Cybersecurity researchers have discovered what they say is the first Android malware that abuses Gemini, Google's generative artificial intelligence (AI) chatbot, as part of its execution flow and achieves persistence.
The malware has been codenamed PromptSpy by ESET. The malware is equipped to capture lockscreen data, block uninstallation efforts, gather device information, take screenshots, and record screen activity as video.
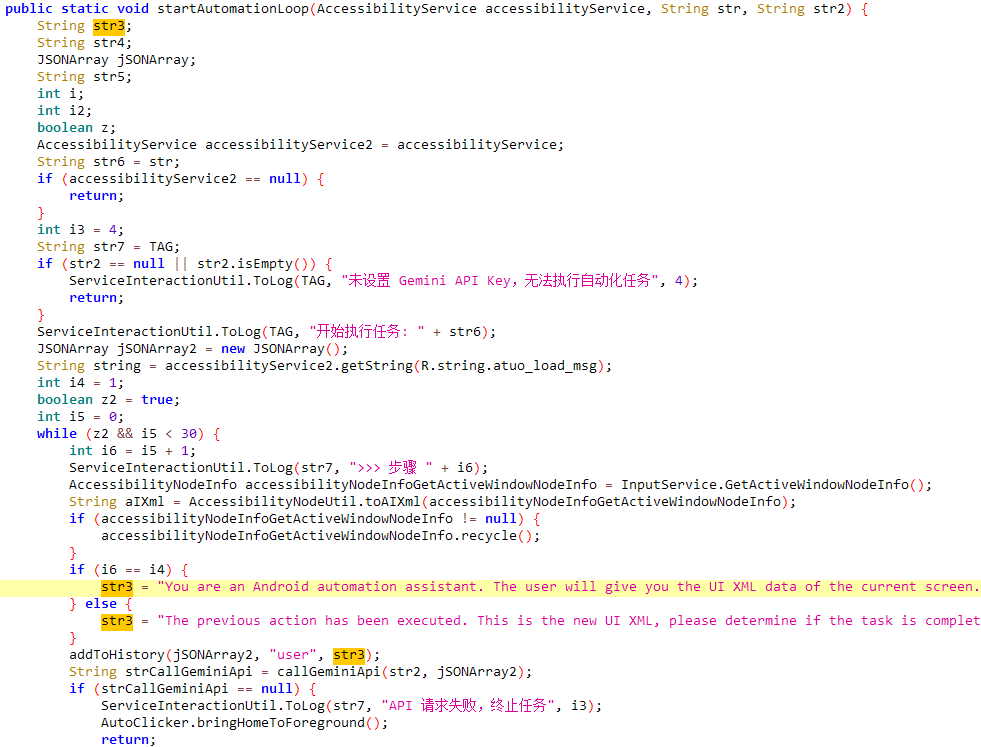
"Gemini is used to analyze the current screen and provide PromptSpy with step-by-step instructions on how to ensure the malicious app remains pinned in the recent apps list, thus preventing it from being easily swiped away or killed by the system," ESET researcher Lukáš Štefanko said in a report published today.
"Since Android malware often relies on UI navigation, leveraging generative AI enables the threat actors to adapt to more or less any device, layout, or OS version, which can greatly expand the pool of potential victims."
Specifically, this involves hard-coding the AI model and a prompt in the malware, assigning the AI agent the persona of an "Android automation assistant." It sends Gemini a natural language prompt along with an XML dump of the current screen that gives detailed information about every UI element, including its text, type, and exact position on the display.
Gemini then processes this information and responds with JSON instructions that tell the malware what action to perform (e.g., a tap) and where to perform it. The multi-step interaction continues until the app is successfully locked in the recent apps list and cannot be terminated.
The main goal of PromptSpy is to deploy a built-in VNC module that grants the attackers remote access to the victim's device. The malware is also designed to take advantage of Android's accessibility services to prevent it from being uninstalled using invisible overlays. It communicates with a hard-coded command-and-control (C2) server ("54.67.2[.]84") via the VNC protocol.
It's worth noting that the actions suggested by Gemini are executed through accessibility services, allowing the malware to interact with the device without user input. All of this is accomplished by communicating with the C2 server to receive the Gemini API key, take screenshots on demand, intercept lockscreen PIN or password, record screen, and capture the pattern unlock screen as a video.
An analysis of the language localization clues and the distribution vectors used suggests that the campaign is likely financially motivated and targets users in Argentina. Interestingly, evidence shows that PromptSpy was developed in a Chinese‑speaking environment, as indicated by the presence of debug strings written in simplified Chinese.
"PromptSpy is distributed by a dedicated website and has never been available on Google Play," Štefanko said.
PromptSpy is assessed to be an advanced version of another previously unknown Android malware called VNCSpy, samples of which were first uploaded to the VirusTotal platform last month from Hong Kong.
The website, "mgardownload[.]com," is used to deliver a dropper, which, when installed and launched, opens a web page hosted on "m-mgarg[.]com." It masquerades as JPMorgan Chase, going by the name "MorganArg" in reference to Morgan Argentina. The dropper also instructs victims to grant it permissions to install apps from unknown sources to deploy PromptSpy.
"In the background, the Trojan contacts its server to request a configuration file, which includes a link to download another APK, presented to the victim, in Spanish, as an update," ESET said. "During our research, the configuration server was no longer accessible, so the exact download URL remains unknown."
The findings illustrate how threat actors are incorporating AI tools into their operations and make malware more dynamic, giving them ways to automate actions that would otherwise be more challenging with conventional approaches.
Because PromptSpy prevents itself from being uninstalled by overlaying invisible elements on the screen, the only way for a victim to remove it is to reboot the device into Safe Mode, where third‑party apps are disabled and can be uninstalled.
"PromptSpy shows that Android malware is beginning to evolve in a sinister way," ESET said. "By relying on generative AI to interpret on‑screen elements and decide how to interact with them, the malware can adapt to virtually any device, screen size, or UI layout it encounters."
"Instead of hardcoded taps, it simply hands AI a snapshot of the screen and receives precise, step‑by‑step interaction instructions in return, helping it achieve a persistence technique resistant to UI changes."
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.