The Good
Praise is being heaped on both Apple and five “white hat” bug bounty researchers this week for some stunning work that led to the fixing of 55 bugs, 11 of which were rated critical, in Apple products and infrastructure. The researchers – Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samuel Erb and Tanner Barnes – spent three months quietly hacking into Apple systems, turning up one zero day bug after another. The most severe bugs included the ability to take over a user’s iCloud account by sending the user a maliciously crafted email. Merely by opening the email – no further clicks or social engineering required – a user would not only have given the attackers full control over their own iCloud account but also caused the wormable exploit to be sent to all of their contacts.
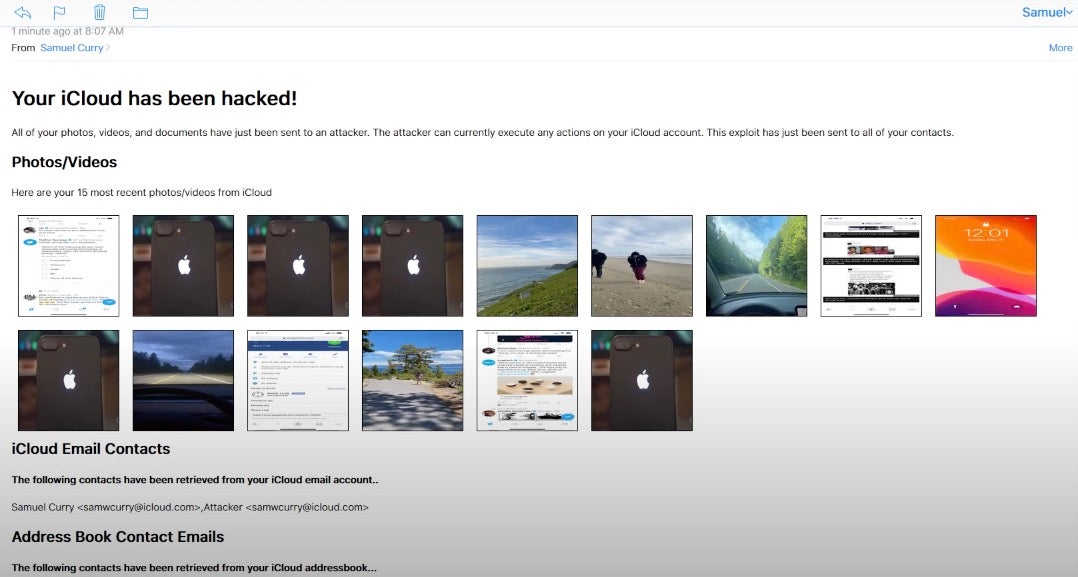
So what makes this such a good news story? There are multiple wins here, for the researchers, for Apple, and for Apple users. First, the researchers themselves took the responsible path and fully disclosed the bugs to Apple. Given the severity of some of these zero days, one can imagine less scrupulous researchers might have been tempted to try and trade some or all of these to third parties for handsome sums. Second, Apple promptly fixed the bugs, sometimes within 48 hours, ensuring that users were not left exposed any longer than absolutely necessary. Apple have said that their logs do not indicate any of these bugs have been exploited in the wild. A third win was for the researchers themselves: Apple are still assessing payout according to the terms of their bug bounty program, but to-date the researchers have received almost $300,000 in rewards, with another $200,000 likely on the way.
And that leads to a bigger win for the security research community at large. There’s been some scepticism about Apple’s bug bounty program in the past, and Apple’s reaction here is exemplary: The researchers were rewarded, allowed to publish the details, and the bugs were fixed in record time. That’s only going to encourage other researchers to engage with Apple’s bug bounty program, and that’s a win for us all.
The Bad
Malware in firmware is a particularly bad thing, but at the same time it’s relatively rare. LoJax made big news back in 2018 as the first UEFI rootkit to be found in the wild, and since then the only other known malware targeting firmware was found in the leak of tools from Italian private intelligence firm “Hacking Team” back in 2015. However, that code hadn’t been seen used in the wild, until now. Researchers this week have published details of an investigation in which they found a modified version of Hacking Team’s “Vector-EDK” malware being used in targeted attacks on diplomats and NGOs from Africa, Asia and Europe.
According to the researchers, the malicious firmware was used to drop a malware executable, “IntelUpdate.exe”, into the victim’s Startup folder, which in turn appears designed to deploy a wider malicious framework dubbed “MosaicRegressor”. The framework’s downloaders contain a variety of mechanisms for contacting the attacker’s C2s, including CURL, WinHTTP API and the BITS transfer interface. Unusually, there is also a POP/SMTP/IMAP mechanism to fetch payloads from hard-coded email addresses, [email protected] and [email protected]. Full functionality of the framework and payloads has not yet been ascertained as the researchers were not able to retrieve all components of the malware framework. However, one component, load.rem, appears to be a document stealer targeting the user’s Recent Documents directory.
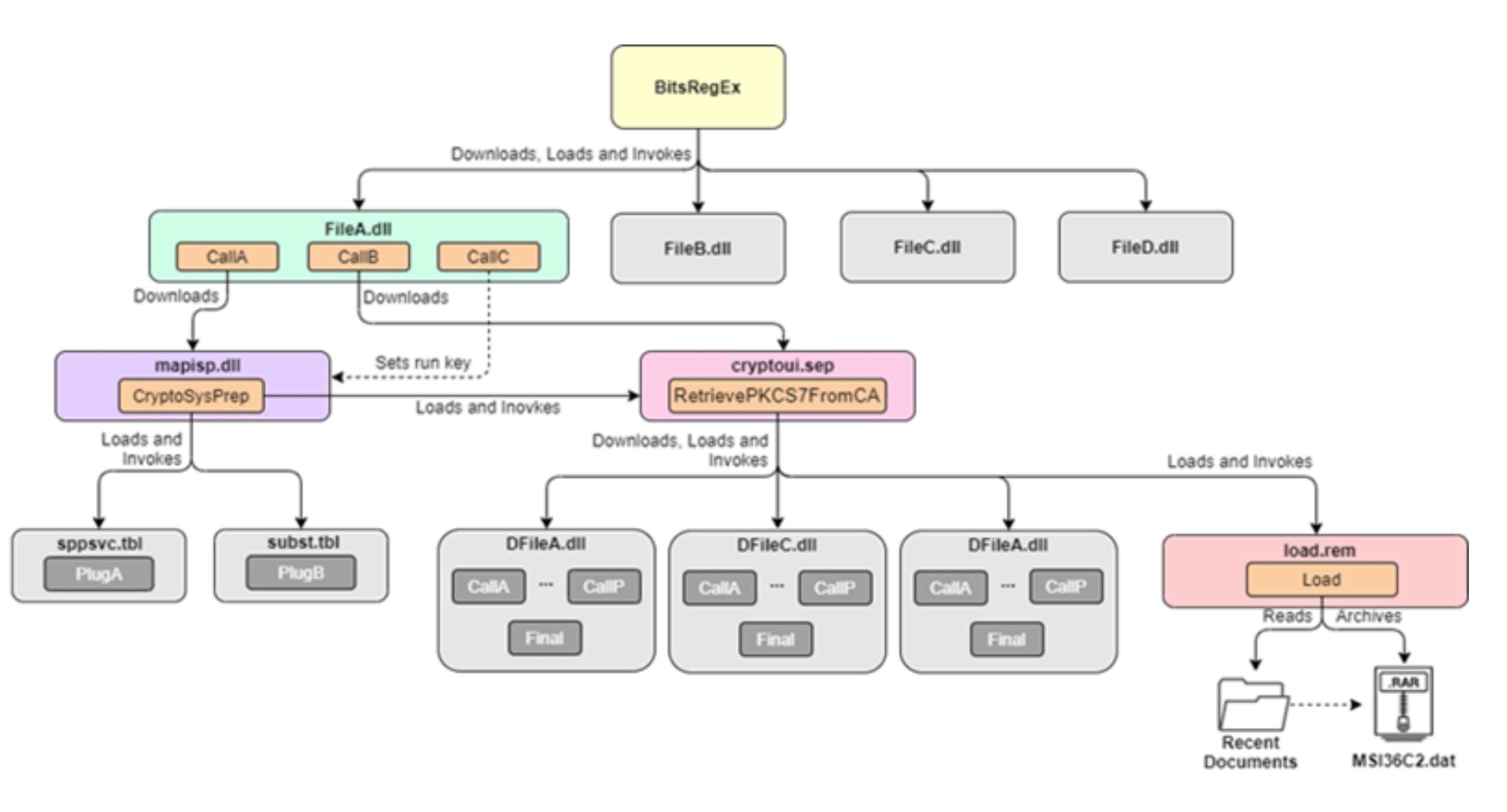
Source: Securelist
As for how the as-yet unattributed APT group planted the malicious UEFI images, that remains at present unknown, though the options appear to be either via physical access to the machines or through a compromised firmware update mechanism. Given the rarity of UEFI attacks, the full details are certainly worth a read. See these links for background on dumping UEFI and on reversing UEFI images.
The Ugly
For 25,000 Massachusetts school students hoping to recapture some sense of normalcy this fall with return to classes, it turned out to be a disappointing week. A ransomware attack on the Springfield Public Schools district on Thursday has resulted in closure of the schools and the suspension of all learning till further notice.
The attack has affected both bricks-and-mortar schools and all remote learning activities as the district took swift action to contain the ransomware by ordering all school devices to be shut down immediately.
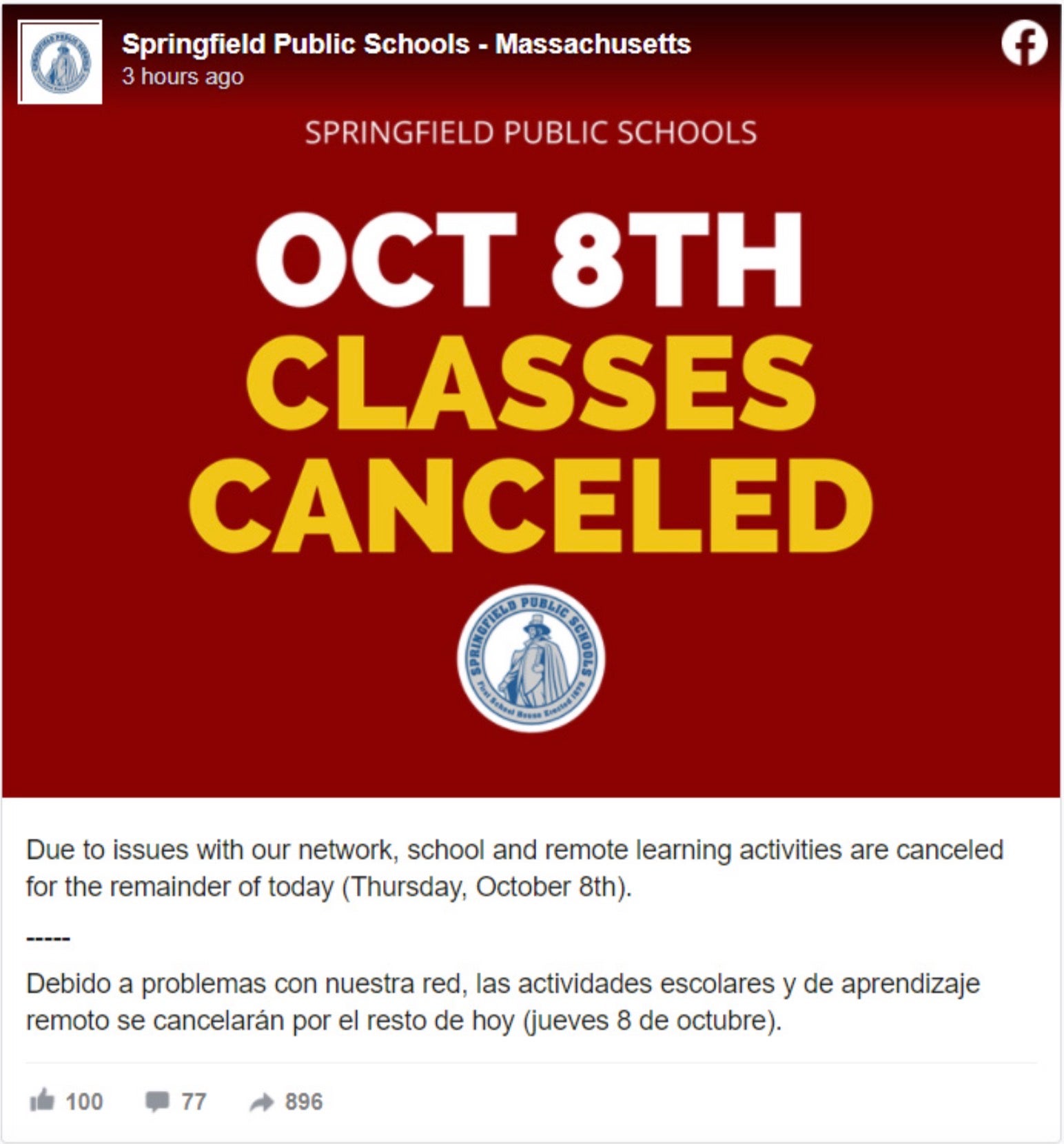
Aside from the students at more than sixty schools, the closures also affect 4,500 teaching and other staff.
It is not yet known which family of ransomware is involved or whether the attack has involved a data breach. An announcement about when learning activities will be able to resume was no more specific than stating it was “anticipated that the risk will be cleared and resolved in the near future.” Let’s hope for the sake of staff, students and families that’s sooner rather than later.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Healthcare and Cybersecurity in the Times of Covid-19
- How to Catch a Spy | Detecting FinFisher Spyware on macOS
- APTs and Defending the Enterprise in an Age of Cyber Uncertainty
- Unifying Endpoint Security for Enterprise | An Interview With Migo Kedem
- Revisiting the Pyramid of Pain | Leveraging EDR Data to Improve Cyber Threat Intelligence
- How Ransomware Attacks Are Threatening Our Critical Infrastructure
- The C-suite Guide to Cyber Safety | 7 Steps to Securing Your Organization
- What Is Cloud Security (and How Do You Secure the Cloud Today)?
