嗯,用户让我总结一下这篇文章的内容,控制在100字以内,而且不需要特定的开头。首先,我需要快速浏览文章,抓住主要信息。 文章主要讲的是Moltbot,一个开源的AI助手,可以集成到各种消息平台,执行各种任务。然后提到它在GitHub上的流行情况,用户增长很快。接着讨论了安全问题,很多用户不小心泄露了敏感信息,比如API密钥和令牌。最后介绍了GitGuardian开发的一个插件来帮助检测这些秘密。 现在我需要把这些要点浓缩到100字以内。要确保涵盖Moltbot的功能、流行度、安全问题以及解决方案。可能的结构是先介绍Moltbot,然后提到它的流行和安全漏洞,最后解决方案。 检查一下是否遗漏了关键点:开源、本地运行、集成消息平台、自动化任务、快速增长、秘密泄露、解决方案插件。这些都得包含进去。 最后组织语言,确保流畅且符合字数限制。 </think> Moltbot 是一个开源 AI 助手,可集成多种消息平台并执行复杂任务。自 2025 年发布以来迅速走红,在 GitHub 上获得大量关注和叉取。然而,用户因配置不当泄露大量敏感信息(如 API 密钥和令牌),GitGuardian 检测到 181 个独特秘密。为解决此问题,GitGuardian 开发了 ggshield 插件以帮助用户扫描和防止秘密泄露。 2026-1-29 16:56:40 Author: securityboulevard.com(查看原文) 阅读量:0 收藏

Moltbot (formerly known as Clawdbot) is an open-source, self-hosted AI agent that operates directly on your local machine. It acts as your 24/7 personal assistant, and easily integrates with popular messaging platforms like WhatsApp, Telegram, and Slack, enabling it to execute tasks and take actions, going beyond simple conversational interactions.
It is a personal assistant that you can interact with using messages to automate a whole range of tasks. Agent skills are published at https://clawdhub.com/ and allow to easily extend Moltbot. Using dozens of integrations, you can:
- sort emails and reply to them
- review pull requests
- summarize daily meetings
- book sport activities
- plan weekly meals for the family, and order groceries online
- Write code and deploy applications on your behalf
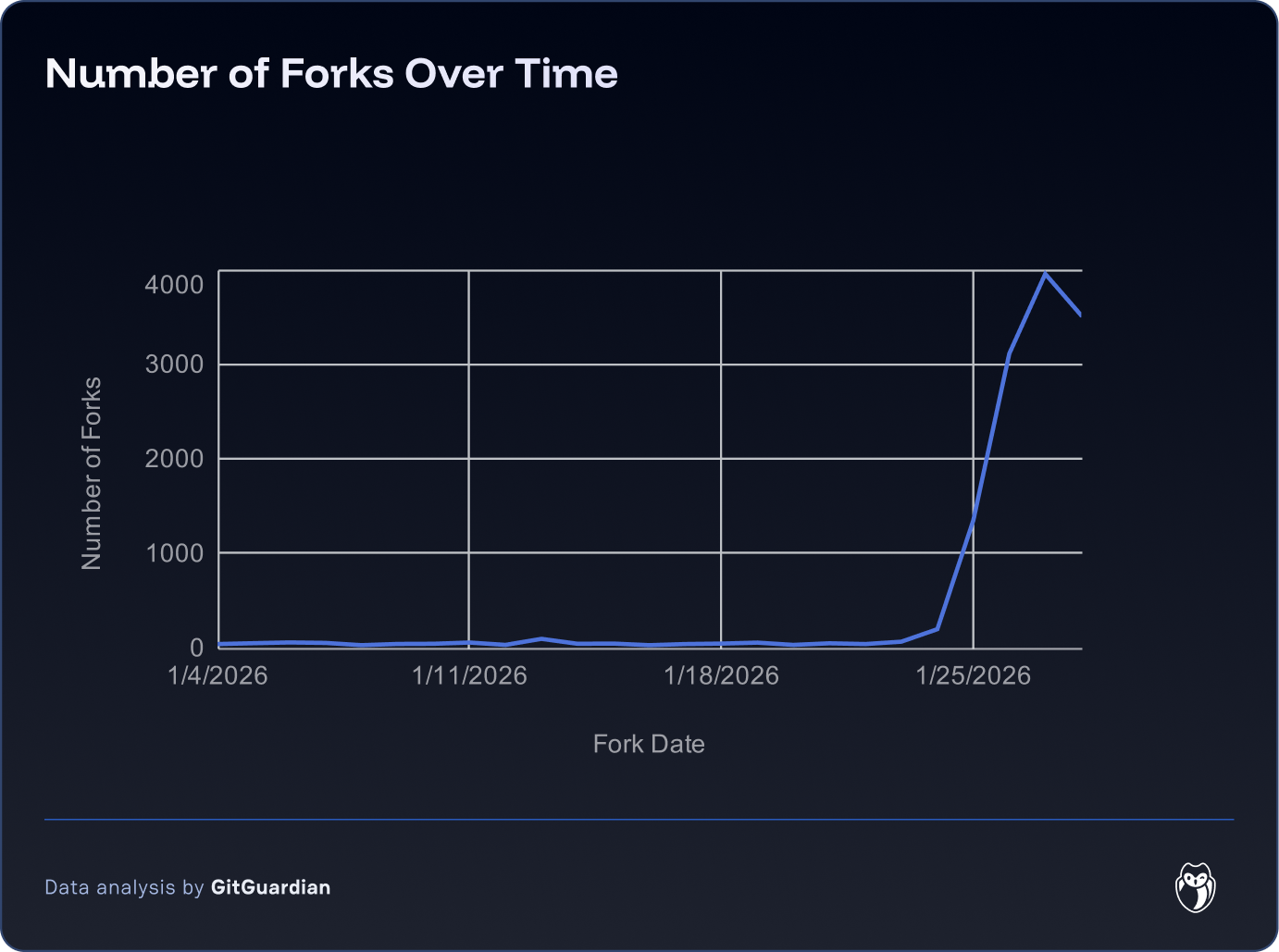
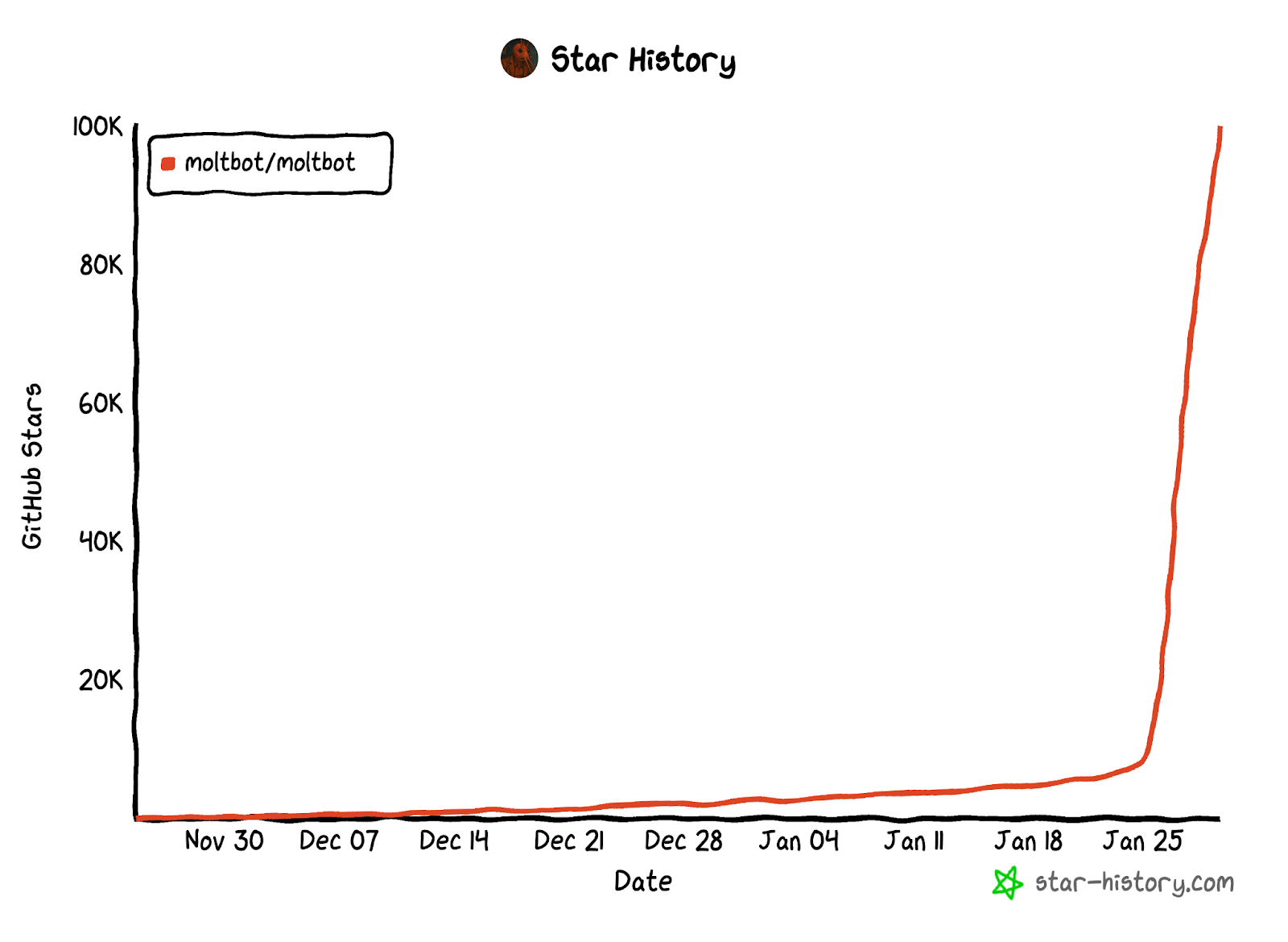
Moltbot versatile and automated actions make it an extremely powerful tool whose adoption has continued to grow since its release in November 2025. Its usage went viral on January 24 2026, when the number of daily forks on GitHub went from 50+ to 3000+. The project's star count mirrored this explosive growth: Moltbot gained a record-breaking 17,830 stars in a single day, ultimately crossing 85,000 stars within weeks—the fastest growth trajectory in GitHub history.
A Moltbot workspace is the agent's home (defaults to ~/clawd) – designed as a git repository for backup and sync. It provides the agent with persistent memory and a dedicated space for executing tools and tasks.
The documentation recommends treating the workspace as private storage and strongly encourages users to save it in private GitHub repositories. One section of the documentation is even dedicated to the risks associated with hardcoded secrets.
However, as might be expected, some people make mistakes and push their workspaces to public repositories – including secrets.
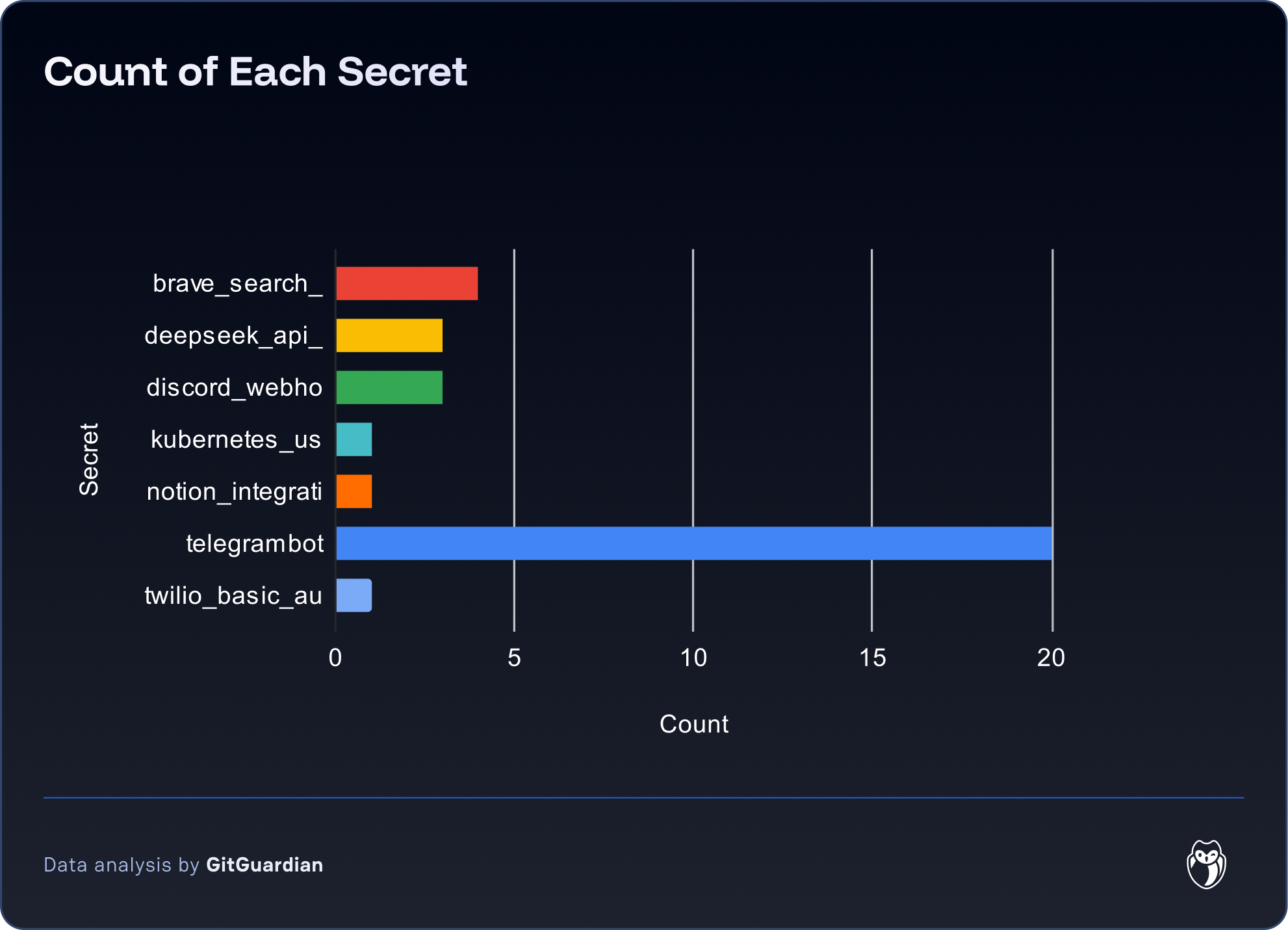
Since November, GitGuardian has detected 181 unique secrets, leaked from repositories with names containing either the clawdbot or moltbot keywords. At the time of writing, 65 secrets were still valid – 30% are Telegram Bot tokens, the easiest solution to interact with Moltbot.
Among these secrets, two caught our attention: a Notion Integration token and a Kubernetes User Certificate. Leaked on January 24, the first one gave access to the entire corporate documentation of a healthcare company. The second, leaked on January 18 gave full privileged access to a Kubernetes cluster of a fintech company, used to host a Moltbot instance. Inside the repository, other credentials were leaked, including for a private Docker images registry. Following these discoveries, we performed responsible disclosures to their owners.
From the standpoint of proactive detection, our Good Samaritan program immediately identified and notified by email 38 developers responsible for the leaks. Unfortunately, as of writing, most secrets are still valid.
DockerHub also contains public images containing secrets related to Moltbot. The first leak was detected on January 15, followed by several images every day. Now, 18 are still valid. Here, the types of secrets vary. We find GitHub tokens, AWS IAM keys, and Cloudflare tokens. This provides interesting information about the likely uses of Moltbot for automating cloud infrastructure-related tasks.
While the Moltbot documentation includes a dedicated security section warning users about the risks of hardcoded secrets, the proposed mitigation relies primarily on .gitignore rules—a pattern-based approach that fails silently when users forget to add sensitive files or when credentials end up in unexpected locations.The reality is that Moltbot installations contain multiple sensitive files by design:
|
Location |
Contains |
|
~/.clawdbot/clawdbot.json |
Gateway authentication tokens |
|
~/.clawdbot/identity/device-auth.json |
Device authentication credentials |
|
~/.clawdbot/credentials/*.json |
WhatsApp, Telegram, and other channel credentials |
|
~/.clawdbot/agents/*/auth-profiles.json |
Model provider API keys (OpenAI, Anthropic) |
|
~/clawd/ (workspace) |
Session logs, tool outputs, and any files the agent creates |
The nature of an AI agent's work makes preventing credential leaks challenging: the agent creates files, captures tool outputs, and logs session transcripts that may inadvertently include credentials pasted by users or fetched from external sources.
Running ggshield against a typical Moltbot configuration directory immediately reveals the problem:
> ~/.clawdbot/clawdbot.json: 1 secret detected
>> Secret detected: Generic High Entropy Secret
Validity: No Checker
27 | "auth": {
28 | "mode": "token",
29 | "token": "d6e2bd8e********************************922c7e89"
|____________________apikey____________________|
To address this gap, we developed a ggshield skill for Moltbot. Once installed, users can ask their assistant to scan the workspace for leaked credentials:
- "Check if my workspace contains any hardcoded secrets"
- "Scan my staged changes before I commit"
- "Set up a pre-commit hook to catch secrets automatically"
Important limitation: The skill runs on demand—it requires the user to prompt it. It does not automatically scan on commit or push. For users who want automated protection, the skill can install a git pre-commit hook that blocks commits containing detected secrets. The following are illustrative real-world use cases:
- Auditing the workspace:
"Scan my workspace for any secrets" Detects credentials in session logs, generated scripts, or files the agent created during tasks—before they ever reach git history.
- Pre-commit validation:
"Check my staged changes for secrets" Fast scanning of what's about to be committed, catching credentials before they enter version control.
- Setting up guardrails:
"Install a pre-commit hook to catch secrets" One-time setup that automatically blocks future commits containing detected credentials—the only automated protection the skill provides.
Prerequisites:
- ggshield CLI installed (see installation docs)
- A GitGuardian API key (see how to get one)
- The GITGUARDIAN_API_KEY environment variable set in your shell
Install via npx:
npx molthub@latest install ggshield-scannerThe skill is installed into your Moltbot workspace's skills/ directory. Start a new session for the agent to pick it up:
# Verify the skill is loaded
clawdbot skills list
# You should see:
# ✓ ready │ 📦 ggshield-scanner │ Detect 500+ types of hardcoded secrets…Closing the Loop
The leaked secrets we detected from Moltbot workspaces could have been prevented if users had access to integrated secret scanning. With the ggshield skill, Moltbot users can ask their AI assistant the same question they'd ask a security-conscious colleague: "Is this safe to push?"—and get an answer backed by GitGuardian's detection engine before the damage is done. The skill is available on ClawdHub at ggshield-scanner, and the source code is published at https://github.com/GitGuardian/ggshield-skill.
*** This is a Security Bloggers Network syndicated blog from GitGuardian Blog - Take Control of Your Secrets Security authored by Guillaume Valadon. Read the original post at: https://blog.gitguardian.com/moltbot-personal-assistant-goes-viral-and-so-do-your-secrets/
如有侵权请联系:admin#unsafe.sh