好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内,并且不需要特定的开头。首先,我得仔细阅读文章,抓住主要信息。 文章讲的是一个新的Android恶意软件活动,利用Hugging Face平台作为存储库,托管了数千种APK的有效负载变种。这些有效负载收集了流行的金融服务和支付服务的凭证。Hugging Face是一个可信的平台,但被恶意分子滥用。 研究人员来自Bitdefender,他们发现了这个活动。攻击开始于受害者被诱骗安装一个名为TrustBastion的应用程序,伪装成安全工具,使用 scareware 式广告声称设备被感染。安装后,TrustBastion会显示一个强制更新的警告,看起来像Google Play。 这个恶意软件并不直接分发恶意软件,而是联系到一个服务器,然后重定向到Hugging Face的数据集仓库来托管恶意APK。最终的有效负载从Hugging Face的基础设施下载,并通过其内容分发网络交付。 为了逃避检测,威胁参与者使用服务器端多态性,每15分钟生成新的有效负载变种。在调查时,仓库已经存在大约29天,并积累了超过6,000次提交。分析期间,该有效负载分发仓库被关闭,但后来以新名称“Premium Club”重新出现。 主要的有效负载是一个远程访问工具(RAT),利用Android的无障碍服务来监控用户活动、捕获屏幕截图、显示仿冒金融应用的钓鱼覆盖层以窃取凭证,并尝试窃取锁屏密码。它还连接到C2服务器来接收指令和配置更新。 Bitdefender通知了Hugging Face关于威胁行为者的仓库,并移除了包含恶意软件的数据集。研究人员还发布了指示器以识别威胁。 最后建议Android用户避免从第三方应用商店下载应用或手动安装,并审查应用请求的权限。 现在我需要将这些信息浓缩到100字以内。关键点包括:新的Android恶意软件利用Hugging Face托管有效负载变种;伪装成安全工具诱骗用户;通过Hugging Face分发;每15分钟生成新变种;收集金融和支付服务凭证;使用无障碍服务监控和窃取数据;建议用户避免第三方来源并检查权限。 综合以上信息,我可以这样组织语言: “一篇关于新型 Android 恶意软件利用 Hugging Face 平台托管数千个有效负载变种的文章。该恶意软件伪装成安全工具诱骗用户安装,并通过 Hugging Face 分发恶意 APK。每 15 分钟生成新变种以逃避检测,并收集金融和支付服务凭证。” 这样控制在100字以内,并且涵盖了主要的信息点。 </think> 一篇关于新型 Android 恶意软件利用 Hugging Face 平台托管数千个有效负载变种的文章。该恶意软件伪装成安全工具诱骗用户安装,并通过 Hugging Face 分发恶意 APK。每 15 分钟生成新变种以逃避检测,并收集金融和支付服务凭证。 2026-1-29 22:15:16 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

A new Android malware campaign is using the Hugging Face platform as a repository for thousands of variations of an APK payload that collects credentials for popular financial and payment services.
Hugging Face is a popular platform that hosts and distributes artificial intelligence (AI), natural language processing (NLP), and machine learning (ML) models, datasets, and applications.
It is considered a trusted platform unlikely to trigger security warnings, but bad actors have abused it in the past to host malicious AI models.
The recent campaign discovered by researchers at Romanian cybersecurity company Bitdefender leverages the platform to distribute Android malware.
The attack begins with victims being lured to install a dropper app called TrustBastion, which uses scareware-style ads claiming that the target’s device is infected. The malicious app is disguised as a security tool, claiming to detect threats such as scams, fraudulent SMS messages, phishing attempts, and malware.
Immediately after installation, TrustBastion shows a mandatory update alert with visual elements that mimic Google Play.
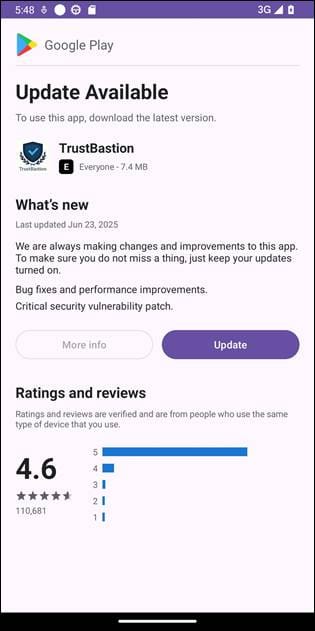
Source: Bitdefender
Instead of directly serving malware, the dropper contacts a server linked to trustbastion[.]com, which returns a redirect to a Hugging Face dataset repository hosting the malicious APK. The final payload is downloaded from Hugging Face infrastructure and delivered via its content distribution network (CDN).
To evade detection, the threat actor uses server-side polymorphism that generates new payload variants every 15 minutes, Bitdefender says.
"At the time of investigation, the repository was approximately 29 days old and had accumulated more than 6,000 commits."
During analysis, the payload-serving repository was taken down, but the operation resurfaced under a new name, ‘Premium Club,’ which used new icons while retaining the same malicious code.
The main payload, which lacks a name, is a remote access tool that aggressively exploits Android’s Accessibility Services, presenting the request as necessary for security reasons.
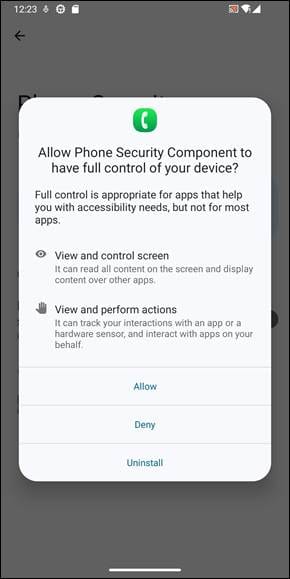
Source: Bitdefender
This gives the malware the ability to serve screen overlays, capture the user’s screen, perform swipes, block uninstallation attempts, and more.
In this case, Bitdefender says the malware monitors user activity and captures screenshots, exfiltrating everything to its operators. The malware also displays fake login interfaces impersonating financial services such as Alipay and WeChat to steal credentials, and also attempts to steal the lock screen code.
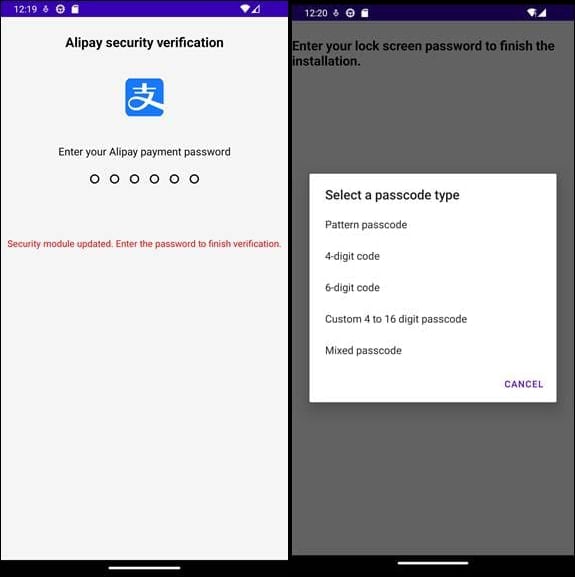
Source: Bitdefender
The malware remains connected at all times to the command-and-control (C2) server, which receives the stolen data, sends command execution instructions, configuration updates, and also pushes fake in-app content to make TrustBastion appear legitimate.
Bitdefender informed Hugging Face about the threat actor's repository, and the service removed the datasets containing the malware. Researchers also published a set of indicators of compromise for the dropper, the network, and malicious packages.
Android users should avoid downloading apps from third-party app stores or installing them manually. They should also review the permissions an app requests and ensure all of them are necessary for the app’s intended functionality.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

