
2021-02-26 04:49:09 Author: infosecwriteups.com(查看原文) 阅读量:212 收藏
Okay, so Slack can’t actually perform port scans! However, it can act as a communication channel to relay tasks, such as port scanning, to a remote server.
This post demonstrates how to use Slack to automate repetitive, resource intensive tasks during bug bounty hunting or any offensive security engagement. This comes with multiple benefits and ultimately frees up your primary host to continue testing until results are returned.

Introduction
Port scanning is an essential step in the recon process that can lead to missed opportunities if left unchecked. However, its time and resource constraints make it one of my least favorite activities when up against larger scopes.
Using Slack, we can delegate port scanning to a remote server and alleviate stress on our primary host. Once implemented, simply upload the target, or target.txt file, and await the results.
This technique can also help in continuous recon, collaboration, and testing from smaller, less capable devices such as smart phones or tablets. All of which, contribute to better hunts and the identification of more vulnerabilities!
Requirements
- [Private] Slack workspace with admin access.
- Remote server utilizing a Debian based Linux distribution. This can be a cloud system or just another host on the local network.
- Python 3.6+ installed on the server.
Slack Setup
Using access to your workspace, create a channel for the remote server to monitor. This will be used to relay tasks and retrieve results. These can be broken out by server names, tools, or tasks as shown below:

Next, create a new Slack app with the following permissions and install it in your workspace. Don’t forget to go back and add the app to any channels previously created — forgetting this could result in API permission errors.
channels:history
channels:read
channels:write
files:read
files:write
users:readServer Setup
Once Slack is configured, the next step is to install the monitoring program on the remote server. This will utilize Slack’s API to track conversations in the predefined channel. If a valid command is issued by an authorized user, the monitoring application will execute the task and return the results.
To simplify this step, I have created a Python monitoring script called slackexec.py and made it freely available on GitHub. Be sure to follow the directions in the header to setup your host, install all required dependencies, and fill in your Slack configuration settings:

Execution
With setup complete, slackexec.py can be run in the background or configured as a service with systemctl. Either approach will allow you to execute commands and begin automating your port scans with Slack!
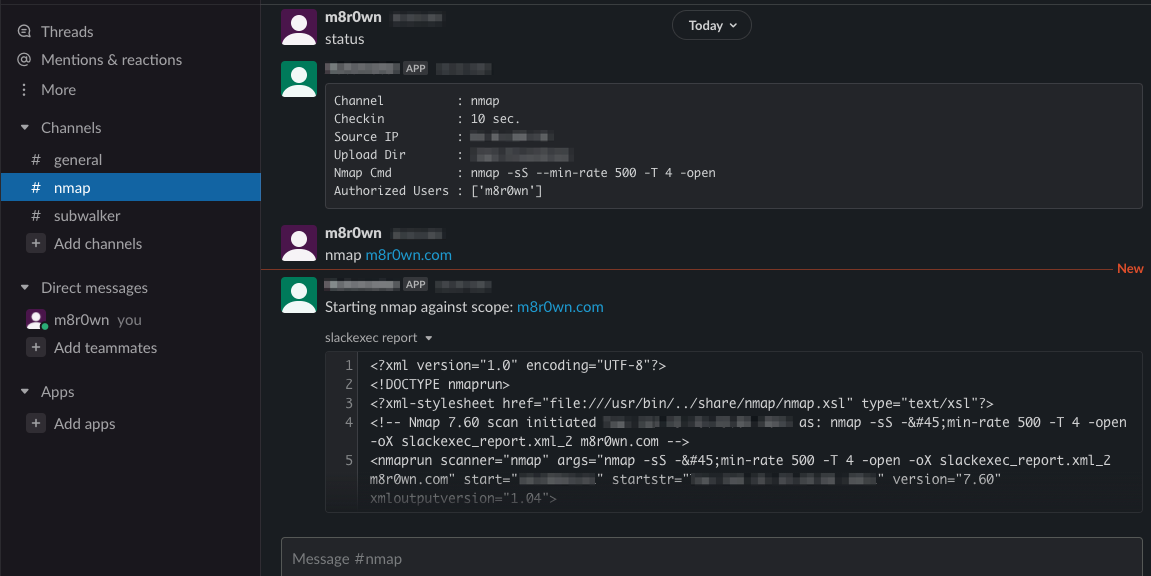
Authorized users can give the nmap command followed by scope or scope.txt file. The remote host will interpret the command and execute the task in a new thread. Once finished, an XML report will be returned with the results.
The following is a list of all available actions with slackexec.py. This can be recalled in your own channel using the help command:
status Get current status and defined commands.
shutdown Shutdown monitoring app.
checkin [#] Change check-in time (seconds).
channel [name] Change monitoring channel.
update [nmap cmd] Update Nmap command & arguments.
add-user [slack user] Add authorized user for execution.
nmap [scope|file] Execute nmap scan.Closing Remarks
When using Slack automation for bug bounty hunting, consider the use of cloud servers to provide an alternate source address. This is especially useful when executing “loud” attacks against hardened targets to prevent adverse effects on your primary address.
For users outside the security space, the tools and techniques provided can be easily adapted to run alternate tasks. This will allow users to initiate remote activities over Slack and better utilize their time.
Lastly, be sure to review Slack’s Acceptable Use policy before implementing automation via the API to ensure you are in compliance with their guidelines.
如有侵权请联系:admin#unsafe.sh