
好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内,并且不需要特定的开头。首先,我得仔细阅读文章,理解主要信息。 文章讲的是Iron Mountain公司最近遭受了网络攻击,被Everest勒索团伙声称窃取了1.4TB的内部文件。不过Iron Mountain回应说,攻击者只是用了一个被破解的账户访问了一个存储营销材料的文件夹,并没有涉及客户敏感信息,也没有部署勒索软件或其他恶意软件。 接下来,我需要提取关键点:Iron Mountain是数据存储和恢复服务的领导者,Everest声称窃取了大量文件,但Iron Mountain澄清攻击范围有限,主要影响营销材料,没有客户数据泄露,也没有系统被入侵。 然后,我需要把这些信息浓缩到100字以内。要注意用词简洁明了,避免冗余。可能的结构是先点明事件,然后说明Iron Mountain的回应和具体情况。 最后检查一下字数是否符合要求,并确保没有遗漏重要信息。 </think> Iron Mountain回应Everest勒索团伙声称窃取其1.4TB内部文件的说法,称攻击仅限于营销材料文件夹,未涉及客户敏感信息或系统入侵。 2026-2-3 17:0:32 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

Iron Mountain, a leading data storage and recovery services company, says that a recent breach claimed by the Everest extortion gang is limited to mostly marketing materials.
Headquartered in Portsmouth, New Hampshire, and founded in 1951, Iron Mountain specializes in data centers and records management, and has over 240,000 customers worldwide from more than 61 countries, including 95% of the Fortune 1000.
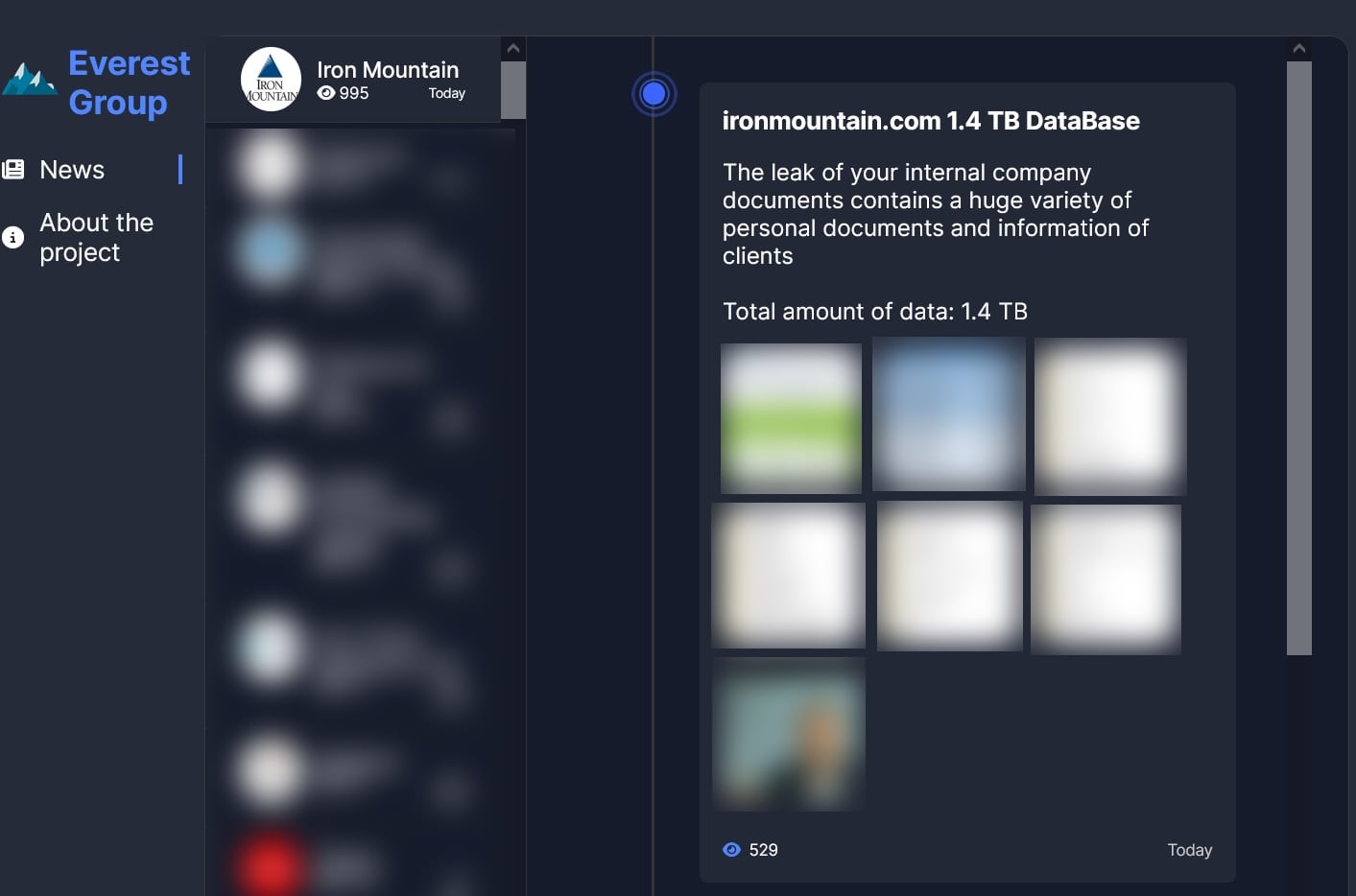
The company's statement comes after the cybercrime group claimed on its dark web leak site that it had stolen 1.4 TB of "internal company documents" containing "personal documents and information on clients."
However, Iron Mountain told BleepingComputer that the attackers used compromised credentials to access a single folder on a file-sharing server storing marketing materials.
It also added that the Everest operators didn't deploy any ransomware payloads on the server, and no other Iron Mountain systems were breached in the incident.
"No customer confidential or sensitive information has been involved. A single compromised login credential was used to gain access to one folder, consisting primarily of marketing materials shared with third-party vendors on a public-facing file-sharing site," the company told BleepingComputer.
"At this time, we also confirm that no Iron Mountain systems have been breached, and there is no ransomware or malware involvement, or any other cyber activity, beyond the compromised folder credential, which has since been deactivated."
Since it surfaced in 2020, the Everest ransomware group has shifted tactics from encrypting victims' systems with ransomware to data-theft-only corporate extortion.
Everest is also known for acting as an initial access broker for other threat actors and cybercrime gangs, selling access to breached corporate networks for a fee.
Over the last 5 years, Everest has added hundreds of victims to its leak portal, which is used in double-extortion attacks in which the threat actors threaten to publish stolen files unless victims pay ransoms.
In August 2024, the U.S. Department of Health and Human Services also warned that Everest was increasingly targeting healthcare organizations across the United States.
More recently, the cybercrime operation took down its website in April 2025 after it was defaced and its contents replaced with the "Don't do crime CRIME IS BAD xoxo from Prague" message.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
如有侵权请联系:admin#unsafe.sh

