ANY.RUN observes a growing trend of phishing kit infrastructure being hosted on legitimate cloud and CDN platforms, rather than on newly registered domains. These campaigns often target enterprise users specifically, creating a global threat to businesses. The shift createsserious visibility challenges for security teams, as trusted platforms and valid indicators shield malicious activity from detection.
For a deeper dive, read on and see the breakdown of such cases, along with tips on what works and what doesn’t.
Key Takeaways
- Modern phishing campaigns increasingly rely on trusted cloud infrastructure, not disposable domains.
- AiTM phishing kits dominate enterprise-targeted attacks.
- Cloudflare, Microsoft Azure, Google Firebase, and AWS are frequently abused.
- Traditional IOCs like IPs, TLS fingerprints, and certificates are becoming unreliable.
- Continuous threat intelligence and behavioral analysis are critical for detection.
Enterprises Under Fire: AITM kits and Cloudflare Abuse
The most widespread and dangerous phishing campaigns today are powered by AiTM (Adversary-in-the-middle kits). These toolsets help unfold phishing attacks where threat actors become a proxy between the victim and a legitimate service.
- Follow ANY.RUN’s team on X to get weekly updates on the most widespread phishing kits
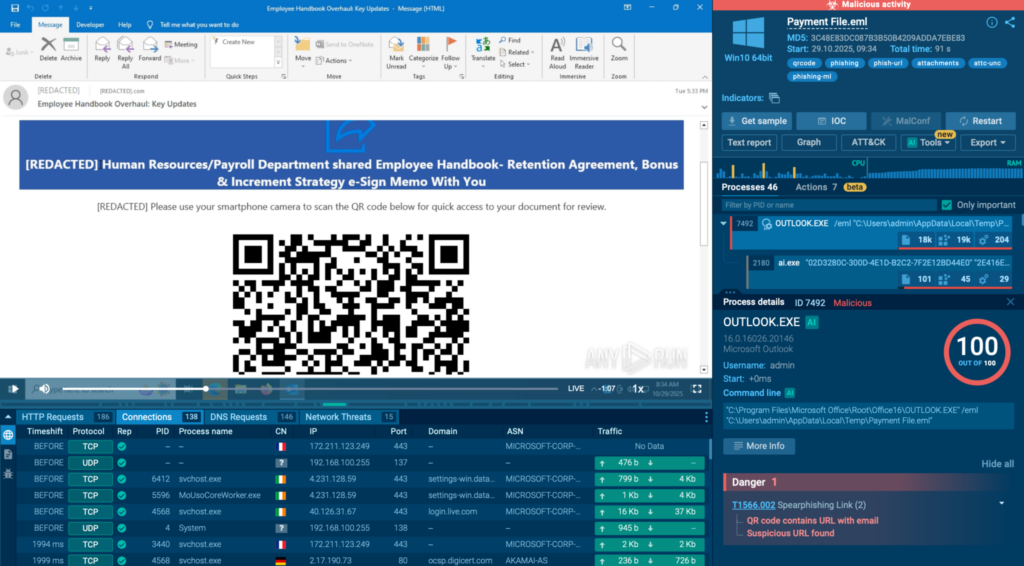
A typical phishkit attack starts with an email containing a link (including in the form of a QR code) leading to attackers’ infrastructure. Most campaigns also involve a CAPTCHA challenge and a string of redirects as a means to avoid detection by AVs and static systems.Advanced evasion leads to a high rate of missed attacks for organizations that suffer from data theft as a result of this.
ANY.RUN’s Interactive Sandbox provides security teams with the capabilities to quickly detect phishkit attacks thanks to interactive analysis. In addition to static detection, the sandbox lets SOC analysts safely follow the entire attack chain in an isolated VM and go past all the evasion layers to reveal the final malicious credential theft page or payload.
The result for businesses that have adopted ANY.RUN’s solutions in their infrastructure is a lower risk of a data breach and a more effective SOC team that can quickly identify phishing attempts with a high degree of certainty.
The top three most active phishing kits remain stable quarter to quarter. The list features:
- Tycoon2FA: Phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA).
- Sneaky2FA: Adversary-in-the-Middle (AiTM) threat used in Business Email Compromise (BCE) attacks.
- EvilProxy: Reverse-proxy phishing kit, often used for account takeover attacks aimed at high-ranking executives.
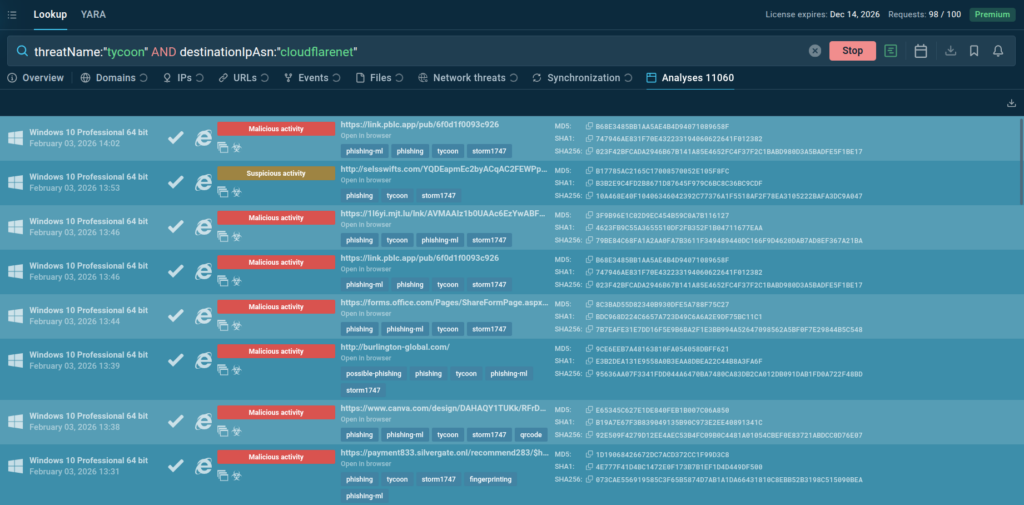
Mostly these campaigns are hosted behind Cloudflare CDN infrastructure. You can find live examples using Threat Intelligence Lookup with queries like these:
threatName:”tycoon” AND destinationIpAsn:”cloudflarenet”
Use TI Lookup to strengthen alert triage and proactive threat hunting:
- Accelerate detection and response: Correlate alerts with real-time threat intelligence to reduce triage time and missed threats.
- Improve threat visibility: Gain deeper insight into emerging malware and attack trends across industries.
- Stay ahead of risk: Proactively monitor relevant threats with automated alerts and expert intelligence reports.
Why Treat Actors Choose Cloudflare
For threat actors, Cloudflare abuse offers critical advantages:
- Complicated detection: Cloudflare operates as both a CDN and reverse proxy. The real origin server (often a VPS) gets hidden behind Cloudflare’s IP addresses. SOC analysts only see trusted Cloudflare ASN, valid HTTPS, and ordinary CDN traffic. The original IP can’t be scanned, blocked, or easily linked to other campaigns.
- Resistance to blocking and takedowns: Cloudflare’s IPs are nearly impossible to block without significant disruption. If a malicious domain is taken down, threat actors can register a new own right away and hide it behind Cloudflare just the same, without changing the basic infrastructure.
- Built-in anti-analysis techniques: Even in mass mailing cases, the CDN helps sustain the activity and lowers the risk of VPS’s takedown. It also provides easy-to-use anti-analysis and access control techniques, such as CAPTCHA, Turnstile, geo fencing, ASN and User-Agent filtering, and blocking of automated scanners and sandboxes.
Because TLS termination happens at Cloudflare, SSL certificates and TLS session’s fingerprints like JA3S lose value as indicators for SOC analysts. IP- and TLS-based detection becomes inefficient, and the only remaining leads for analysts are domains and their reputation.
Implications and Recommendations for Decison-Makers
- Attackers increasingly rely on trusted platforms to evade detection, reflecting cloud-based phishing growth to a mainstream technique.
- In many cases, there’s a clear intent to target large companies specifically.
- Traditional detection methods and static IOCs aren’t sufficient for a strong defense strategy.
- Effective detection requires non-stop monitoring of phishing campaigns, as well as constantly updated signature databases.

Interactive sandboxing combined with threat intelligence solutions enable analysts to uncover evasive phishing threats and helps achieve:
- Early warning through global intelligence: Learn from real-world incidents across industries to anticipate threats before they reach your organization.
- Faster, more confident triage: Enrich alerts with proven historical evidence to reduce false positives and unnecessary escalations.
- Deeper visibility into real threats: Observe malicious behavior as it unfolds to uncover evasive techniques that static analysis often misses.
- Operational efficiency at scale: Eliminate manual correlation across multiple sources and streamline investigations within a single workflow.
- Stronger SOC performance: Support analysts at all levels while accelerating the full security operations lifecycle, from detection to response.
| The result is measurable: |
|---|
| +62.7% more threats detected overall |
| 94% of surveyed users report faster triage |
| 63% year-over-year user growth, driven by analyst efficiency |
| 30% fewer alerts require escalation to senior analysts |
Modern Phishing: No Longer Seen by the Naked Eye
Until recently, a typical phishing attack looked like this:
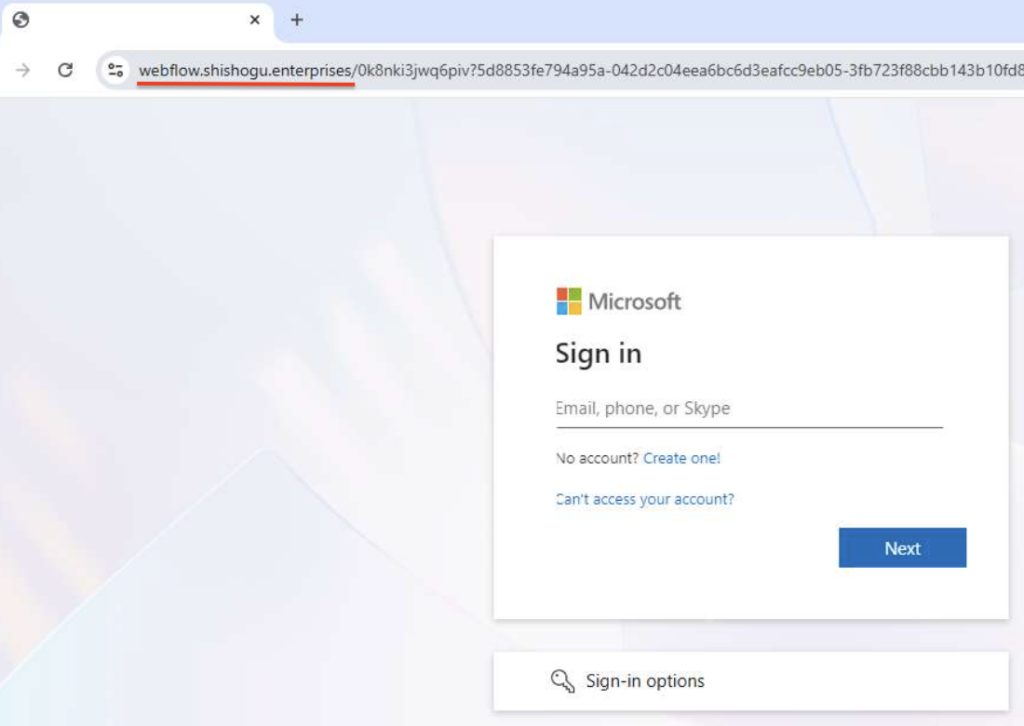
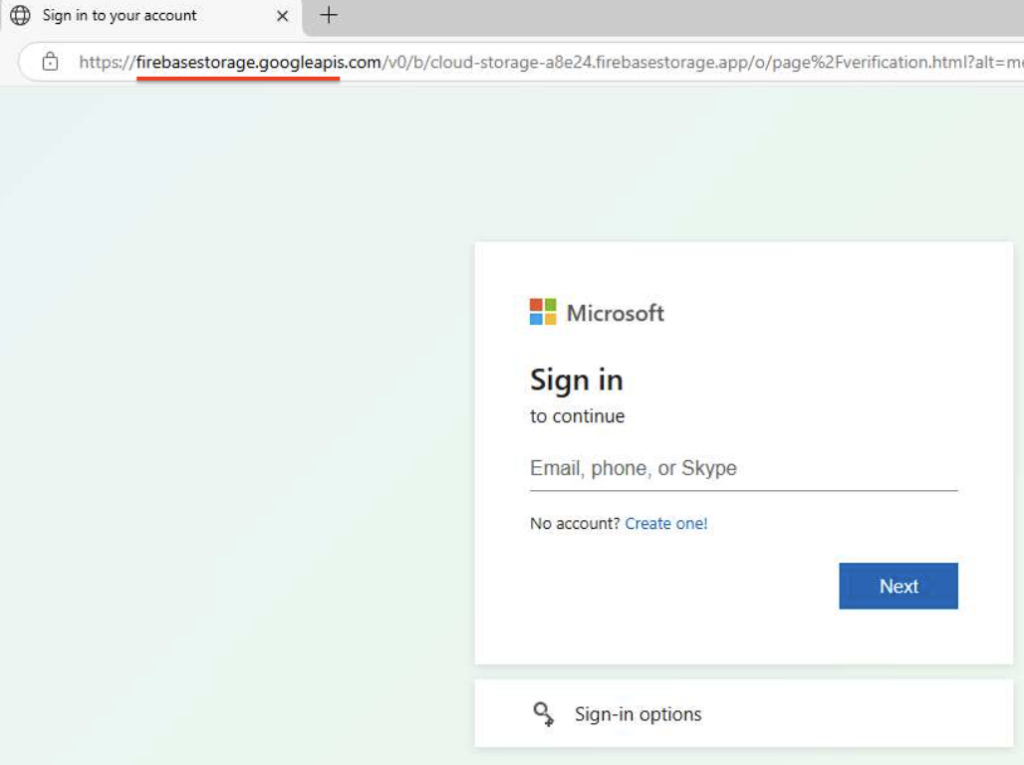
As shown above, the login form is hosted on a newly registered domain, not legitimate Microsoft 365 one (e.g., windows[.]net, microsoftonline[.]com, office[.]net, or live[.]com). This clearly indicates phishing.
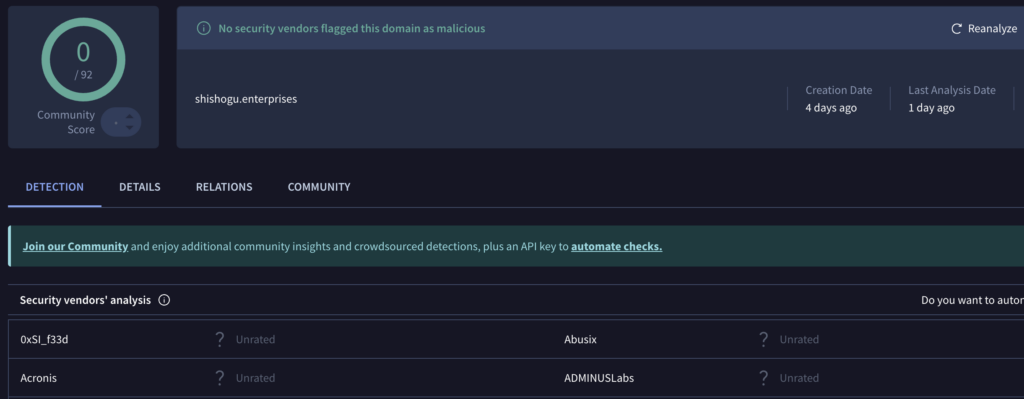
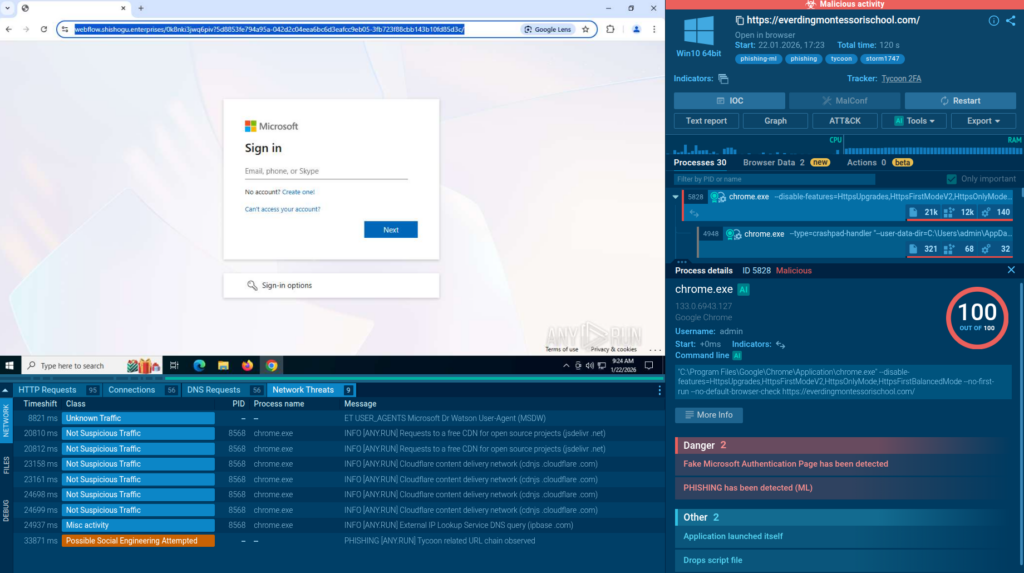
But modern phishing threats are significantly more complex and therefore dangerous. In many cases, even the domain name stops being a reliable IOC. That’s what can be observed in this sample:
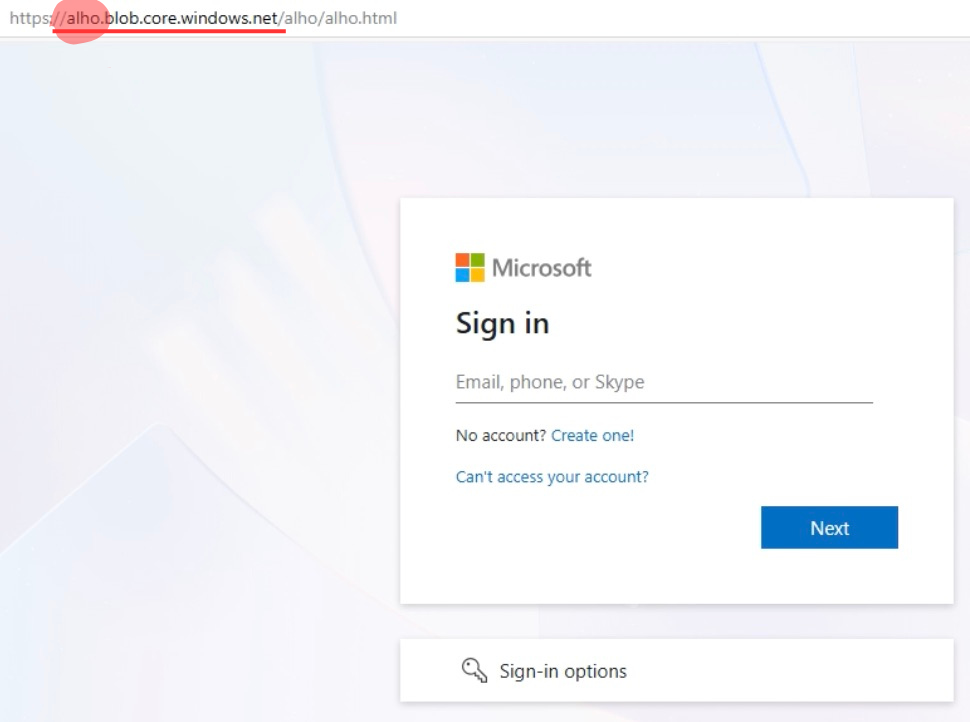
In this analysis, login form is hosted on legitimate Microsoft Azure Blob Storage, complicating the chance of detection. This sample belongs to Tycoon2FA, which we’ve discussed in detail in this article.
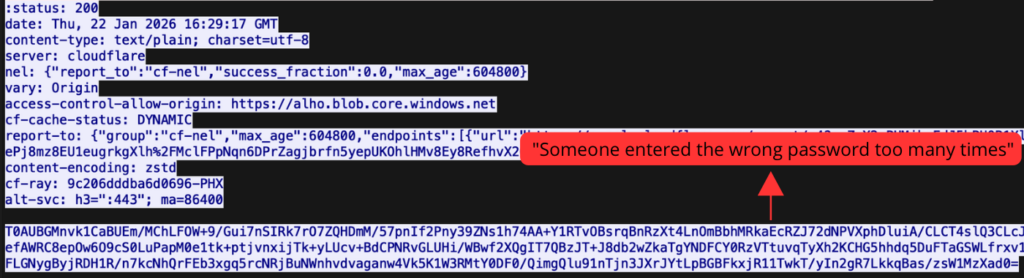
In the POST request below, the victim’s encrypted password is transmitted from Microsoft Azure page to an attacker-controlled server:
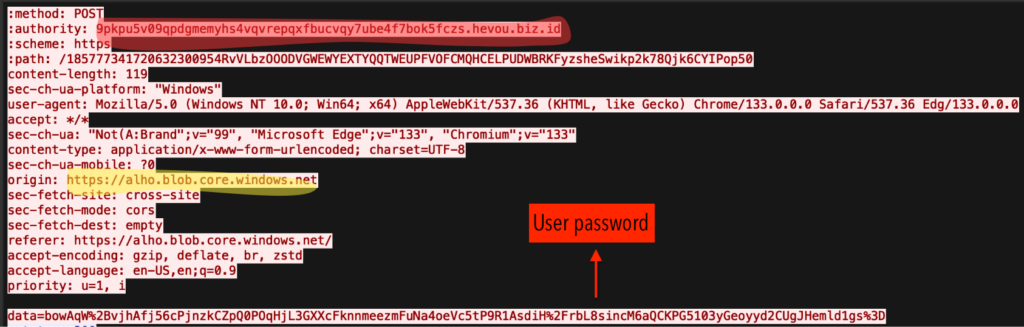
The response from a malicious reserve proxy returns a “wrong password” message, mimicking Microsoft’s legitimate authentication flow.
Trends: Rapid Growth of Cloud-Hosted Threats
At the time of writing, it’s been a week the previous publication of these findings. Since then, the amount of similar phishing cases has nearly doubled.
You can find examples of this trend on TI Lookup:
threatName:”tycoon” AND domainName:”*.blob.core.windows.net”
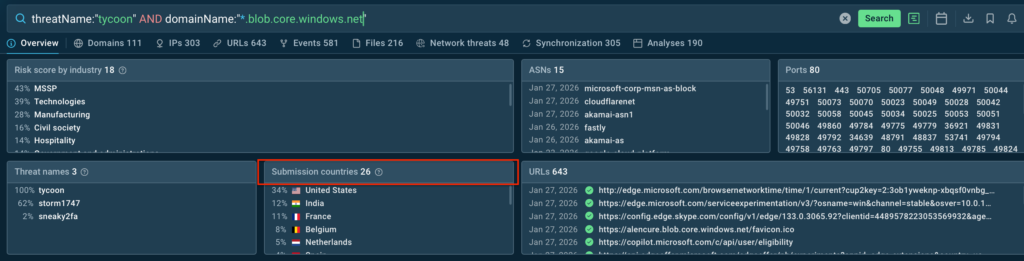
On average, SOC teams from the US and Europe encounter Tycoon-based phishing abusing trusted Microsoft infrastructure multiple times a day, indicating a growing rise in their activity.
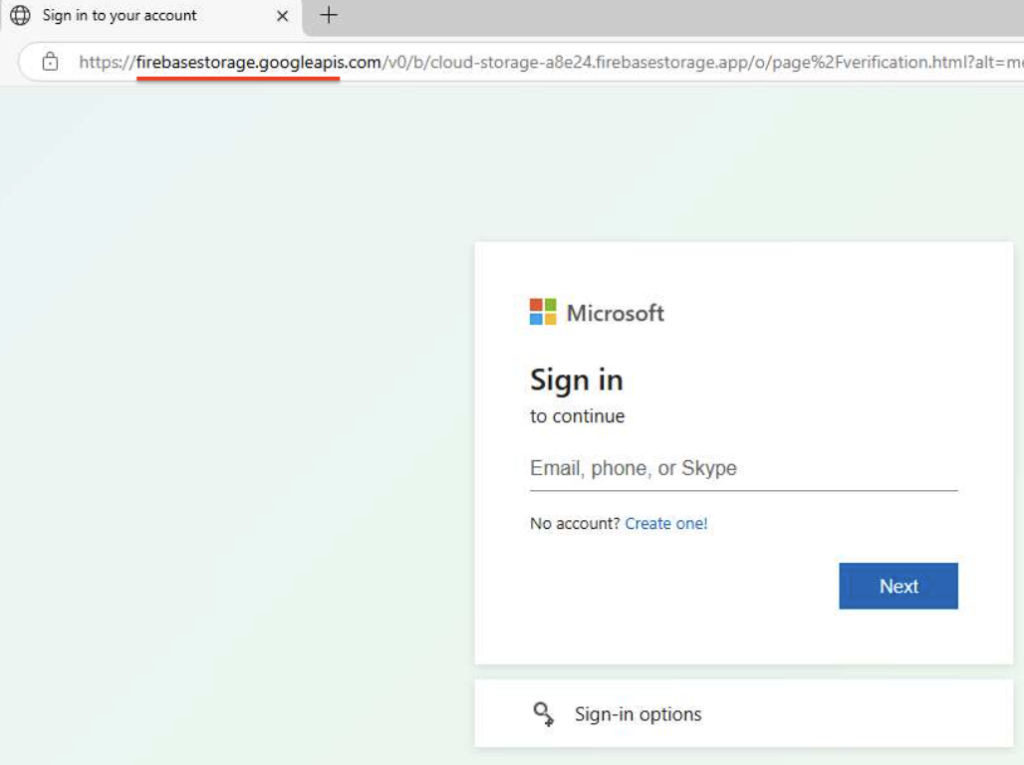
Sneaky2FA Targeting Enterprises
Similar behavior is observed in Sneaky2FA campaigns, commonly hosted at Google Firebase Storage:
As well as at AWS CloudFront:
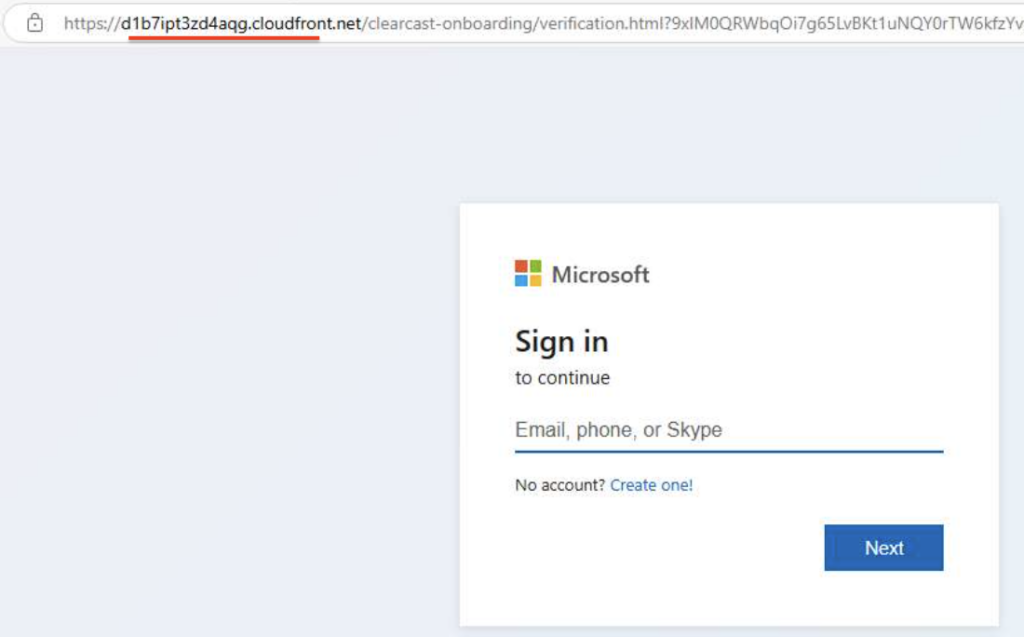
What differentiates Sneaky2FA from Tycoon2FA is its focus on large companies, not mass campaigns. The kit excludes free personal email addresses hosted on gmail.com, yahoo.com, and outlook.com, focusing only on corporate emails.
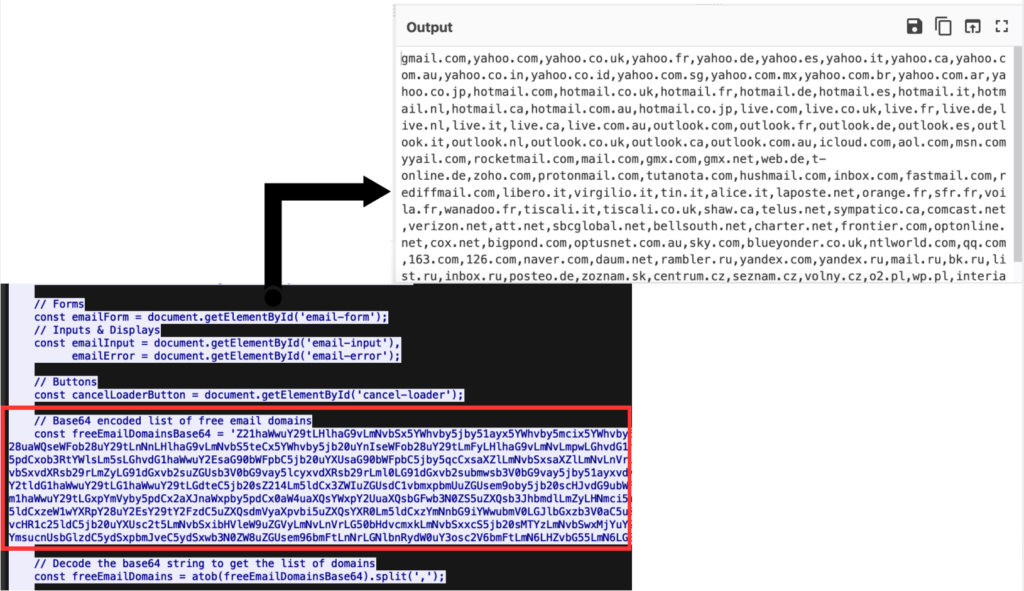
EvilProxy: Different Threat, Same Method
In addition to Tycoon2FA and Sneaky2FA, EvilProxy also demonstrates similar abuse of trusted cloud platforms:
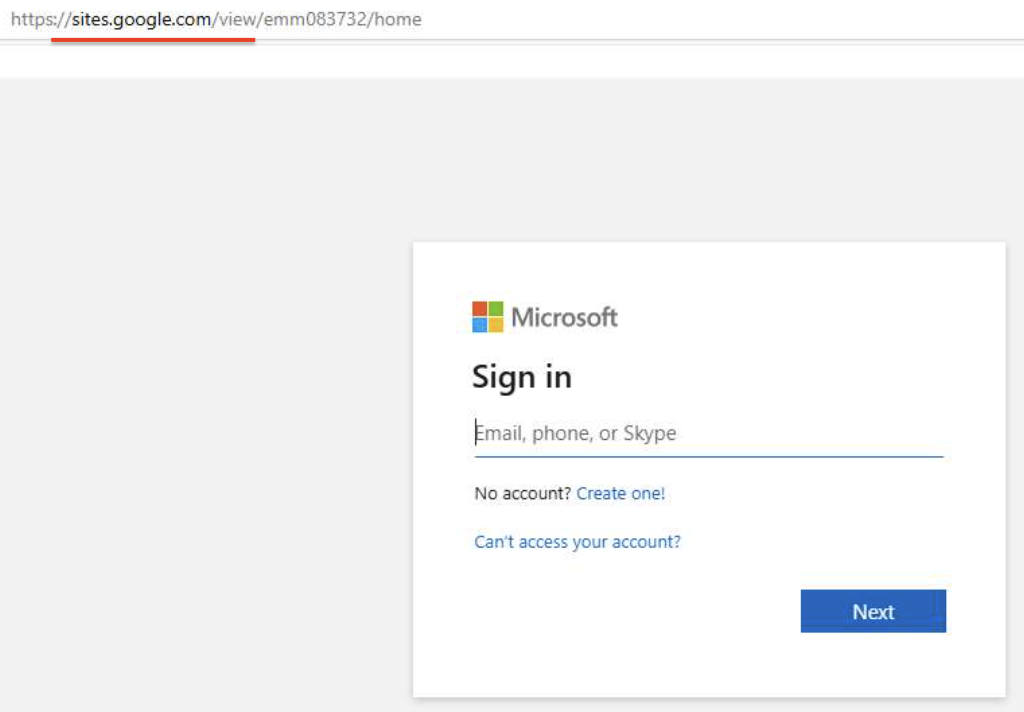
The underlying strategy is similar and involves hiding malicious activity behind legitimate infrastructure.
Cephas: Beyond Mainstream
Another example of a Microsoft 365 phishing abusing a trusted cloud infrastructure was found among less common phishkits, such as Cephas.
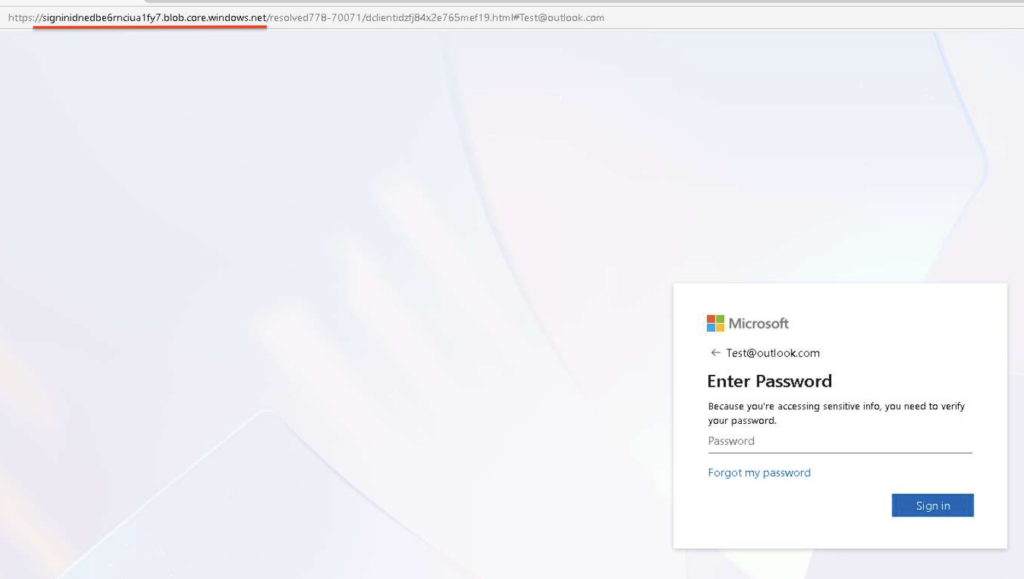
This confirms the trend, which solidifies cloud platform abuse as a standard technique, not a one-off case.
To find more phishing domains based on Microsoft Azure, use the following TI Lookup query:
threatName:”phishing” AND domainName:”*blob.core.windows.net”
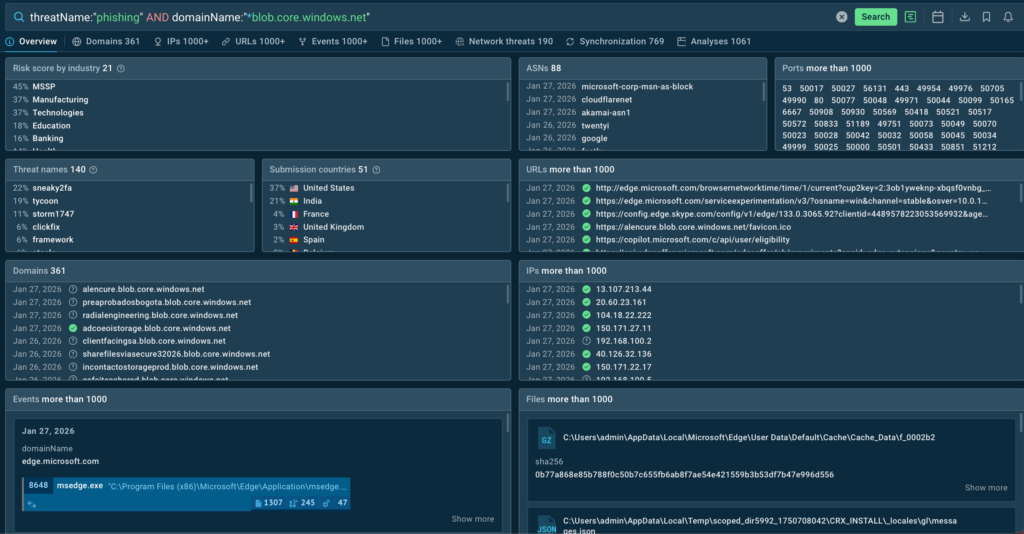
Phishing hosted on trusted cloud infrastructure is becoming increasingly widespread. The risk for large organizations grows daily, and detecting this type of attacks at early stages is made possible through continuous monitoring of phishing campaigns.
ANY.RUN provides this visibility by delivering continuous signature updates and empowering SOC teams in 195 countries to detect sophisticated phishing threats for maximum business protection.
About ANY.RUN
ANY.RUN develops advanced solutions for malware analysis and threat hunting, trusted by 600,000+ cybersecurity professionals worldwide.
Its interactive malware analysis sandbox enables hands-on investigation of threats targeting Windows, Linux, and Android environments. ANY.RUN’s Threat Intelligence Lookup and Threat Intelligence Feeds help security teams quickly identify indicators of compromise, enrich alerts with context, and investigate incidents early. Together, the solutions empowers analysts to strengthen overall security posture at enterprises.
Request ANY.RUN access for your company
Frequently Asked Questions (FAQ)
What is enterprise phishing?
Enterprise phishing refers to targeted phishing attacks aimed at corporate users, often designed to steal credentials, session cookies, or gain access to business systems rather than personal accounts.
How do attackers abuse Microsoft and Google platforms for phishing?
Attackers host phishing pages on legitimate services like Microsoft Azure Blob Storage, Google Firebase, and Cloudflare, allowing malicious activity to blend in with trusted cloud traffic and evade traditional detection.
Why is cloud-hosted phishing harder to detect?
Because these attacks use trusted domains, valid HTTPS, and well-known cloud infrastructure, common indicators such as IP addresses, TLS fingerprints, and certificates lose effectiveness.
What are AiTM phishing kits?
AiTM (Adversary-in-the-Middle) phishing kits act as real-time proxies between victims and legitimate services, enabling attackers to bypass MFA and steal credentials without raising obvious suspicion.
Which phishing kits most commonly target enterprises?
Tycoon2FA, Sneaky2FA, and EvilProxy are among the most active kits, frequently used in enterprise-focused campaigns abusing trusted cloud and CDN platforms
Can traditional email security tools stop modern phishing attacks?
Traditional tools alone are often insufficient, as modern phishing relies on trusted infrastructure and advanced evasion techniques that bypass static rules and reputation-based detection.
How can organizations detect cloud-based phishing attacks early?
Early detection requires continuous monitoring of phishing campaigns, up-to-date threat intelligence, and behavioral analysis using interactive sandboxing and real-time investigation tools like ANY.RUN.
GridGuardGhoul
I am a network security researcher and reverse engineer exploring malware, protocols, and exploits.
I am a network security researcher and reverse engineer exploring malware, protocols, and exploits.