
好的,我现在需要帮用户总结一篇文章的内容,控制在100个字以内。首先,我得仔细阅读文章,理解其主要内容和关键点。 文章讲的是Arkanix Stealer,这是一个信息窃取的恶意软件,2025年底在暗网论坛上推广。它由AI辅助开发,有两个版本:基本版用Python,高级版用C++并有反病毒功能。作者两个月后就关闭了控制面板和Discord服务器。卡巴斯基的研究人员发现它使用了LLM(大语言模型)来开发,这可能大大缩短了开发时间和成本。此外,Arkanix的功能包括窃取浏览器数据、加密钱包信息、传播到Discord好友等。 接下来,我需要将这些信息浓缩到100字以内。重点包括:Arkanix Stealer是什么、它的功能、开发者背景、以及卡巴斯基的研究发现。 可能的结构是:介绍Arkanix Stealer及其功能,提到AI辅助开发和推广情况,最后说明其短暂存在和目的。 现在组织语言: “Arkanix Stealer是一款由AI辅助开发的信息窃取恶意软件,在2025年底通过暗网论坛推广。该软件分为基础版和高级版,具备数据窃取、传播及反分析功能。开发者两个月后关闭相关服务。卡巴斯基研究发现其使用大语言模型进行开发。” 这样大约95个字左右,符合要求。 </think> Arkanix Stealer是一款由AI辅助开发的信息窃取恶意软件,在2025年底通过暗网论坛推广。该软件分为基础版和高级版,具备数据窃取、传播及反分析功能。开发者两个月后关闭相关服务。卡巴斯基研究发现其使用大语言模型进行开发。 2026-2-22 15:45:16 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

An information-stealing malware operation named Arkanix Stealer, promoted on multiple dark web forums towards the end of 2025, was likely developed as an AI-assisted experiment.
The project included a control panel and a Discord server for communication with users, but the author took them down without notification, just two months after the operation began.
Arkanix offered many of the standard data-stealing features that cybercriminals are used to, along with a modular architecture and anti-analysis features.
Kaspersky researchers analyzed the Arkanix stealer and found clues indicating LLM-assisted development, which "might have drastically reduced development time and costs."
Source: Kaspersky
The researchers believe that Arkanix was a short-lived project for quick financial gains, which makes detection and tracking much more difficult.
Arkanix appears online
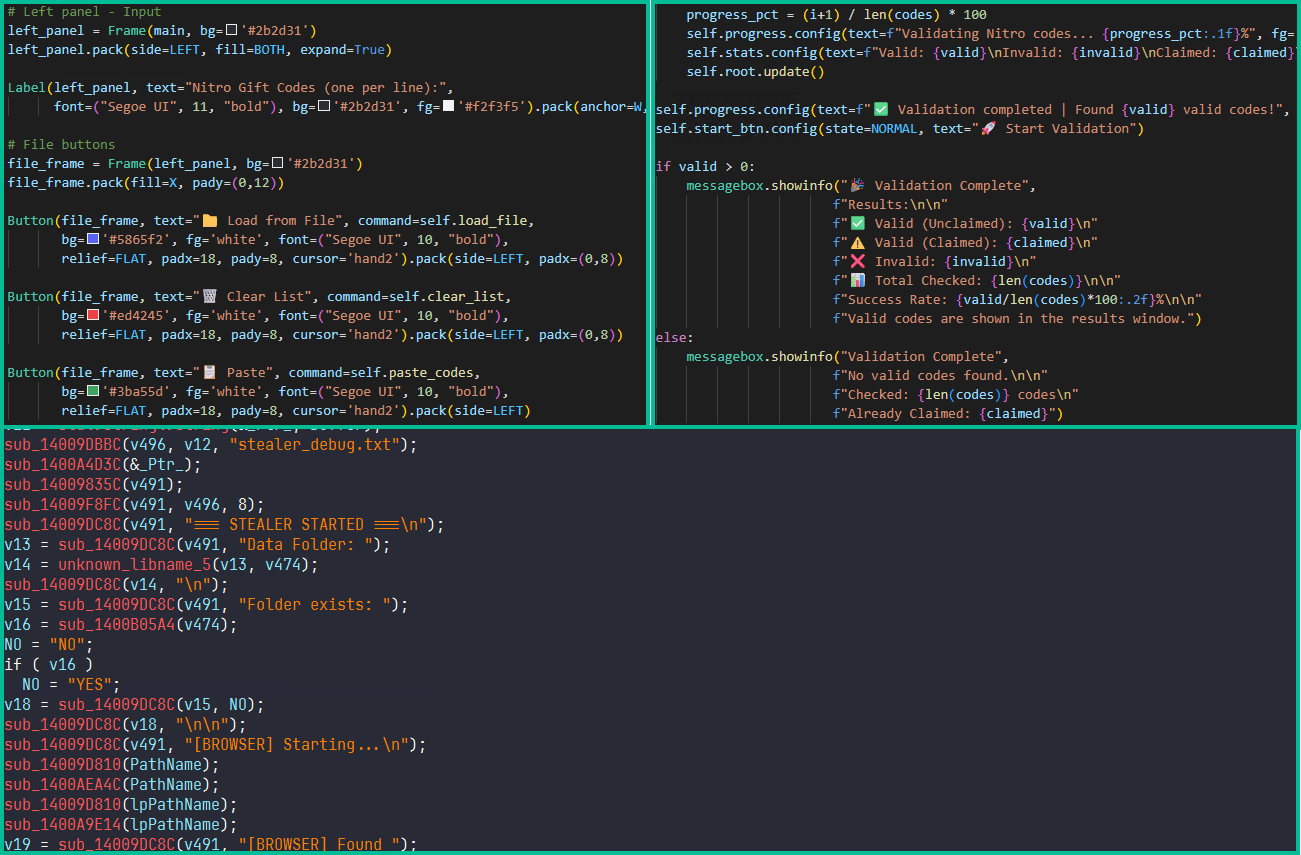
Arkanix started being promoted on hacker forums in October 2025, offering two tiers to potential customers: a basic level with a Python-based implementation, and a “premium” one with a native C++ payload using VMProtect protection, integrating AV evasion and wallet injection features.
Source: Kaspersky
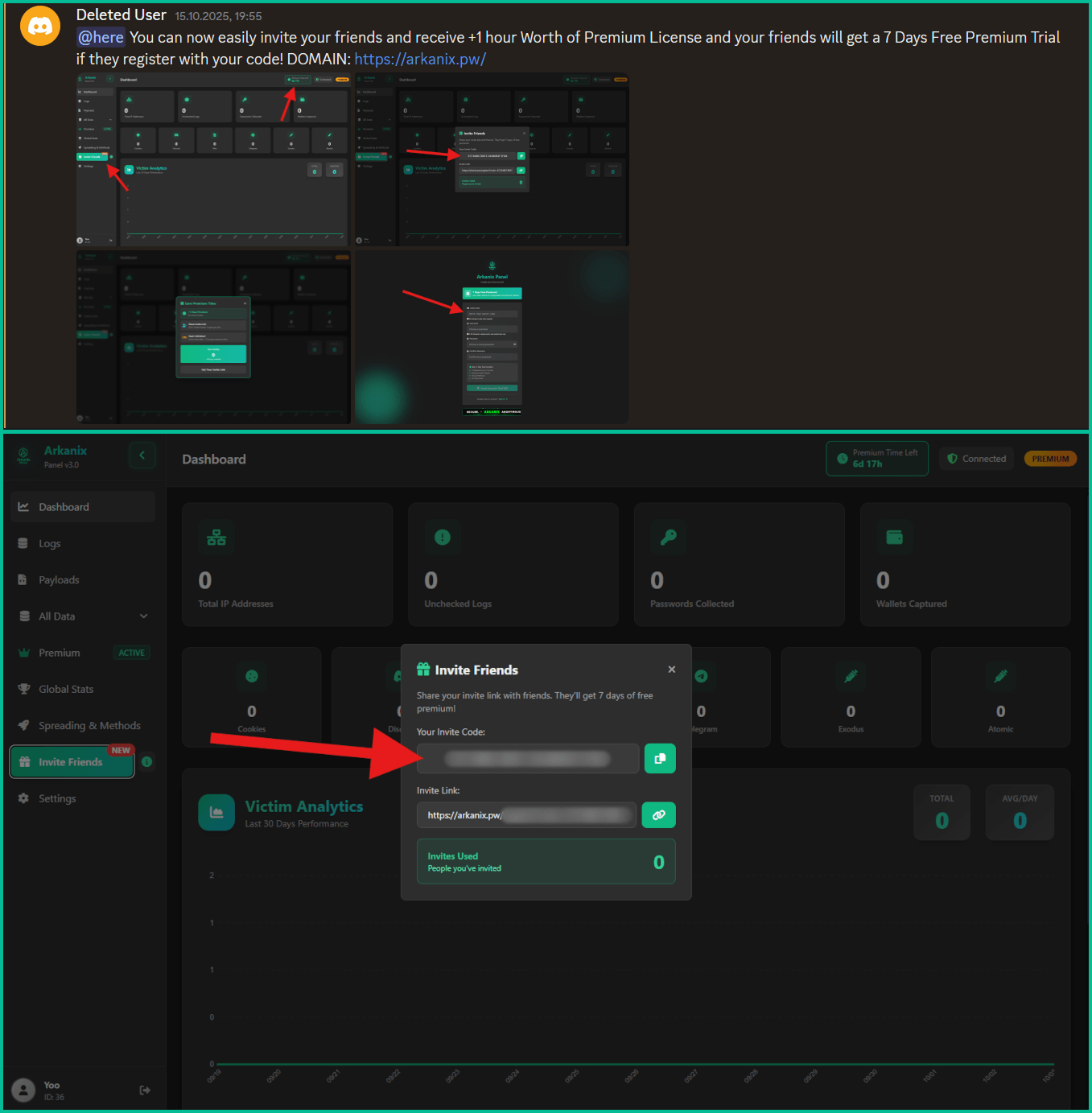
The developer set up a Discord server that acted as a forum for the community around the project to receive updates, provide feedback for proposed features, and receive help.
Also, a referral program was established to promote the project more aggressively, giving referrers an extra free hour of premium access, while potential new customers received one week of free access to the “premium” version.
Source: Kaspersky
Data-stealing capabilities
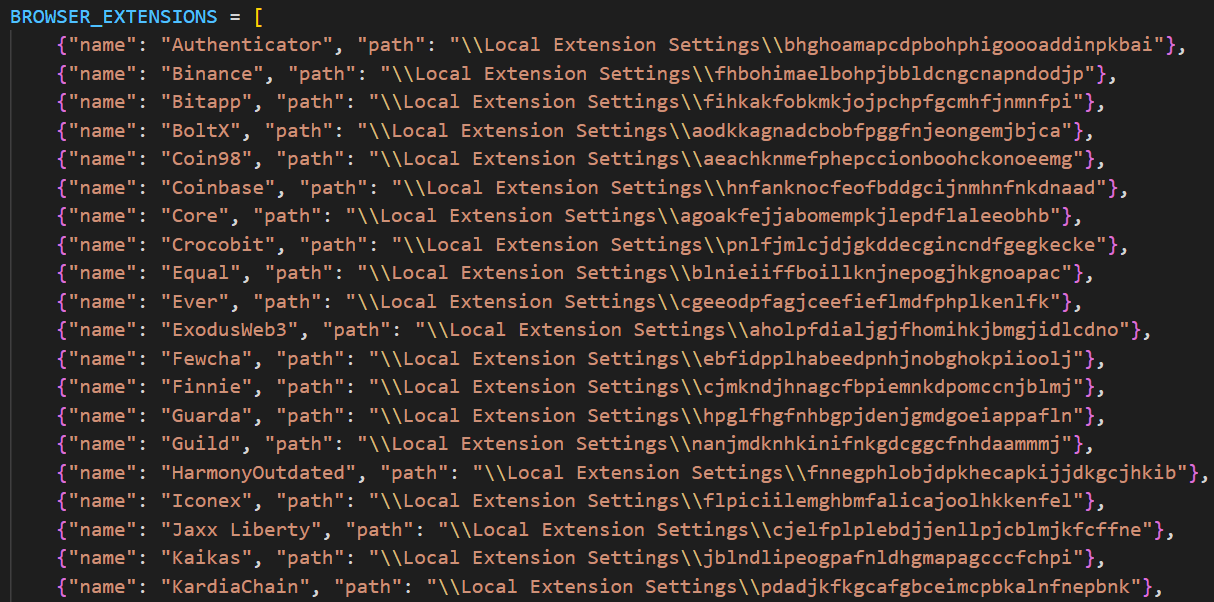
Arkanix malware can collect system information, steal data stored in the browser (history, autofill info, cookies, passwords), and cryptocurrency wallet data from 22 browsers. Kaspersky researchers say that it can also extract 0Auth2 tokens on Chromium-based browsers.
Additionally, the malware can steal data from Telegram, steal Discord credentials, spread via the Discord API, and send messages to the victim’s friends/channels.
Arkanix also targets credentials for Mullvad, NordVPN, ExpressVPN, and ProtonVPN, and can archive files from the local filesystem to exfiltrate them asynchronously.
Additional modules that can be downloaded from the command-and-control include a Chrome grabber, a wallet patcher for Exodus or Atomic, a screenshots tool, HVNC, and stealers for FileZilla and Steam.
Source: Kaspersky
The “premium” native C++ version adds RDP credential theft, anti-sandbox and anti-debugging checks, WinAPI-powered screen capturing, and also targets Epic Games, Battle.net, Riot, Unreal Engine, Ubisoft Connect, and GOG.
The higher-tier variant also delivers the ChromElevator post-exploitation tool, which injects into suspended browser processes for data theft and is designed to bypass Google's App-Bound Encryption (ABE) protection for unauthorized access to user credentials.
The purpose of the Arkanix stealer experiment remains unclear. The project may be an attempt to determine how LLM assistance can improve malware development and how quickly new features can be shipped to the community.
Kaspersky's assessment is that Arkanix is "more of a public software product than a shady stealer."
The researchers provide a comprehensive list of indicators of compromise (IoCs) that include hashes for detected files, along with domains and IP addresses.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
如有侵权请联系:admin#unsafe.sh

