好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,理解主要信息。 文章讲的是Match Group,他们拥有Tinder、Match.com等多个在线约会服务。最近发生了网络安全事件,黑客入侵了他们的系统,泄露了用户数据。具体来说,ShinyHunters威胁集团泄露了1.7GB的压缩文件,包含1000万条用户记录和内部文档。Match Group确认了这一事件,并表示他们已经采取措施终止未经授权的访问。 文章还提到,调查正在进行中,没有迹象显示黑客获取了用户的登录凭证、财务信息或私人通信。公司正在通知受影响的用户。此外,这次攻击是通过钓鱼网站和社会工程学手段进行的,利用Okta的SSO账户进入公司系统。 总结的时候要抓住关键点:Match Group的数据泄露事件、涉及的服务、泄露的数据量、黑客手段以及公司的应对措施。同时要控制在100字以内,避免使用“这篇文章”这样的开头。 现在组织语言:Match Group遭遇网络攻击,涉及Tinder等平台。黑客窃取了1000万用户的部分数据,并未获取敏感信息。公司已采取行动,并与外部专家合作调查。强调数据泄露的影响范围和公司的应对措施。 最后检查字数是否符合要求,并确保内容准确简洁。 </think> Match Group, owner of dating apps like Tinder and Match.com, confirmed a cyberattack where hackers stole limited user data, including 10 million records from Hinge, Match, and OkCupid. The breach involved social engineering and phishing attacks targeting Okta SSO accounts. Match Group is investigating and notifying affected users, with no access to sensitive login or financial data. 2026-1-29 18:15:30 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

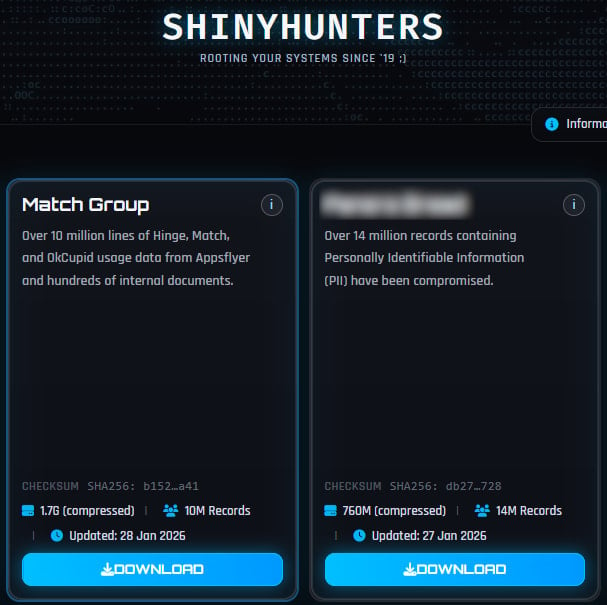
Match Group, the owner of multiple popular online dating services, Tinder, Match.com, Meetic, OkCupid, and Hinge, confirmed a cybersecurity incident that compromised user data.
The company stated that hackers stole a "limited amount of user data" after the ShinyHunters threat group leaked 1.7 GB of compressed files allegedly containing 10 million records of Hinge, Match, and OkCupid user information, as well as internal documents.
In a statement to BleepingComputer, a spokesperson for Match Group confirmed the incident.
"We are aware of claims being made online related to a recently identified security incident," the company spokesperson said.
"Match Group takes the safety and security of our users seriously and acted quickly to terminate the unauthorized access."
Source: BleepingComputer
The company said the investigation into the incident is in progress with the help of external experts, and that there is no indication that the hackers accessed user log-in credentials, financial information, or private communications.
"We believe the incident affects a limited amount of user data, and we are already in the process of notifying individuals, as appropriate," Match Group says.
Match Group is a giant in online dating, generating annual revenue of $3.5 billion, and the active user base across all its apps is estimated to be more than 80 million.
This latest incident is part of a new ShinyHunters voice phishing (vishing) campaign targeting single sign-on (SSO) accounts at Okta, Microsoft, and Google across over a hundred high-value organizations, using links to supposedly internal login portals.
In the case of Match Group, BleepingComputer was told that the attacker stole data after compromising an Okta SSO account that gave them access to the company's AppsFlyer marketing analytics instance and Google Drive and Dropbox cloud storage accounts.
BleepingComputer has learned that the social engineering attack used the phishing domain at ‘matchinternal.com.’
The hackers said that the data contains personally identifiable information (PII), but not a lot of it. and that most of it consists of tracking information.
Companies can add defenses against attacks based on social-engineering by implementing solutions that are resistant to phishing attempts.
"While this is not the result of a security vulnerability in vendors’ products or infrastructure, we strongly recommend moving toward phishing-resistant MFA, such as FIDO2 security keys or passkeys where possible, as these protections are resistant to social engineering attacks in ways that push-based or SMS authentication are not," Charles Carmakal, Mandiant's Chief Technology Officer, says.
Furthermore, "administrators should also implement strict app authorization policies and monitor logs for anomalous API activity or unauthorized device enrollments."
In a post last week, Okta also recommends phishing resistance to prevent access to resources."When using Okta for workforce authentication, that would equate to enrolling users in Okta FastPass, passkeys or both for the sake of redundancy," says Moussa Diallo, threat researcher at Okta Threat Intelligence.
"Social engineering actors can also be frustrated by setting network zones or tenant access control lists that deny access via the anonymizing services favoured by threat actors. The key is to know where your legitimate requests come from, and allowlist those networks,” Diallo said.
The researcher notes that there are some financial institutions, like Monzo Bank and the Crypto exchange, currently testing live caller checks, where users can verify in the official mobile app from the company if an authorized representative is on the phone with them.
The 2026 CISO Budget Benchmark
It's budget season! Over 300 CISOs and security leaders have shared how they're planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
如有侵权请联系:admin#unsafe.sh

