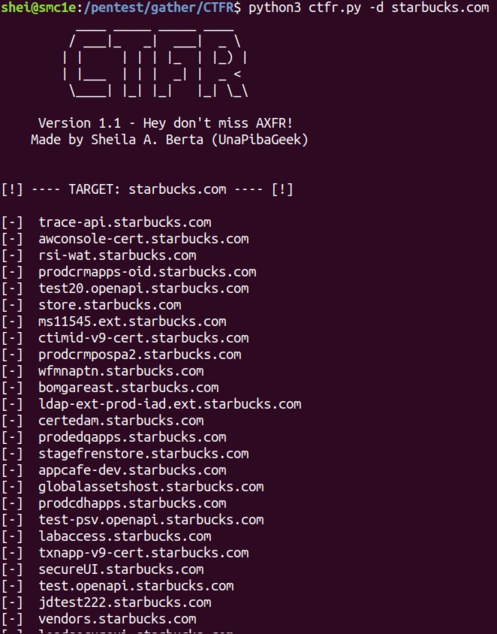
Do you miss AXFR technique? This tool allows to get the subdomains from a HTTPS website in a few seconds.
How it works? CTFR does not use neither dictionary attack nor brute-force, it just abuses of Certificate Transparency logs.
For more information about CT logs, check www.certificate-transparency.org.
Getting Started
Please, follow the instructions below for installing and run CTFR.
Pre-requisites
Make sure you have installed the following tools:
Python 3.0 or later.
pip3 (sudo apt-get install python3-pip).Installing
git clone https://github.com/UnaPibaGeek/ctfr.git
cd ctfr
pip3 install -r requirements.txtRunning
python3 ctfr.py --helpUsage
Parameters and examples of use.
Parameters
-d --domain [target_domain] (required)
-o --output [output_file] (optional)Examples
python3 ctfr.py -d starbucks.compython3 ctfr.py -d facebook.com -o /home/shei/subdomains_fb.txtScreenshot
Author
- Sheila A. Berta - (@UnaPibaGeek).