好的,我现在需要帮用户总结一篇文章的内容,控制在100个字以内。用户已经给出了文章的详细内容,包括标题、正文和一些FAQ。首先,我需要快速浏览文章,抓住主要观点。 文章主要讲的是2026年身份威胁检测与响应(ITDR)的重要性。随着企业转向云计算、远程办公和SaaS应用,攻击者不再试图“突破防线”,而是直接利用被入侵的身份登录。传统安全措施无法检测到合法凭证下的恶意行为,因此ITDR变得至关重要。 接下来,我需要提取关键点:身份成为新的安全边界、ITDR的作用、其四个核心组件(持续监控、身份治理、威胁情报、事件响应)以及如何通过这些组件减少攻击影响。 然后,我要把这些信息浓缩成100字以内的中文总结。需要注意用词简洁明了,避免使用复杂的术语,同时确保涵盖所有关键点。 最后,检查字数是否符合要求,并确保总结流畅自然。 </think> 2026年,身份已成为新的安全边界。随着企业加速云化和远程办公,攻击者利用入侵身份而非突破防线。传统安全措施无法检测合法凭证下的恶意行为,因此身份威胁检测与响应(ITDR)成为关键。ITDR通过持续监控、异常行为检测、数据关联及自动化响应,帮助企业识别和阻止身份相关攻击,减少潜在损害并提升整体安全性。 2026-2-3 05:43:10 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
In 2026, identity has firmly established itself as the new security perimeter. As enterprises accelerate cloud adoption, enable remote workforces, and integrate SaaS and third-party ecosystems, attackers are no longer trying to “break in”; they are simply logging in. Compromised identities now sit at the center of most advanced breaches, making Identity Threat Detection & Response a critical pillar of modern cybersecurity strategies.
Traditional security controls were never designed to detect malicious behavior occurring under valid credentials. As a result, organizations are increasingly blind to identity-centric attacks that bypass perimeter defenses, evade endpoint tools, and blend seamlessly into legitimate user activity. This is precisely why Identity Threat Detection & Response (ITDR) has moved from a niche capability to a board-level security priority in 2026.
Why ITDR Matters in 2026?
Identity Threat Detection & Response matters in 2026 because identity has become the primary attack surface for cyber threats. Here is why ITDR is crucial:
Continuous Identity Visibility:
ITDR continuously monitors all identity activity across users, applications, and devices. Maintaining a real-time inventory of access rights and account behaviors ensures organizations know who is accessing what, when, and from where.
Impact:
- Reduces blind spots in identity management
- Prevents misuse of dormant or privileged accounts
Detection of Abnormal Behavior Post-Authentication:
Traditional security tools often stop at authentication. ITDR, however, detects suspicious activities even after successful login, such as unusual access patterns, multiple failed attempts, or anomalous privilege escalations.
Impact:
- Identifies compromised accounts faster
- Minimizes potential damage from insider threats or external attackers
- Enhances early warning capabilities for cyber incidents
Correlation with Infrastructure Security Data:
Identity threat detection & response doesn’t operate in isolation; it correlates identity signals with network, endpoint, and cloud security data. This contextual insight helps security teams distinguish between legitimate and malicious behavior.
Impact:
- Provides a holistic view of security posture
- Reduces false positives and alert fatigue
- Supports informed, data-driven incident response
Prevention of Lateral Movement & Privilege Escalation
Attackers often use a single compromised identity to access multiple systems. ITDR enforces controls and flags suspicious privilege escalations to stop lateral movement in real-time.
Impact:
- Prevents large-scale breaches
- Protects sensitive data and critical applications
- Strengthens zero-trust security frameworks
How Threat Detection and Response Works?
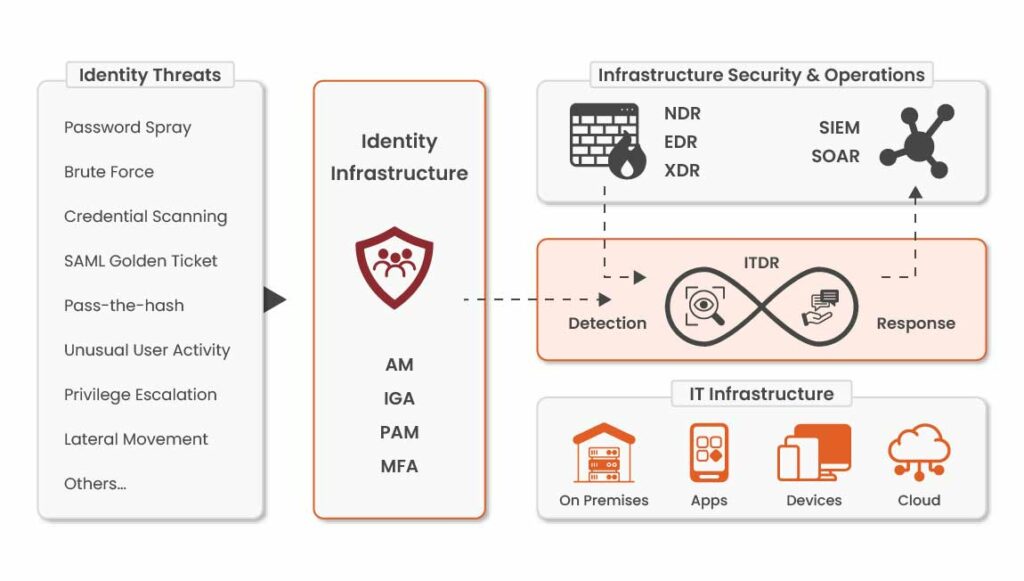
Attackers target identities using techniques like password spraying, credential abuse, and privilege escalation. ITDR monitors identity systems such as IAM, PAM, MFA, and IGA. It correlates this data with signals from EDR, NDR, SIEM, and SOAR. ITDR detects abnormal identity behavior and triggers response actions. This helps protect on-premises systems, cloud environments, applications, and devices.
Use Cases of Identity Threat Detection & Response
Below are the use cases of Identity Threat Detection and Response:
Identity Security Posture Management
Continuously monitors and evaluates identities, access privileges, and authentication mechanisms across the organization’s entire environment.
Identity Incident Investigation & Response
Detects, contains, and eliminates identity-related threats, followed by structured recovery actions and risk mitigation measures.
Identity-Based Zero Trust
Enforces strong identity controls through continuous verification of users and access privileges within a Zero Trust security model.
Secure Privileged Access
Leverages Privileged Access Management (PAM) solutions to reduce risks associated with elevated accounts while ensuring regulatory compliance.
Identity Governance Controls
Implements robust governance frameworks to prevent unauthorized access, reduce data breach risks, and address compliance gaps.
Components Identity Threat Detection & Response
An effective ITDR solution is built on four essential components that operate together seamlessly:
Continuous Monitoring
This keeps a constant watch over networks, systems, and user identities to identify anomalies that may signal identity-based threats. By continuously analyzing logs, events, and activity data, it enables early detection of suspicious behavior. Using machine learning and behavioral analytics, these solutions establish a baseline of normal activity and quickly flag deviations that could indicate an attack on identity systems.
Identity Governance
Identity governance focuses on controlling digital identities and access rights across the organization. It ensures users have the right level of access in line with defined security policies and compliance requirements. These solutions automate user onboarding and offboarding, enforce access controls, and continuously monitor for policy violations, offering centralized visibility and control over access to systems and applications.
Threat Intelligence
Threat intelligence provides insight into the motives, tactics, and tools used by attackers targeting identities and accounts. ITDR solutions leverage this intelligence to help security teams anticipate emerging identity-based threats. With visibility into evolving attack techniques, organizations can more effectively detect, analyze, and respond to sophisticated identity compromises.
Incident Response
Once an identity threat is identified, automated incident response capabilities help contain the impact quickly. Identity threat detection & response solutions can initiate predefined actions such as disabling compromised accounts, isolating affected systems, or enforcing password resets. They also notify security teams in real time and provide contextual details to support investigation and remediation efforts.
An ITDR solution that brings together all four core components enables organizations to take a proactive approach to identity security. Through continuous monitoring and governance, insights from threat intelligence, and rapid automated response, organizations gain end-to-end visibility and control over digital identities and access. This significantly reduces risk across user accounts, networks, systems, applications, and sensitive data.
Join our weekly newsletter and stay updated
Conclusion
In 2026, identity is no longer just a part of the security stack; it is the security perimeter. As attackers increasingly exploit valid credentials, tokens, and privileged accounts to bypass traditional defenses, organizations must shift their focus from simply protecting infrastructure to actively defending identities. Identity Threat Detection & Response provides the visibility, intelligence, and automation needed to detect identity-based attacks that would otherwise remain hidden.
An integrated identity threat detection & response approach that brings together continuous monitoring, identity governance, threat intelligence, and automated incident response enables organizations to detect compromised accounts early, stop lateral movement, and contain threats before they escalate into full-scale breaches. In an era of cloud-first, remote, and hybrid environments, adopting ITDR is not just a best practice; it is a critical requirement for protecting data, maintaining trust, and ensuring long-term cyber resilience.
FAQs
- Why are identity-based attacks increasing in 2026?
As organizations move to cloud, SaaS, and remote work, identities have become the primary gateway to systems and data. Attackers now prefer stealing credentials or abusing privileges because it allows them to operate inside environments without triggering traditional security defenses.
- How does ITDR reduce breach impact?
By detecting compromised accounts early and triggering automated responses such as disabling access, isolating systems, or forcing password resets, ITDR stops attackers before they can move laterally, steal data, or cause widespread damage.
The post Why Identity Threat Detection & Response Matters in 2026? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/why-identity-threat-detection-response-matters-in-2026/
如有侵权请联系:admin#unsafe.sh