
2020-12-07 01:00:00 Author: www.forcepoint.com(查看原文) 阅读量:194 收藏
Back in March, when people in enterprises and government agencies fled their offices and started working from home, most IT organizations performed heroic acts to get users connected to the applications and data they needed to keep things running.
Cloud applications were no problem for newly remote workers to get to (which provided a lot of motivation to switch to SaaS apps where possible). But private apps in internal data centers or private cloud environments were. While few in number, internal programs that are hidden from the internet are often are some of the more critical line-of-business apps (and difficult to move).
In a previous blog post, I wrote that VPN software provided a quick-and-dirty way to get people connected. But it also created headaches for users, network infrastructure staff, and security teams alike. Although the world is still in turmoil, IT teams have largely gotten past the immediate fire drills and are able to look at what they need to change to handle having people work anywhere—at home, in the office, at remote sites, even (eventually) traveling. High on many of their lists: getting rid of end-user VPN software.
That’s why we developed Forcepoint Private Access. Our human-centric SASE platform already brought together protection for using web content and cloud apps; now with Private Access, it makes internal private apps just as easy—and safe—to use.
Zero Trust is about access and more
But even more importantly, Private Access helps our customers fix one of the fundamental problems that has long plagued security. In traditional security approaches, people who are “inside” the network (whether physically or by VPN) are implicitly trusted (see diagram below). They can access anything. Data that is obtained from those applications can be used, copied and moved. And, IT controls tend to be static and very manual. At Forcepoint, we’re using the principles in Zero Trust to flip this around, requiring that people be explicitly trusted at every stage:
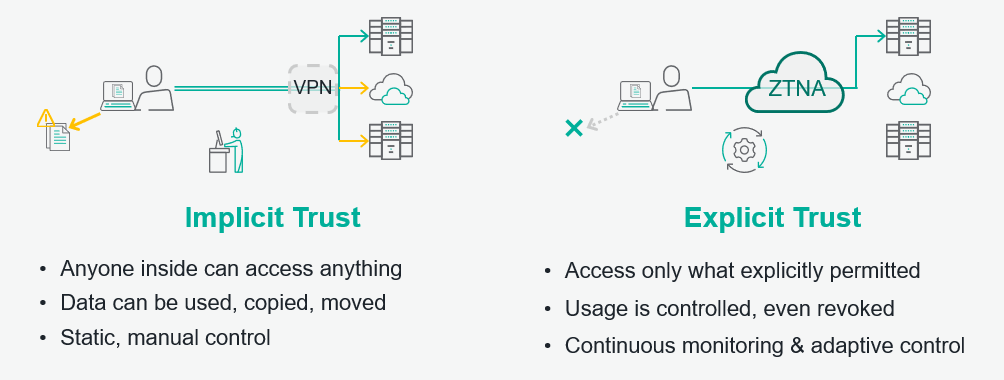
Private Access limits the internal applications each user can see to only those they have been granted specific permission to access. Forcepoint DLP makes sure that data from those applications remains controlled, with the right to retransmit the data revokable at any time. And, our Forcepoint Dynamic User Protection provides continuous user activity monitoring, enabling controls on data to be automated and personalized based on the risk each user’s own behaviors present. The end result is better productivity, lower costs, more security access, and simpler compliance.
To learn more, please visit our Private Access and Zero Trust pages, or click on the green Read the eBook button on the right to download The Path to Zero Trust eBook.
如有侵权请联系:admin#unsafe.sh