嗯,用户让我帮忙总结一篇文章,控制在一百个字以内,而且不需要用“文章内容总结”这样的开头。首先,我需要仔细阅读这篇文章,理解它的主要观点。 文章主要讲的是如何有效管理网络攻击面的暴露风险。它提到了一个成熟度模型,分为五个阶段,帮助组织从被动应对转向主动防御。每个阶段都有具体的特征和痛点,以及如何提升到更高阶段的建议。 用户的需求是总结内容,所以我要抓住关键点:暴露管理、五个成熟度阶段、从被动到主动防御的转变。然后用简洁的语言把这些点整合起来,确保在一百字以内。 可能需要注意的是,不要遗漏成熟度模型的重要性以及它如何帮助组织提升安全能力。同时,要避免使用复杂的术语,让总结更易懂。 最后,检查一下字数和是否符合用户的要求,确保没有使用任何开头模板。 </think> 文章介绍了如何通过成熟度模型实现主动防御的网络安全策略,强调从被动响应到主动风险管理的转变,并通过五个阶段帮助企业逐步提升暴露管理能力。 2026-2-19 17:0:0 Author: www.microsoft.com(查看原文) 阅读量:3 收藏
Effective exposure management begins by illuminating and hardening risks across the entire attack surface. Some of the most meaningful shifts in security happen quietly—when teams take a clear look at their exposure landscape and acknowledge the gap between where they stand today and where they need to be. Today, we’re sharing a new guide designed to support that moment of clarity. It offers a practical, maturity-based path for moving from fragmented visibility and reactive fixes to a more unified, risk-driven approach that strengthens resilience one step at a time. Read “Establishing proactive defense—A maturity-based guide for adopting a dynamic, risk-based approach to exposure management” to learn more now.

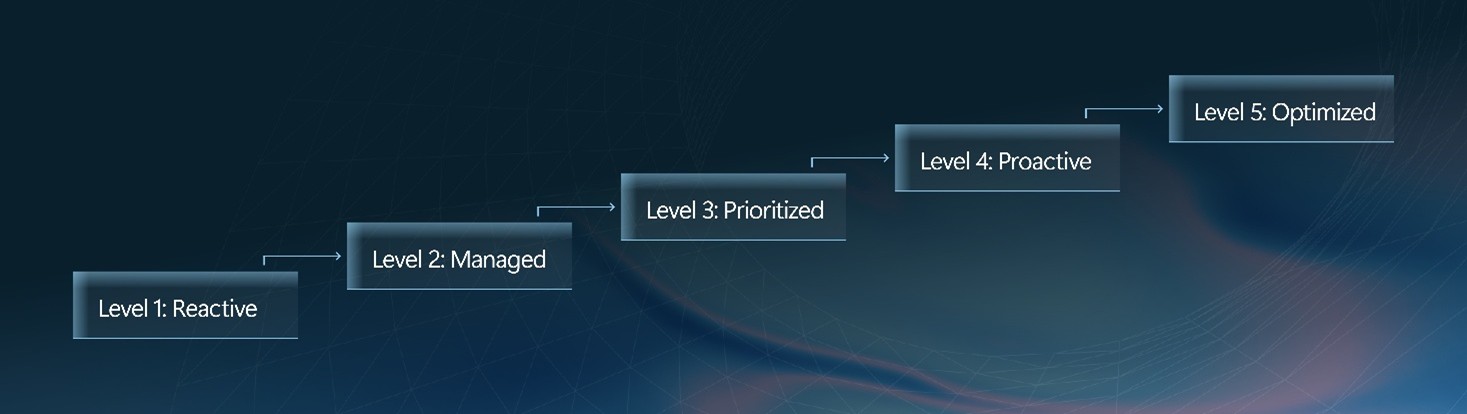
Five levels of exposure management maturity
In the guide, you’ll learn how organizations progress through five levels of exposure management maturity to strengthen how they identify, prioritize, and act on risk. Early-stage teams operate reactively with limited visibility and compliance-driven fixes. As capabilities mature, processes become consistent, prioritization incorporates business context, and decisions shift from reactive to proactive. This progression reflects a move away from isolated security actions toward repeatable, measurable practices that scale with organizational complexity. At higher maturity, organizations validate controls, consolidate asset and risk data into a single source of truth, and confirm that mitigations work. Rather than assuming security improvements are effective, teams test and verify outcomes to ensure effort translates into real risk reduction. At the most advanced stage, exposure management is fully aligned to business objectives, supported by clear risk metrics, and used to guide remediation, resource allocation, and strategic outcomes.
The maturity model helps security leaders assess where their organization is at and identify practical next steps to mature and have a full-fledged exposure management program. Each level in the guide includes details on the realities organizations face, the key characteristics at each maturity level, common pain points, and suggestions for moving forward and up in maturity. Importantly, the model emphasizes that maturity is not static or final. The last stage of the maturity model, level five, isn’t a finish line—it’s the point where exposure management becomes a continuously evolving capability, fueled by real-time telemetry and adaptive risk modeling. At this stage, exposure management shifts from a program to a strategic discipline—one that informs long-term resilience decisions rather than discrete remediation cycles.
The path to proactive defense
Organizations build a unified path to proactive defense when they move beyond fragmented tools and adopt an integrated exposure management approach. By bringing assets, identities, cloud posture, and attack paths into one coherent view, security teams gain the clarity needed to focus effort where it matters most. This alignment enables more consistent action, stronger prioritization, and security decisions that reflect real business risk instead of isolated signals. It also helps teams move from chasing individual findings to managing exposure systematically, with shared context across security, IT, and risk stakeholders. Over time, this shift turns exposure management into a repeatable operating model rather than a collection of disconnected responses.
Take the next step toward proactive defense
Designed to help security leaders translate strategy into practical next steps, regardless of where they are starting, the maturity levels outlined in the e-book support organizations as they shift from reacting to cyberthreats to proactively reducing risk and strengthening security across every layer of the environment. To go deeper into the practices, maturity levels, and actions that matter most, read the new e-book: Establishing a proactive defense—A maturity-based guide for adopting a dynamic, risk-based approach to exposure management to learn more now.
Join us at RSAC™ 2026
RSAC™ 2026 is more than a conference. It’s a chance to shape the future of security. By engaging with Microsoft Security, you’ll gain:
- Actionable insights from industry leaders and researchers.
- Hands-on experience with cutting-edge security tools.
- Connections that help you navigate the evolving cyberthreat landscape.
Together, we can make the world safer for all. Join us in San Francisco March 22-26, 2026, and be part of the conversation that defines the next era of cybersecurity.
Learn more
Learn more about Microsoft Security Exposure Management.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
如有侵权请联系:admin#unsafe.sh