嗯,用户让我总结一篇文章,控制在一百个字以内,而且不需要特定的开头。首先,我需要快速阅读文章,抓住主要内容。 文章讲的是Marquis Software Solutions在2025年8月遭受了勒索软件攻击,影响了几十家美国银行和信用社。他们最初以为是SonicWall防火墙未修补导致的,但后来发现攻击者其实是通过入侵SonicWall的MySonicWall在线客户门户获取了防火墙配置备份文件中的信息。SonicWall在9月报告了这个安全漏洞,并警告客户重置账户凭证。Marquis现在正在评估选项,可能寻求补偿损失。 接下来,我需要把这些要点浓缩成一句话,不超过100字。要确保涵盖事件的时间、涉及的公司、攻击方式以及后续影响。 最后,检查一下是否符合用户的要求:中文、简洁、不使用特定开头。这样应该就能满足用户的需求了。 </think> Marquis Software Solutions遭遇2025年8月的勒索软件攻击,影响多家美国银行和信用社。攻击者利用从SonicWall MySonicWall门户窃取的防火墙配置数据绕过Marquis的防火墙。SonicWall于9月披露其云备份服务受 breach影响,并警告威胁者可能更容易入侵客户防火墙。Marquis正在评估对防火墙提供商的追偿选项。 2026-1-29 18:0:26 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

Marquis Software Solutions, a Texas-based financial services provider, is blaming a ransomware attack that impacted its systems and affected dozens of U.S. banks and credit unions in August 2025 on a security breach reported by SonicWall a month later.
The software company provides data analytics, compliance reporting, CRM tools, and digital marketing services to more than 700 banks, credit unions, and mortgage lenders across the United States.
In statements to customers earlier this week seen by BleepingComputer, Marquis says the ransomware operators didn't breach its systems by exploiting an unpatched SonicWall firewall, as previously believed.
Instead, the attackers used information obtained from firewall configuration backup files stolen after gaining unauthorized access to SonicWall's MySonicWall online customer portal.
"Based on the ongoing third-party investigation, we have determined that the threat actor that attacked Marquis was able to circumvent our firewall by leveraging the configuration data extracted from the service provider's cloud backup breach," Marquis said.
"At this time, Marquis is evaluating its options with respect to the firewall provider, including to seek recoupment of any expenses spent by Marquis and its customers in responding to the data incident."
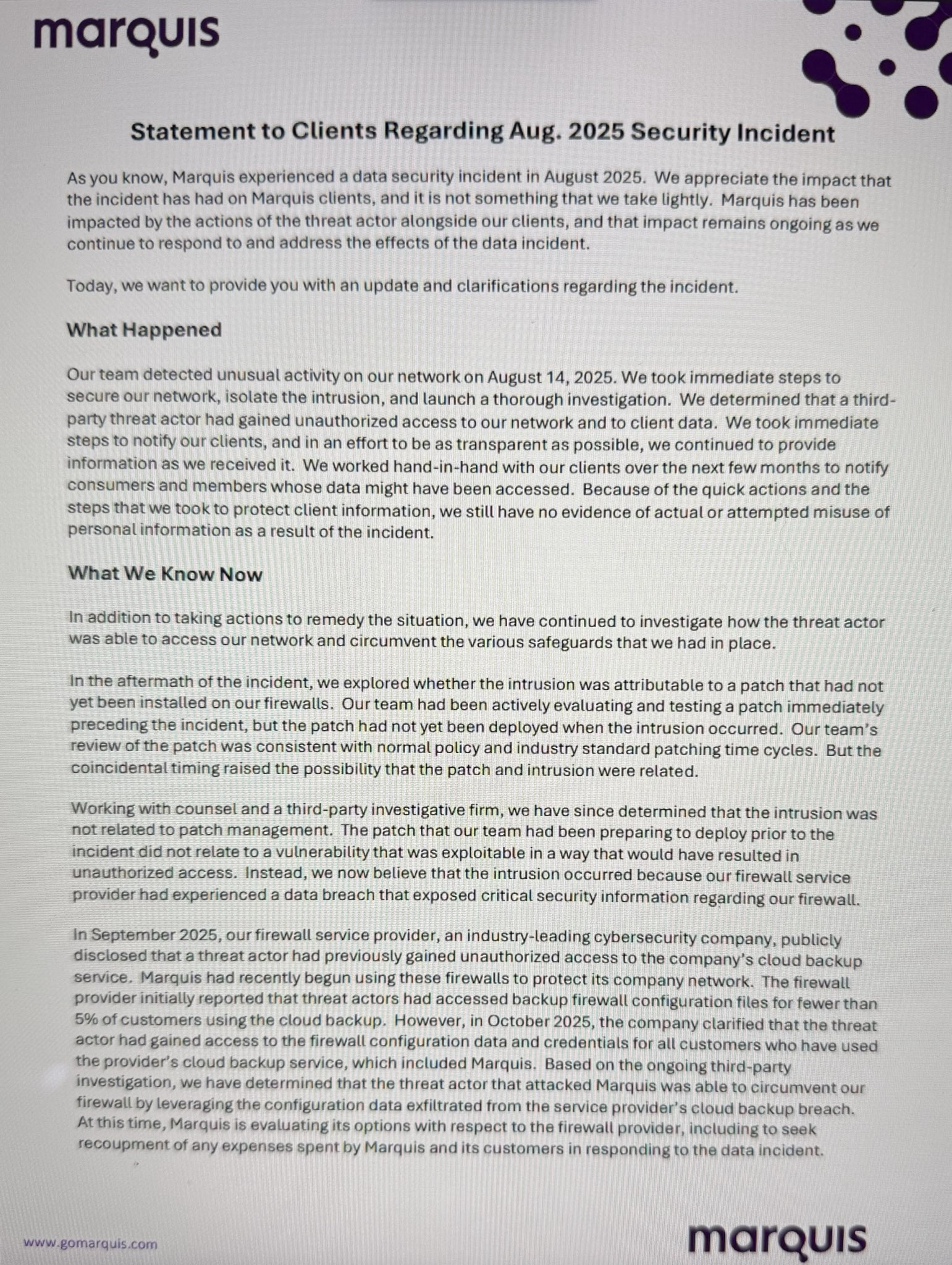
SonicWall disclosed the security breach mentioned by Marquis on September 17, when it warned customers to reset their MySonicWall account credentials and said the incident affected only about 5% of its firewall customers using its cloud backup service.
The company also warned that threat actors could extract access credentials and tokens, making it "significantly easier" to compromise affected customers' firewalls. However, roughly three weeks later, SonicWall issued an update confirming that all customers using its cloud backup service were affected by the September breach.
One month later, it published another update stating that a Mandiant investigation into the September attack found evidence linking the incident to state-sponsored hackers.
SonicWall added that the MySonicWall breach was unrelated to attacks by the Akira ransomware gang that targeted MFA-protected SonicWall VPN accounts in late September.
Cybersecurity company Huntress reported on October 13 that it had observed threat actors compromising over 100 SonicWall SSLVPN accounts in a large-scale campaign using stolen, valid credentials. However, Huntress found no evidence linking these attacks to the SonicWall cloud backup hack, and SonicWall did not respond to BleepingComputer's requests for comment at the time.
BleepingComputer reached out again earlier this week, but a SonicWall spokesperson has yet to reply.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

