
好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内,并且不需要特定的开头。首先,我得仔细阅读文章内容,理解主要信息。 文章讲的是一个网络攻击者利用暴露的MongoDB实例进行自动化的数据勒索攻击。攻击者主要针对配置不当、容易入侵的数据库,已经影响了大约1400个服务器,赎金大约500美元。研究人员发现超过20万个暴露的MongoDB服务器,其中很多没有身份验证就可访问。攻击者删除数据库并留下赎金信息,但支付后是否能恢复数据无法保证。此外,攻击者使用了有限的几个钱包地址,显示可能是单一威胁行为者。 接下来,我需要提取关键点:攻击目标、方式、影响、赎金金额、研究人员发现的数据量、安全建议等。然后把这些信息浓缩成一句话,不超过100字。 可能的结构是:描述攻击行为、目标、影响和建议措施。比如,“网络攻击者利用暴露的MongoDB实例进行数据勒索,影响1400个服务器,赎金约500美元。研究人员发现20万暴露实例,建议加强安全措施。” 检查字数是否在限制内,并确保信息准确全面。 </think> 网络攻击者利用暴露的MongoDB实例进行自动化数据勒索攻击,已影响约1400个服务器,并要求支付约500美元赎金以恢复数据。研究人员发现超过20万个暴露实例中存在严重安全漏洞,并建议加强身份验证和安全措施以防止此类攻击。 2026-2-1 16:30:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

A threat actor is targeting exposed MongoDB instances in automated data extortion attacks demanding low ransoms from owners to restore the data.
The attacker focuses on the low-hanging fruit, databases that are insecure due to misconfiguration that permits access without restriction. Around 1,400 exposed servers have been compromised, and the ransom note demanded a ransom of about $500 in Bitcoin.
Until 2021, a flurry of attacks had occurred, deleting thousands of databases and demanding ransom to restore the information [1, 2]. Sometimes, the attacker just deletes the databases without a financial demand.
A pentesting exercise from researchers at cybersecurity company Flare revealed that these attacks continued, only at a smaller scale.
The researchers discovered more than 208,500 publicly exposed MongoDB servers. Of them, 100,000 expose operational information, and 3,100 could be accessed without authentication.
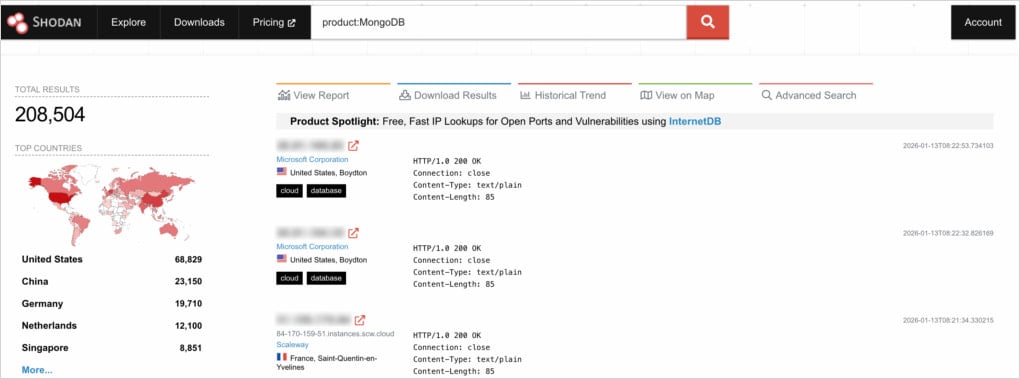
Source: Flare
Almost half (45.6%) of those with unrestricted access had already been compromised when Flare examined them. The database had been wiped, and a ransom note was left.
An analysis of the ransom notes showed that most of them demanded a payment of 0.005 BTC within 48 hours.
“Threat actors demand payment in Bitcoin (often around 0.005 BTC, equivalent today to $500-600 USD) to a specified wallet address, promising to restore the data,” reads the Flare report.
“However, there is no guarantee the attackers have the data, or will provide a working decryption key if paid.”
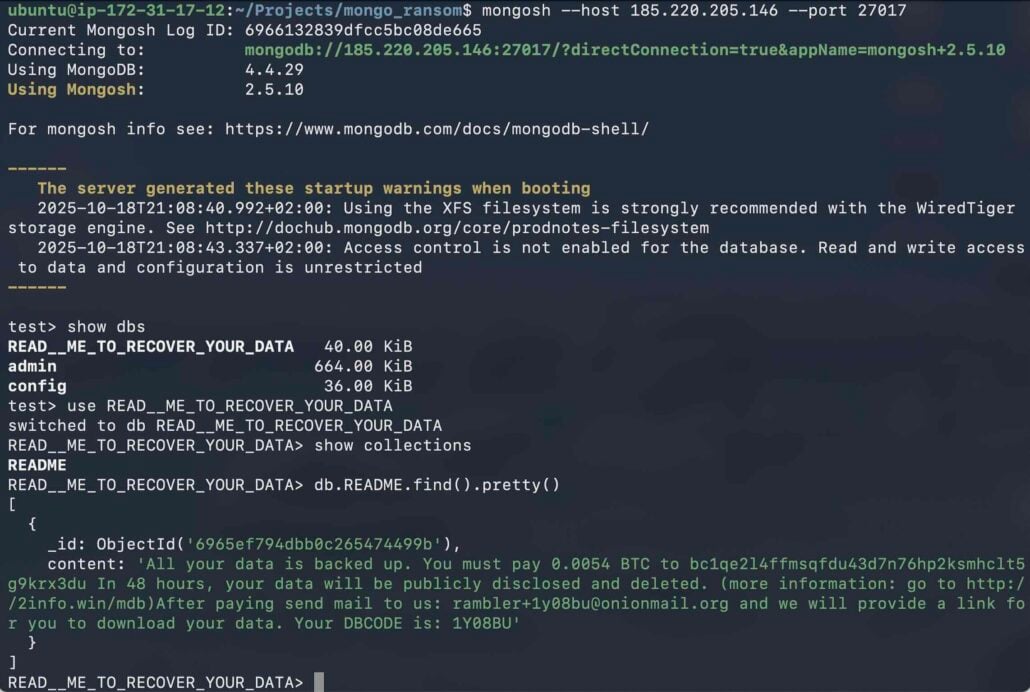
Source: Flare
There were only five distinct wallet addresses across the dropped ransom notes, and one of them was prevalent in about 98% of the cases, indicating a single threat actor focusing on these attacks.
Flare also comments on the remaining exposed instances that didn’t appear to have been hit, even though they were exposed and poorly secured, hypothesizing that those may have already paid a ransom to the attackers.
In addition to poor authentication measures, the researchers also found that nearly half (95,000) of all internet-exposed MongoDB servers run older versions that are vulnerable to n-day flaws. However, the potential of most of those was limited to denial-of-service attacks, not offering remote code execution.
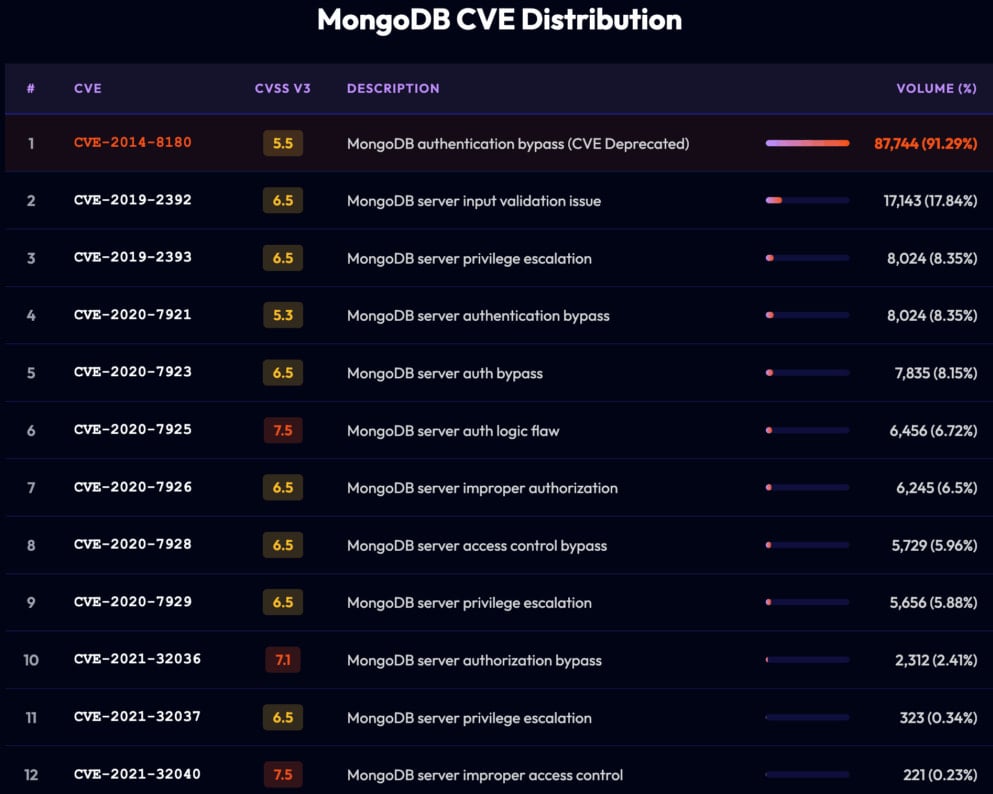
Source: Flare
Flare suggests that MongoDB administrators avoid exposing instances to the public unless it’s absolutely necessary, use strong authentication, enforce firewall rules and Kubernetes network policies that allow only trusted connections, and avoid copying configurations from deployment guides.
MongoDB should be updated to the latest version and continuously monitored for exposure. In the case of exposure, credentials need to be rotated and logs examined for unauthorized activity.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
如有侵权请联系:admin#unsafe.sh

