WebAppPoolState -Name "MSExchangeOABAppPool"
Get-ServerComponentState -Component OabProxy -Identity | fl
Nmap Script To Scan For CVE-2021-26855
Detects whether the specified URL is vulnerable to the Exchange Server SSRF Vulnerability (CVE-2021-26855). This can be used to validate patch and mitigation state of exposed servers.
Download from: CSS-Exchange/http-vuln-cve2021-26855.nse at main · microsoft/CSS-Exchange (github.com)
Installation on Windows:
- Add to the following directory:
C:\Program Files (x86)\Nmap\scripts - Run the following to add the script to
nmap: nmap --script-updatedb
Example Usage:
Nmap -Pn -p T:443 --script http-vuln-cve2021-26855 <IP>