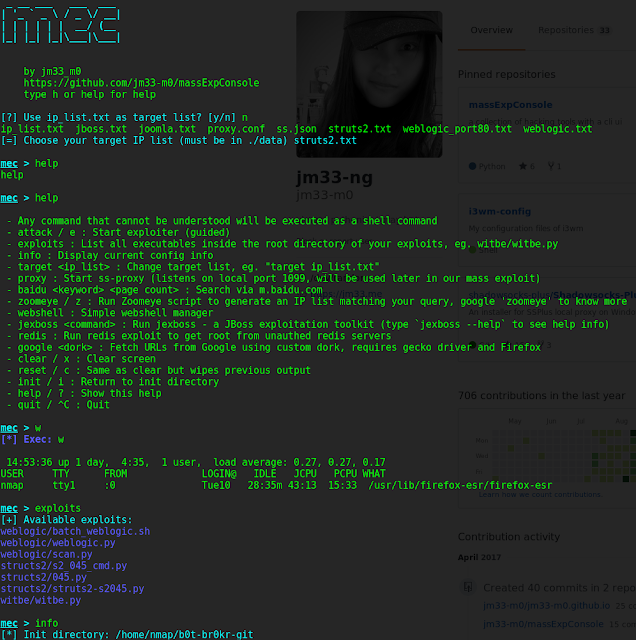
Collection of Tools and Exploits with a CLI UI
What does it do?
- an easy-to-use user interface (cli)
- execute any adapted exploit with process-level concurrency
- crawler for baidu and zoomeye
- a simple webshell manager
- some built-in exploits (automated)
- more to come...
- GNU/Linux or MacOS, WSL (Windows Subsystem Linux), fully tested under Kali Linux (Rolling, 2017), Ubuntu Linux (16.04 LTS) and Fedora 25 (it will work on other distros too as long as you have dealt with all deps)
proxychains4(in$PATH), used by exploiter, requires a working socks5 proxy (you can modify its config inmec.py)- Java is required when using Java deserialization exploits, you might want to install
openjdk-8-jreif you haven't installed it yet - python packages (not complete, as some third-party scripts might need other deps as well):
requestsbs4beautifulsoup4html5libdocoptpip3 installon the go
- note that you have to install all the deps of your exploits or tools as well
Usage
- just run
mec.py, if it complains about missing modules, install them - if you want to add your own exploit script (or binary file, whatever):
cd exploits,mkdir <yourExploitDir>- your exploit should take the last argument passed to it as its target, dig into
mec.pyto know more chmod 755 <exploitBin>to make sure it can be executed by current user- use
attackcommand thenmto select your custom exploit
- type
helpin the console to see all available features