嗯,用户让我帮忙总结一篇文章,控制在100字以内,而且不需要特定的开头。首先,我需要仔细阅读这篇文章,理解其主要内容。 文章主要讲的是Tenable Cloud Security在他们的Tenable One平台上的最新增强功能。这些功能包括统一多云探索、高保真网络验证和扩展的身份权限可见性。还有Explorer功能,用于统一查询和关系映射,网络安全性方面的改进,IAM安全性的扩展,以及公共AMI扫描的支持。 接下来,我需要把这些要点浓缩到100字以内。要注意用词简洁,涵盖主要功能和技术提升。同时,避免使用像“文章内容总结”这样的开头。 可能的结构是先点出平台名称和主要更新,然后列举关键功能。例如:“Tenable Cloud Security平台新增统一多云探索、高保真网络验证及扩展身份权限管理功能。Explorer界面支持跨云资源查询与可视化分析,助力企业精准识别风险并优化安全治理。” 这样既涵盖了主要更新,又保持了简洁明了。 </think> Tenable Cloud Security平台新增统一多云探索、高保真网络验证及扩展身份权限管理功能。Explorer界面支持跨云资源查询与可视化分析,助力企业精准识别风险并优化安全治理。 2026-2-2 14:0:0 Author: www.tenable.com(查看原文) 阅读量:2 收藏
February 2, 2026
6 Min Read

Tenable Cloud Security continues to expand the technical depth of our Tenable One exposure management platform. Our latest enhancements include unified multi-cloud exploration, high-fidelity network validation, and expanded entitlement visibility across infrastructure and identity providers.
Key takeaways
- Graph-based multi-cloud exploration: We’ve leveraged our unified data model to provide deep visibility across all cloud environments. You can now easily explore cloud risks and resources using an advanced query builder to build and save queries, and switch to Graph view to instantly visualize complex asset relationships and blast radius.
- Outside-In network attack surface validation: A new external network scanner probes environments to confirm reachability, allowing teams to prioritize vulnerability mitigation based on verifiable external exposure
- Comprehensive identity inventory: We’ve expanded our identity inventory to unify entitlement tracking across cloud platforms, including Microsoft Entra ID and Google Workspace. This allows teams to instantly pinpoint overprivileged roles and unused policies to enforce least privilege at scale.
Explorer: Unified query and relationship mapping
Fragmentation of data across disconnected tools is a primary hurdle in multi-cloud security, often forcing teams to pivot between siloed views to find context. To address this, we have introduced Explorer, a unified interface for deep-dive analysis into resources and findings across your cloud estate. This capability moves beyond static views, allowing security teams to precisely identify risk by querying across objects using granular filters, logical operators, and relationship-based joins.
With the Explorer, you can:
- Perform complex correlations: Use advanced query logic and joins to connect disparate data points, such as linking specific vulnerabilities to their underlying cloud identities or identifying storage buckets that contain sensitive data and are being used for training by AI models.
- Streamline operations: Leverage saved query configurations to standardize repetitive auditing tasks and ensure consistency across compliance reviews.
- Visualize the blast radius: Utilize the Graph view to map asset dependencies, providing a clear visual understanding of how vulnerabilities can propagate through your environment.

The Explorer unifies multi-cloud resources into a single interface, allowing teams to query complex asset relationships and instantly visualize the potential blast radius via Graph view.
Network security: High-fidelity exposure validation
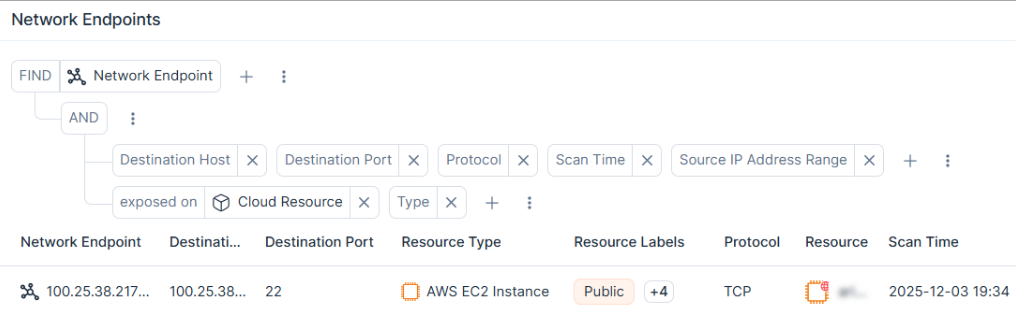
To improve prioritization accuracy, we have enhanced Tenable’s network scanner to perform outside-in probing of your cloud environments' attack surface. Rather than relying solely on static cloud configuration analysis of publicly exposed cloud resources – which can often lead to false positives — this tool conducts an external reachability analysis to confirm whether an endpoint is actually accessible from the internet. By validating real-world exposure, security teams can filter out noise and surface the small percentage of vulnerabilities that pose a genuine external threat.
To translate this validation into action, you can now filter exposed network endpoints by resource type (such as EC2 instances, S3 buckets, and databases), specific ports, host IPs, and other properties. This granularity makes it easier to isolate specific segments of your infrastructure and accelerate targeted remediation of your most critical external exposures.

The Tenable network scanner actively verifies external reachability to confirm internet-exposed workloads
IAM security: Expanded entitlement visibility and insight
Managing identity risk requires deep visibility into both cloud infrastructure and identity providers (IdPs). We have expanded our cloud infrastructure entitlement management (CIEM) capabilities to provide a comprehensive inventory of entitlements across AWS, Azure, GCP, Microsoft Entra ID, and Google Workspace. The Inventory view now displays all roles and identity-based policies—regardless of whether they are currently active. This technical baseline is essential for identifying "ghost" identities and stale permissions that increase the attack surface. Furthermore, administrators can now define custom security policies for any role category, including those not yet deployed in the environment. This enables the establishment of proactive governance and least-privilege guardrails that scale automatically as new resources are provisioned.
Comprehensive posture: Public AMI scanning
Our AWS coverage now includes support for public Amazon Machine Image (AMI) scanning. This allows organizations to assess the security posture of vendor-provided and AWS-published images within their own environment. By analyzing these images for vulnerabilities and misconfigurations, teams can mitigate supply chain risks before they are integrated into production workloads.

Audit-vendor and AWS-published images in your posture assessments to mitigate supply chain risk
Guided use cases: Solve real problems, fast
This month, we’ve added two high-impact use-case packages to help you build an exposure management foundation:
- Prioritize cloud risk that matters most. Use AI-Powered VPR and toxic combination analysis to cut through the noise, reducing remediation time by 80%. See a demo.
- Secure AI workloads. Discover and protect sensitive data powering AI workloads while continuously assessing the underlying AI infrastructure and configurations. Learn more by reading a solution overview.

Advance your security maturity
Maturing a cloud security program requires a shift from managing individual findings to understanding functional resilience. By unifying visibility, validating network reachability, and auditing identity, organizations build the foundation to manage exposure at scale. Tenable Cloud Security is the critical pillar of the Tenable One exposure management platform that provides these comprehensive CNAPP capabilities. Reflecting the real-world value delivered to users, Tenable was recently recognized as a 2025 Customers’ Choice in the Gartner® Peer Insights™ 'Voice of the Customer': Cloud-Native Application Protection Platforms (CNAPPs).
Frequently Asked Questions
- Which identity platforms are now included in the expanded inventory? Coverage has expanded beyond standard cloud providers to include Microsoft Entra ID and Google Workspace, providing visibility into the full "identity-to-data" path.
- What is the primary technical advantage of the Explorer Graph view? It replaces isolated alerts with a visual map of asset relationships, helping teams visualize how a single vulnerability could impact adjacent resources.
- How does the network scanner differ from standard configuration checks? It actively probes the environment from an external perspective to confirm service reachability – assessing exposure more accurately than static code analysis alone.
- Why scan public AMIs? This ensures that third-party images, often used as base layers for workloads, are audited for vulnerabilities within the context of your specific security requirements.
Learn more:
Gartner, Voice of the Customer for Cloud-Native Application Protection Platforms, 24 December 2025, By Peer Community Contributor
Gartner and Peer Insights are trademarks of Gartner, Inc. and/or its affiliates. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences with the vendors listed on the platform, should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.

Yoel Calderon
Senior Director, Product Management
Yoel Calderon, Senior Director of Product Management at Tenable, leads the Tenable Cloud Security Product Management group. He is a cybersecurity product veteran with 18+ years of experience in designing and delivering enterprise software. Before joining Tenable, Yoel led the Cloud Security product portfolio at Proofpoint and played a key role in building VMware’s cloud services platform and shifting the company toward SaaS products. He holds an MBA (magna cum laude) from Tel Aviv University and is a co-inventor on several patents in cloud storage and data protection.
- Cloud
- Exposure Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh