好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,理解其主要内容。 文章讲的是一个读者Charlie转发的一个钓鱼邮件,这个邮件是发给Vivaldi Webmail用户的。邮件看起来不太可信,但可能还是能骗到一些用户。接着,用户点击链接后会进入Google文档的幻灯片展示。通常情况下,Google Docs会有警告 footer 提示可能的钓鱼网站,并提供举报链接,但在这个案例中没有出现。 作者最初怀疑是HTML、JavaScript或CSS的技巧,但后来发现这是Google Docs的一个功能。通过调整URL中的参数,可以避免显示编辑窗口和footer。特别是当幻灯片被发布时,footer会被移除,而且可以设置自动播放的时间间隔。 钓鱼邮件最终引导到一个经典的登录表单页面,使用Square创建,并且该页面仍然在线。 现在我需要将这些信息浓缩到100字以内。重点包括:钓鱼邮件针对Vivaldi用户、利用Google Docs隐藏警告、链接指向登录表单。确保语言简洁明了。 </think> 一封针对Vivaldi Webmail用户的钓鱼邮件利用Google Docs隐藏警告功能,引导用户点击链接后进入幻灯片展示页面,并最终指向一个登录表单进行诈骗。 2026-1-30 17:56:10 Author: isc.sans.edu(查看原文) 阅读量:0 收藏
Charlie, one of our readers, has forwarded an interesting phishing email. The email was sent to users of the Vivladi Webmail service. While not overly convincing, the email is likely sufficient to trick a non-empty group of users:
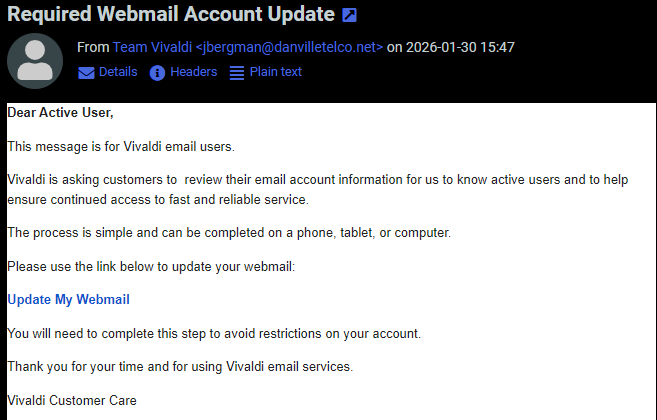
The e-mail gets more interesting as the user clicks on the link. The link points to Google Documents and displays a slide show:
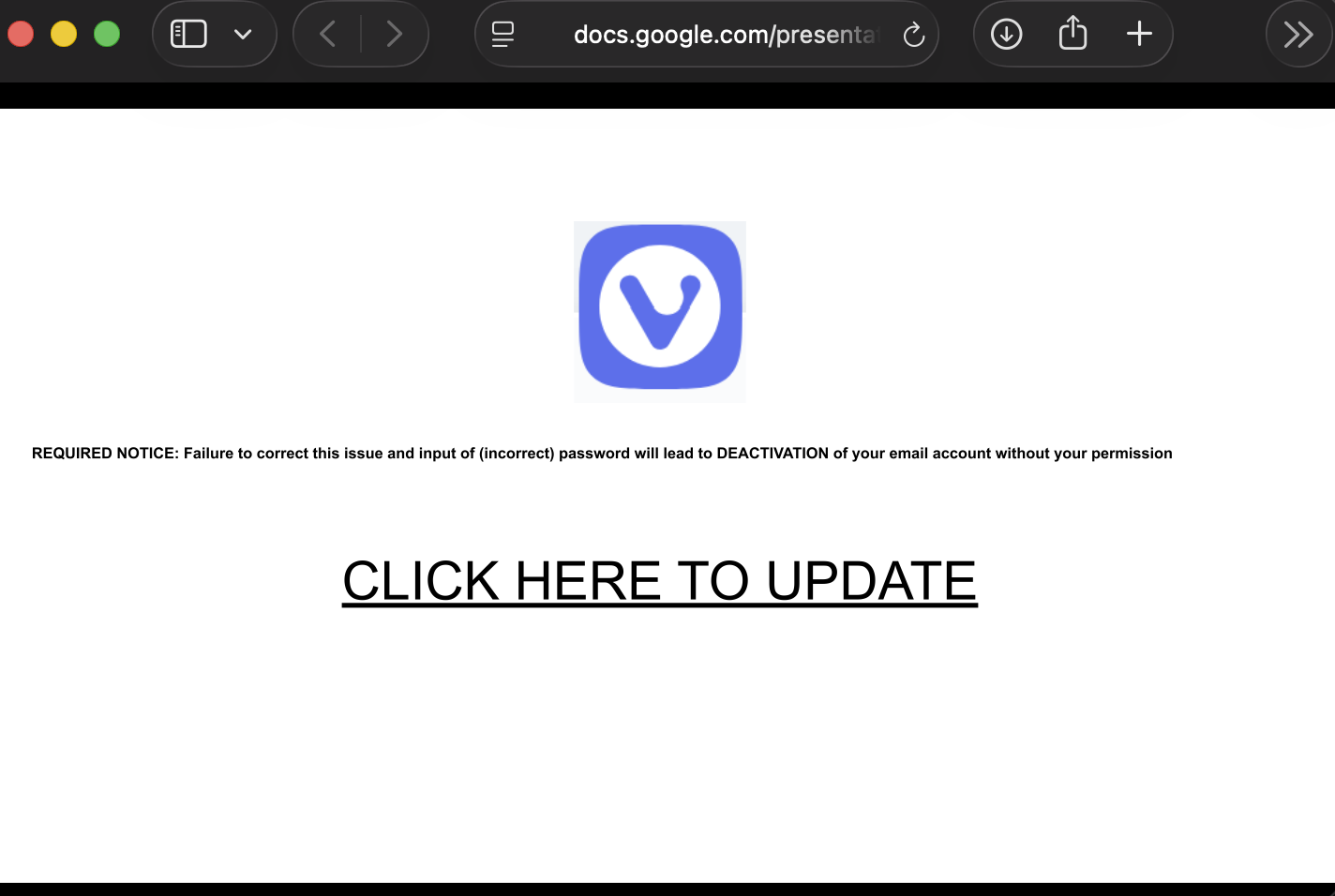
Usually, Google Docs displays a footer notice that warns viewers about phishing sites and offers a "reporting" link if a page is used for phishing. Bots are missing in this case. At first, I suspected some HTML/JavaScript/CSS tricks, but it turns out that this isn't a bug; it is a feature!
Usually, if a user shares slides, the document opens in an "edit" window. This can be avoided by replacing "edit" with "preview" in the URL, but the footer still makes it obvious that this is a set of slides. To remove the footer, the slides have to be "published," and the resulting link must be shared. When publishing, the slides will auto-advance. But for a one-slide slideshow, this isn't an issue. There is also a setting to delay the advance. Here are some sample links:
[These links point to a simple sample presentation I created, not the phishing version.]
Normal Share:
https://docs.google.com/presentation/d/1Quzd6bbuPlIcTOorlUDzSuJCXiOyqBTSHczo6hnXcac/edit?usp=sharing
Preview Share:
https://docs.google.com/presentation/d/1Quzd6bbuPlIcTOorlUDzSuJCXiOyqBTSHczo6hnXcac/preview?usp=sharing
Publish Share:
https://docs.google.com/presentation/d/e/2PACX-1vRaoBusJAaIoVcNbGsfVyE0OuTP1dS-2Po9lpAN9GGy2EkbZG_oR9maZDS7cq2xW_QeiF8he457hq3_/pub?start=false&loop=false&delayms=30000
The URL parameters in the last link do not start the presentations, nor loop them, and delay the next slide by 30 seconds.
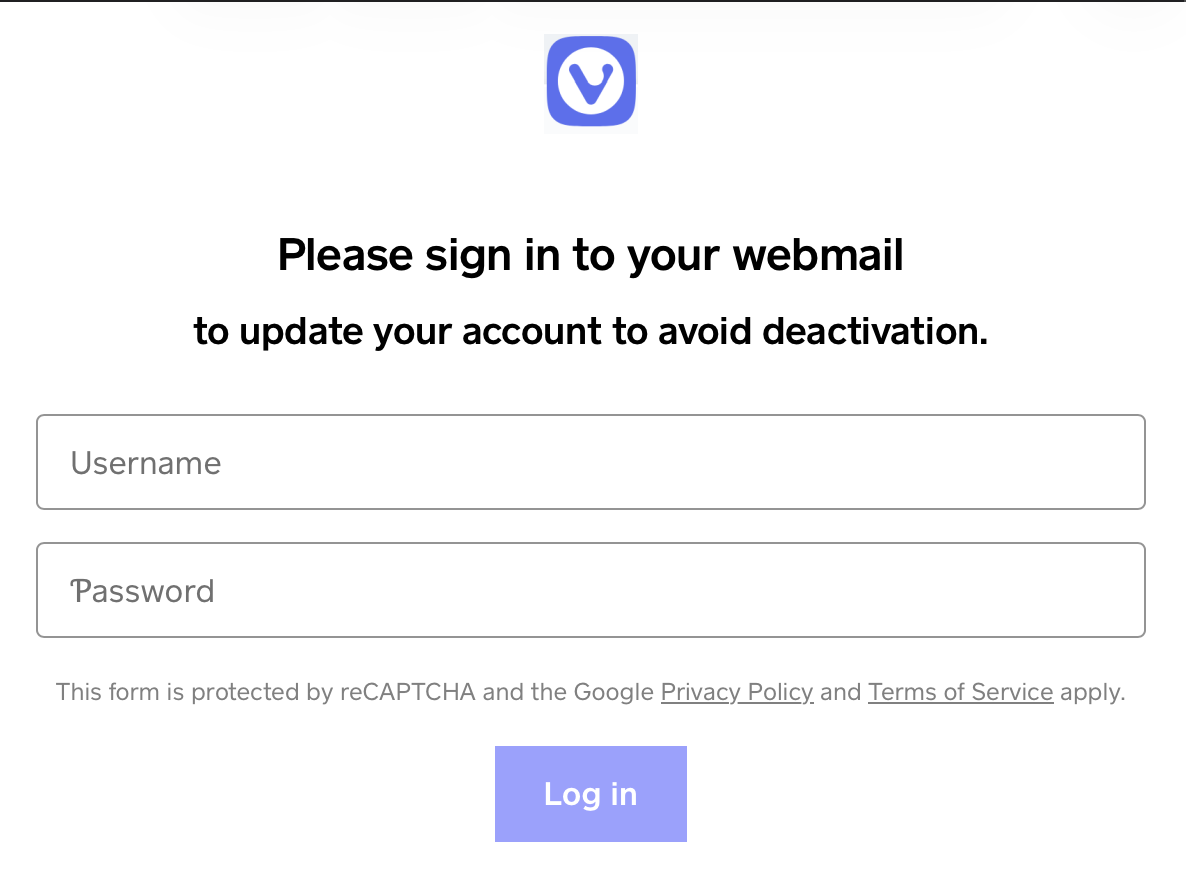
The Vivaldi webmail phishing ended up on a "classic" phishing login form that was created using Square. So far, this form is still visible at
hxxps [:] //vivaldiwebmailaccountsservices[.]weeblysite[.]com
 ???????
???????
--
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
如有侵权请联系:admin#unsafe.sh