好的,我现在需要帮用户总结一篇文章,控制在100字以内。用户的要求是直接写描述,不需要开头。首先,我得仔细阅读文章内容,抓住关键点。 文章讲的是Google Threat Intelligence Group(GTIG)联手行业伙伴破坏了IPIDEA,这是一个大型的住宅代理网络,被威胁者滥用。他们采取了关闭相关域名、共享SDK情报等措施。IPIDEA伪装成VPN服务,用户量很大,但实际上是通过感染设备进行恶意活动。 接下来,我需要提炼这些信息。GTIG的行动、IPIDEA的伪装、用户数量、恶意用途以及影响。还要注意字数限制,所以要简洁明了。 可能会提到GTIG联合行动、破坏IPIDEA、伪装VPN、670万用户、恶意活动如接管账户和DDoS攻击等。同时说明虽然打击了IPIDEA,但威胁可能卷土重来。 最后检查一下是否符合要求:100字以内,直接描述内容,没有开头用语。 </think> Google Threat Intelligence Group联合行业伙伴破坏了大型住宅代理网络IPIDEA,该网络被伪装成VPN服务用于恶意活动。行动包括关闭相关域名和共享SDK情报。IPIDEA曾拥有670万用户,并被用于账户接管、敏感信息窃取及大规模DDoS攻击等。尽管此次行动重创IPIDEA运营,但其可能重建基础设施继续威胁网络安全。 2026-1-29 19:30:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

IPIDEA, one of the largest residential proxy networks used by threat actors, was disrupted earlier this week by Google Threat Intelligence Group (GTIG) in collaboration with industry partners.
The action included taking down domains associated with IPIDEA services, infected device management, proxy traffic routing. Additionally, intelligence has been shared on the IPIDEA software development kits (SDK) that distributed the proxying tool.
The operators of IPIDEA advertised it as a VPN service that "encrypts your online traffic and hides your real IP address," used by 6.7 million users worldwide.
Residential proxy networks use home user or small business IP addresses to route traffic after compromising devices on the network. Typically, the infection occurs through trojanized apps and software posing as useful utilities.
In a court letter, Google explains that threat actors use residential proxies in various malicious activities, such as account takeovers, fake account creation, credential theft, and sensitive information exfiltration.
"By routing traffic through an array of consumer devices all over the world, attackers can mask their malicious activity by hijacking these IP addresses. This generates significant challenges for network defenders to detect and block malicious activities," Google says in a report today.
In the case of IPIDEA, GTIG observed a range of malicious activity, with more than 550 distinct threat groups using its exit nodes in a single week, including actors from China, Iran, Russia, and North Korea.
The observed activities included access to victim SaaS platforms, password spraying, botnet control, and infrastructure obfuscation. Previously, Cisco Talos linked IPIDEA to large-scale brute-forcing attacks targeting VPN and SSH services.
IPIDEA infrastructure also supported record-breaking DDoS botnets such as Aisuru and Kimwolf.
Google says IPIDEA enrolled devices using at least 600 trojanized Android apps that embedded proxying SDKs (Packet SDK, Castar SDK, Hex SDK, Earn SDK), and over 3,000 trojanized Windows binaries posing as OneDriveSync or Windows Update.
Source: Google
IPIDEA promoted several VPN and proxying apps to Android users that secretly turned their devices into proxy exit nodes without their knowledge or consent.
According to Google, IPIDEA operators ran at least 19 residential proxy businesses that pretended to be legitimate services and sold access to devices compromised with the BadBox 2.0 malware. Some of the associate brands are listed below:
-
360 Proxy (360proxy\.com)
-
922 Proxy (922proxy\.com)
-
ABC Proxy (abcproxy\.com)
-
Cherry Proxy (cherryproxy\.com)
-
Door VPN (doorvpn\.com)
-
Galleon VPN (galleonvpn\.com)
-
IP 2 World (ip2world\.com)
-
Ipidea (ipidea\.io)
-
Luna Proxy (lunaproxy\.com)
-
PIA S5 Proxy (piaproxy\.com)
-
PY Proxy (pyproxy\.com)
-
Radish VPN (radishvpn\.com)
-
Tab Proxy (tabproxy\.com)
- Aman VPN (defunct)
Despite the multiple brands, all services are connected to a centralized infrastructure under the single control of IPIDEA operators, who remain unidentified.
Google Play Protect now automatically detects and blocks on up-to-date, certified Android devices the applications that include IPIDEA-related SDKs.
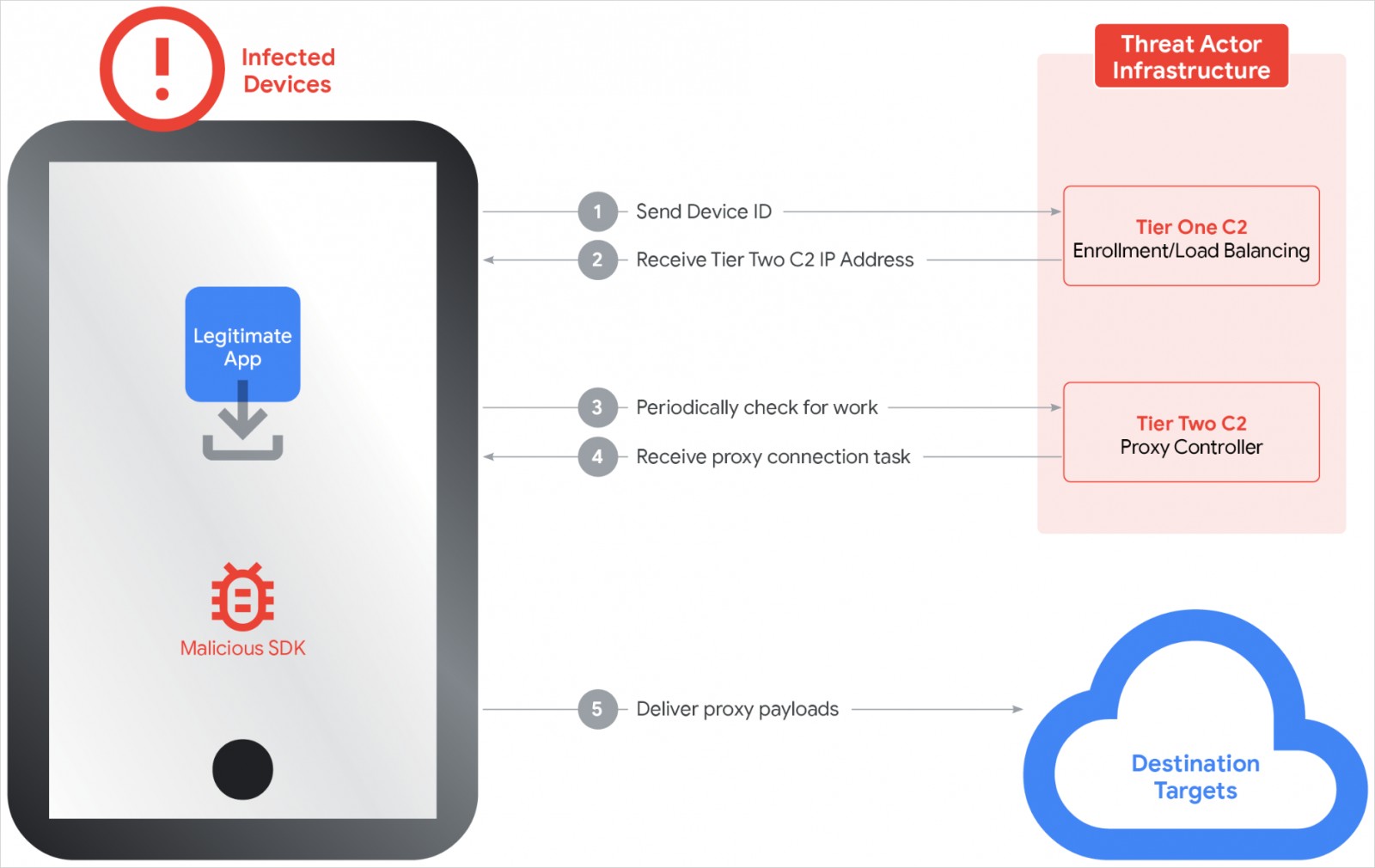
Regarding its structure, Google explains that IPIDEA operated on a two-tier command-and-control (C2) system. The first tier provides configuration and timing, and the node lists for the second tier.
According to the researchers, the second tier comprised roughly 7,400 servers that assigned proxying tasks and relayed traffic.
Source: Google
Google researchers note that the operators of the networks also offered free VPN services through apps that provided the advertised fucntionality. However, the devices were added to the IPIDEA network, acting as an exit node.
Although GTIG and partners' action likely had a significant impact on IPIDEA's operations, the threat actor may try to rebuild its infrastructure. Currently, there are no arrests or indictments announced.
Users should remain cautious about apps that offer payment in exchange for bandwidth, as well as free VPN and proxy apps from non-reputable publishers.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

