
2021-02-10 21:45:37 Author: www.nowsecure.com(查看原文) 阅读量:208 收藏
The U.S. federal government relies on an extensive array of mobile applications to run operations, defend the country and engage with citizens. Mobile has changed the way apps are released and updated, and federal agencies such as the Department of Defense have adopted DevSecOps to unleash speed and innovation. In fact, the Air Force operates a number of software factories such as BESPIN, Kessel Run and Platform One.
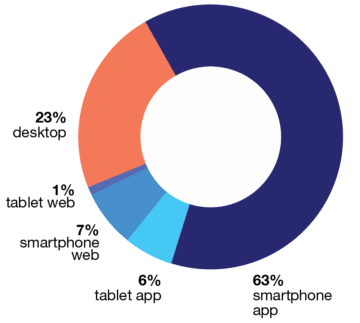
Mobile apps dominate digital media usage with 69% of all digital traffic, surpassing time spent on the web, according to Comscore’s “Global State of Mobile” report. Smartphone app use continues to rise and now accounts for 63% of all digital use, while tablet apps garner 6%. In comparison, smartphone and tablet web use accounts for only 8% of all digital media time combined, showing a strong preference for native mobile apps over web.
However, mobile app risks abound. NowSecure benchmark testing of apps from the Apple® App Store® and Google Play™ reveal 85% of mobile apps have security vulnerabilities and 70% leak private data. Alarmingly, that means many of the mobile apps that federal agencies build, buy and use could expose critical Intellectual Property (IP) or Personally Identifiable Information (PII) of citizens and users that could compromise national security.
Federal Mobile App Security Risks
Mobile app security issues have put service members in harm’s way or potentially compromised intelligence. Consider these incidents:
- Researchers used the beer app Untappd to follow the movements of military and intelligence personnel worldwide to uncover sensitive data and trips to sensitive locations.
- Attackers exploited the pandemic to create an Android coronavirus tracking app ransomware that locks phones and demands payment in bitcoin.
- Last year, Kilswitch/APASS software used for air support coordination and situational awareness put Marines and sailors at substantial risk of hackers and foreign adversaries gaining access to sensitive battlefield information or location data.
- A few years ago, the Strava fitness tracking interactive map and app revealed sensitive locations of U.S. troops who used fitness tracking devices while exercising.
- In 2016, a cyberattack of an artillery app proved deadly when hackers used it to target Ukrainian troops. In all of these cases, hackers could learn troop locations using the apps and in some cases, could access other highly sensitive operational information.
- In 2015, NowSecure researchers discovered a supply-chain vulnerability called Corrupdate that impacted Samsung Account and GALAXY apps by allowing an adjacent network attacker to replace an official Samsung app update with his own malicious apk.
Mobile app security issues have put service members in harm’s way or potentially compromised intelligence.
In the cases above, insecure mobile apps could have potentially life-threatening consequences and underscore the need for a rigorous process to find and fix mobile application security vulnerabilities within internally developed code and the external software supply chain before software is released. “Mobile security is the most significant challenge,” said DoD Acting CIO Terry Halvorsen in 2017. And a NowSecure federal customer shared, “The biggest challenge is the length of time to proceed through the risk management framework process.”
But at the same time, a high security bar impedes release cadence. Military departments must support a rigorous process that can quickly catch and resolve security issues to achieve continuous ATO that is necessary to get critical apps in the hands of service members and warfighters faster. And for continuous ATO, they need DevSecOps.
The recent SolarWinds supply-chain attacks have dramatically heightened security concerns and underscore the risks posed throughout elements of the supply chain. All federal agencies use commercial mobile apps and therefore should continuously monitor their mobile app supply chain for security, privacy and compliance risks.
As a focused mitigation effort in agency mobile app supply chains, continuous vetting of new and currently deployed mobile apps for cyberrisks or changes in behavior over time is critically important to block or remove high-risk mobile apps from agency users and networks. Common risks and attacker exploits include :
- Leaking credentials that could be used to move laterally through the network
- Failure to properly validate connections that could redirect users to phishing sites
- Wide-scale leakage of PII, geolocation, telemetry and other mission-critical data.
Learn more about how the US Marshals Service protects its mobile supply chain in this case study.
Continuous Mobile AppSec Testing
Including security in the mobile app dev process enables federal agencies to achieve continuous security through automation. The complexity and time-consuming nature of manual application security testing makes it impossible to scale to accommodate the growing volume, velocity and frequency of mobile app releases. But automated mobile app security testing solutions allow federal agencies to quickly and reliably assess mobile apps at the speed required by DevOps teams.
To uncover vulnerabilities, privacy issues and compliance flaws, agencies must continuously test open-source components from the software supply chain and compiled mobile app binaries. For open source, be sure to test components with software composition analysis tools. For mobile app binary security testing, look for thorough coverage of SAST, DAST, IAST and API Security Testing based on industry standards such as OWASP Mobile Application Security Verification Standards (MASVS) and National Information Assurance Partnership (NIAP).
Testing tools should seamlessly integrate with the CI/CD pipeline and ticketing systems to autonomously run in the background and test every build, every day. Fast feedback loops enable developers to quickly fix issues as they build the mobile app, saving time and money. For defense agencies that require the rigorous assurance of NIAP compliance, automated NIAP testing is available to dramatically speed ATO. By automating security testing with the right testing criteria in the DevSecOps process, federal agencies can accelerate into continuous ATO.
To gain insight about optimizing the mobile software development lifecycle to deliver mobile apps quickly and securely, download our ebook, “The Ultimate Guide to Establishing an Effective Mobile DevSecOps Toolchain.”
如有侵权请联系:admin#unsafe.sh

