嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。首先,我得仔细阅读这篇文章,理解它的主要观点。 文章讲的是现在的孩子们玩游戏时,常常会下载各种模组、作弊器或者所谓的性能增强工具。这些看似无害的东西其实可能隐藏着恶意软件,特别是信息窃取者(infostealer)。一旦下载并运行这些文件,恶意软件就会在后台窃取用户的浏览器密码、会话cookie、认证令牌等敏感信息。 这些信息被收集后会被上传到暗网市场或犯罪平台,然后被用于非法活动,比如入侵企业系统。因为孩子们通常会使用家庭电脑,而家庭电脑可能连接到公司的网络或存储有工作相关的敏感信息。所以,一个看似简单的游戏模组下载可能会导致整个企业被入侵。 文章还提到,攻击者利用了孩子们的信任和对快速获取游戏优势的渴望。他们通过YouTube视频、Discord链接或GitHub仓库来分发这些恶意软件。孩子们往往不会怀疑这些来源的安全性,从而轻易点击下载并运行。 此外,文章指出这种威胁不仅仅是针对孩子的问题,而是涉及到身份盗窃的普遍问题。现代网络攻击越来越多地利用合法凭证进行入侵,而不是传统的漏洞利用。因此,保护个人和企业的数字身份变得尤为重要。 总结起来,这篇文章主要警告家长们和企业注意孩子们在下载游戏相关文件时可能带来的安全风险,并强调了信息窃取者在当前网络攻击中的重要性。 </think> 孩子们通过搜索游戏模组、作弊器或性能增强工具下载恶意软件(如infostealer),窃取浏览器密码、认证令牌等敏感信息,并将其用于入侵企业系统。攻击者利用孩子们的信任和对快速获取游戏优势的渴望,在YouTube、Discord或GitHub等平台分发恶意软件。这种威胁不仅影响孩子,还可能导致企业数据泄露和身份盗窃问题。 2026-1-29 15:15:29 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

Growing up I always wanted to play the newest and most exciting games, and for me it was FIFA, Zelda and Red Alert. For my kids today it’s Roblox, Minecraft, and Call of Duty.
I remember, it wasn’t easy to convince your parents to constantly pay for these new games, so you compromise or you look up in Google “Free FIFA 2003 download.”
While today I know it’s illegal, for most kids, it starts innocently. Your child wants to make Roblox run faster. Or unlock a feature. Or install a mod that their friends are using.
They search Google or YouTube, find a video titled “NEW Roblox FPS Booster 2025 - FREE,” click a Discord link, download a ZIP file, and double-click an executable called something like RobloxExecutor.exe.
The game launches. Nothing looks wrong.
But in the background, something far more serious just happened. That “mod” wasn’t a mod at all. It was infostealer malware.
Within seconds, malware running on your child’s laptop harvested every saved browser password, session cookie, and authentication token on the system: Gmail, Discord, Steam, Microsoft. Maybe your corporate VPN, maybe Okta, maybe Slack, maybe GitHub.
The infection happened in your living room. The breach happens at your company. And neither you nor your child will notice anything until it’s too late.
Gamers Are Now a Primary Infection Vector
This isn’t science fiction. It happens every day. According to threat intelligence research, gamers have become one of the largest and most reliable infection pools for infostealer malware.
One recent analysis found that over 40% of infostealer infections originate from gaming-related files, including cheats, mods, cracked games, and “performance boosters.”
From an attacker’s perspective, gamers are the perfect targets:
-
The majority are children or teenagers
-
They constantly download third-party files
-
They disable antivirus to “make mods work”
-
They trust Discord links and GitHub repos
-
They search for shortcuts, cheats, and bypasses
-
They run random executables without hesitation
Most importantly: they are trained to execute untrusted code.
That behavior is exactly what infostealer operators need.
The Modern Roblox Mod Infection Flow
A typical Roblox infostealer infection looks like this:
-
Child searches for:
-
“Roblox FPS unlocker”
-
“Roblox executor free”
-
“Roblox script injector”
-
They land on:
-
A YouTube video
-
A Discord server
-
A GitHub repository
-
A Google Drive link
-
They download a file:
RobloxMod.zip
+- install.exe
They run install.exe
What actually executes is not a mod. It’s Lumma, RedLine, Vidar, or Raccoon, which are some of the most common infostealers on the planet.
No exploit. No vulnerability. No hacking required.
Just a simple psychological mechanism exploitation of a user (child) double-clicking a file.
Am I Exaggerating the Impact of Infostealer Hiding in Games?
I thought to myself that I am probably exaggerating. Kids, downloading, malware! No way.
So, I typed in Google “Roblox mod free,” and this was the first result I saw.
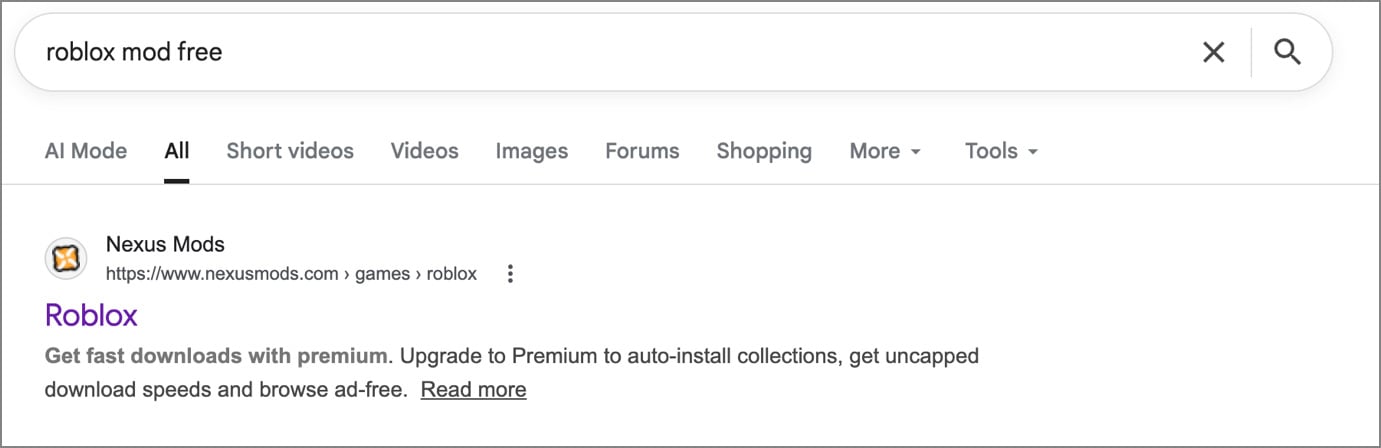
I went into the website, and then I saw the second option, uploaded January, 9th 2026.
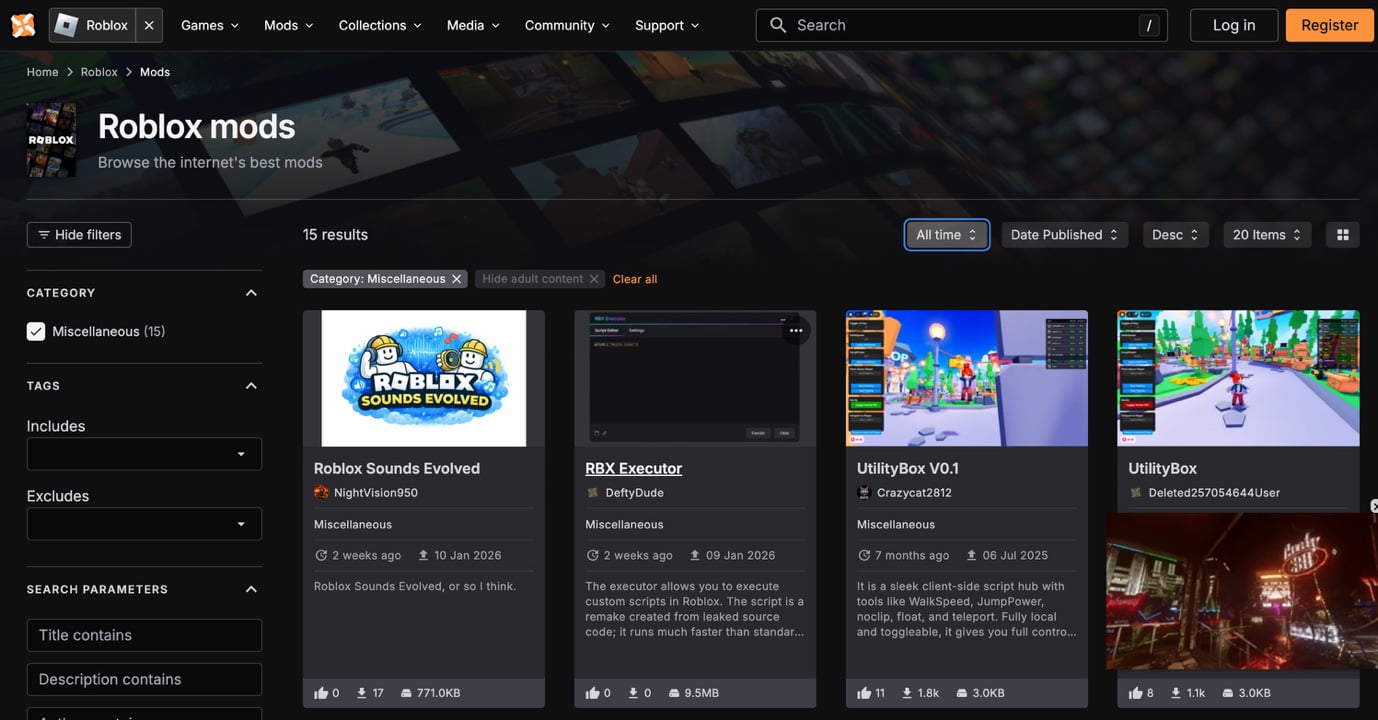
I clicked on this option and tried to download the mod.
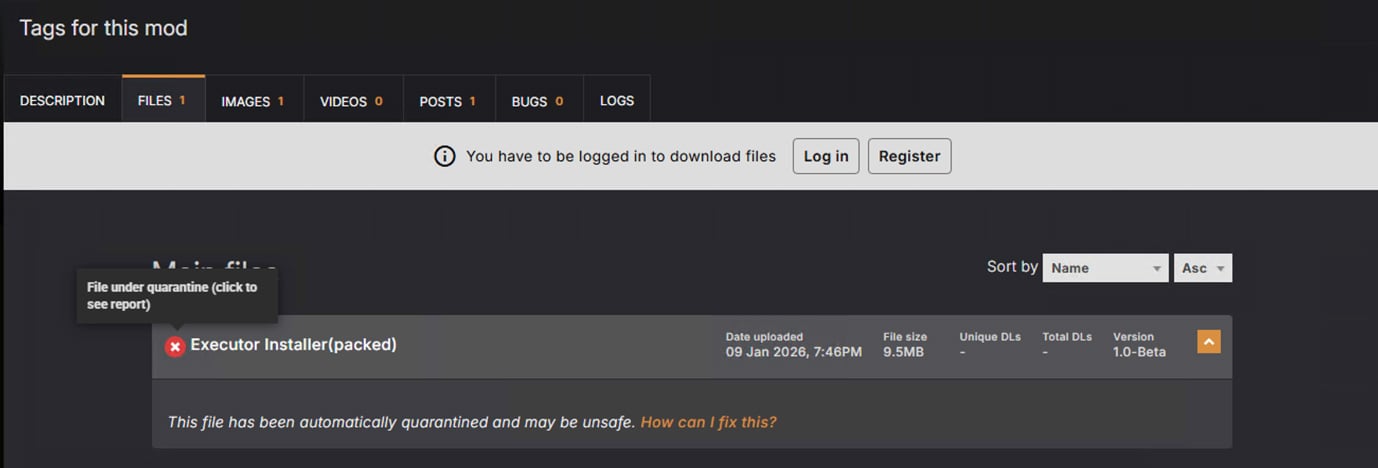
But wait, it’s quarantined, and clicking to see the report links to Virus Total, where you can see that this mod isn’t that innocent.
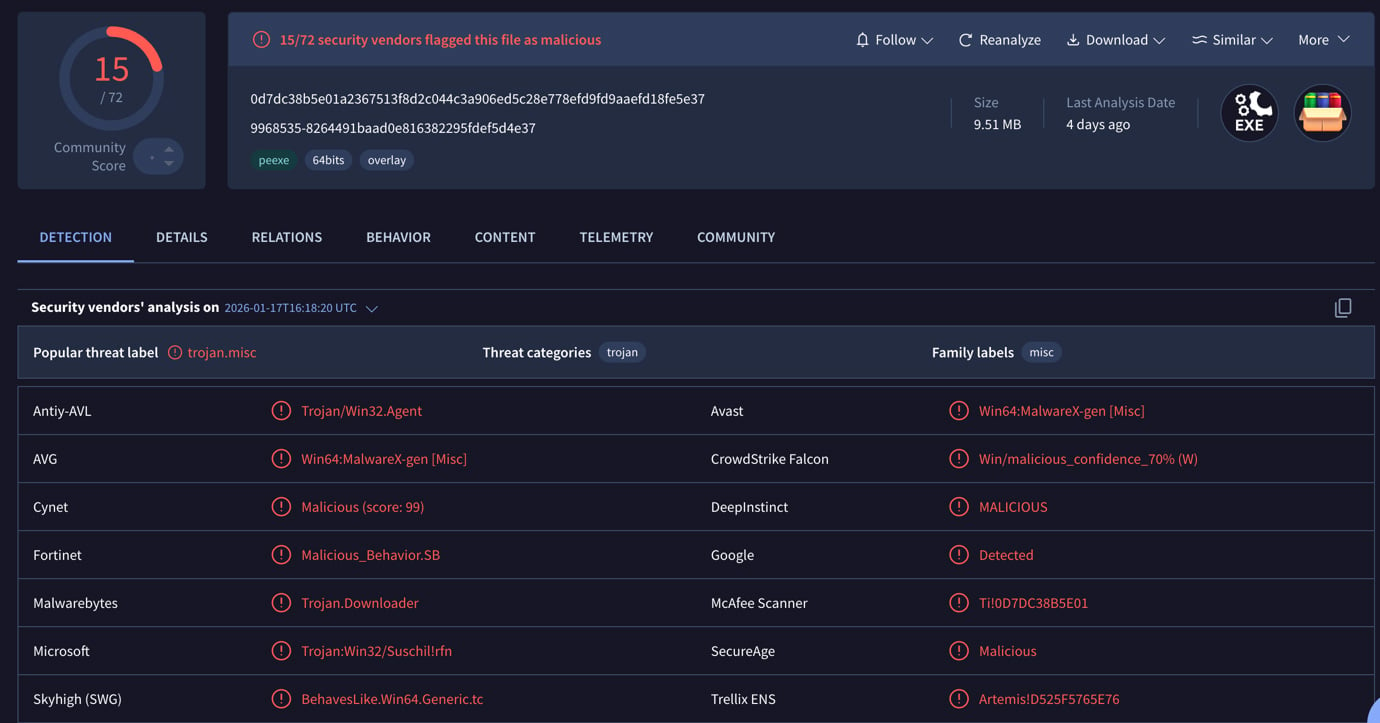
What an Infostealer Actually Does
Once executed, a modern infostealer immediately begins harvesting identity data from the system:
-
Browser saved passwords
-
Session cookies
-
Autofill data
-
OAuth tokens
-
Discord tokens
-
VPN credentials
-
Crypto wallets
-
Cloud logins
-
SSH keys
-
FTP credentials
From:
-
Chrome, Edge, Firefox, Brave
-
Outlook and mail clients
-
Password managers
-
VPN clients
-
Developer tools
This entire process takes seconds.
The data is then packaged into what’s known as a “stealer log," a structured archive representing a full digital snapshot of that person’s identity.
That log is uploaded to:
-
Telegram channels
-
Russian Market
-
Dark web marketplaces
-
Criminal SaaS panels
where it is sold, resold, and indexed.
Why This Becomes an Enterprise Breach
To be honest, if you use your company laptop and stay aligned with corporate policy, compliance and guidelines, your kid probably won’t be able to download anything to the corporate computer.
Here’s the part most people miss. Your child’s laptop isn’t just a gaming device, or alternatively gamers aren’t the only targets, attackers booby-trap anything free on the net.
It could be:
-
Illegal software of any kind
-
Fake AI tools
-
Browser extensions
-
Fake installers for legitimate software
-
Crypto and web3 tools
-
Malicious documents and email attachments
-
Adult and dating content
-
Fake system utilities
So, basically everything that can run and is free on the internet is a potential horror movie scene.
If you downloaded any of the above and you do any of these actions:
-
You check work email
-
You access Slack
-
You log into Okta
-
You connect to VPN
-
You approve MFA pushes
-
You access GitHub
-
You open internal dashboards
Infostealers don’t care who clicked the file. They care what identities exist on the machine.
So, a Roblox mod (or anything malicious) can steal:
-
Corporate SSO credentials
-
Active Directory passwords
-
Session cookies that bypass MFA
-
Access to internal SaaS platforms
And now your company is compromised - not through a vulnerability, but through a leisure download.
Trading Your Identity in the Underground
On cybercrime marketplaces, threat actors can purchase everything from raw infostealer logs to step-by-step tutorials, and even fully managed “Stealer-as-a-Service” offerings.
In the screenshot above, you can observe an ad that offers access to Exodus stealer for a monthly cost of $500 USD and lifetime access for $2K USD.
While this specific ad falls under the too good to be true category and thus a scammer ad trying to defraud criminals, there are more realistic ads in the underground selling stealer access.
(Flare link to post, sign up for free trial to access if you aren’t already a customer)
You can also see the logs themselves. Below is a typical logs structure, including IP addresses, domains, and credit cards. In addition, they can also include single sign on (SSO), cookies, tokens, passwords, etc.
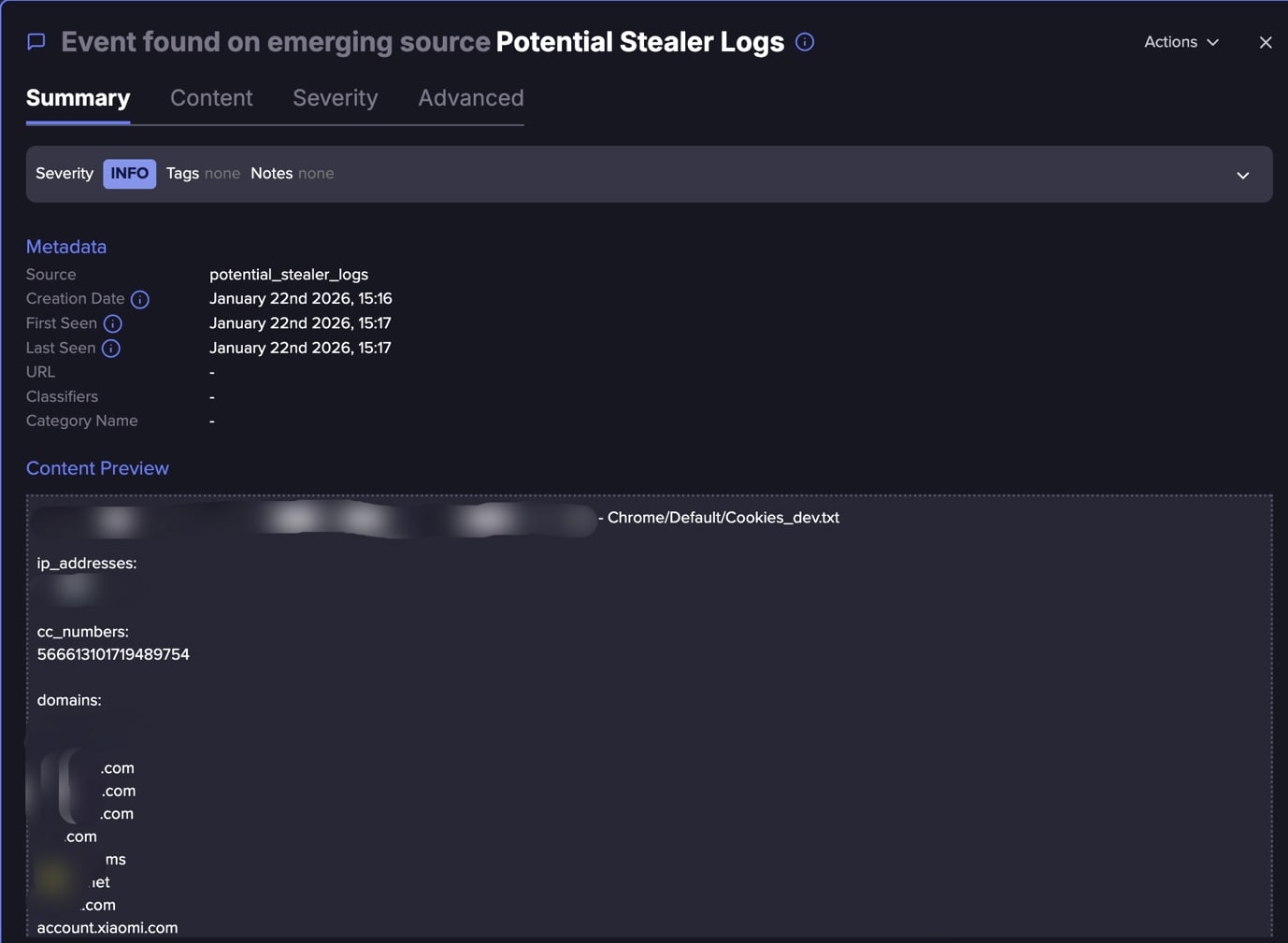
(Flare link to post, sign up for free trial to access if you aren’t already a customer)
Below you can also see a tutorial in the underground illustrating the central part infostealers possess as part of the cybercrime attack chain:
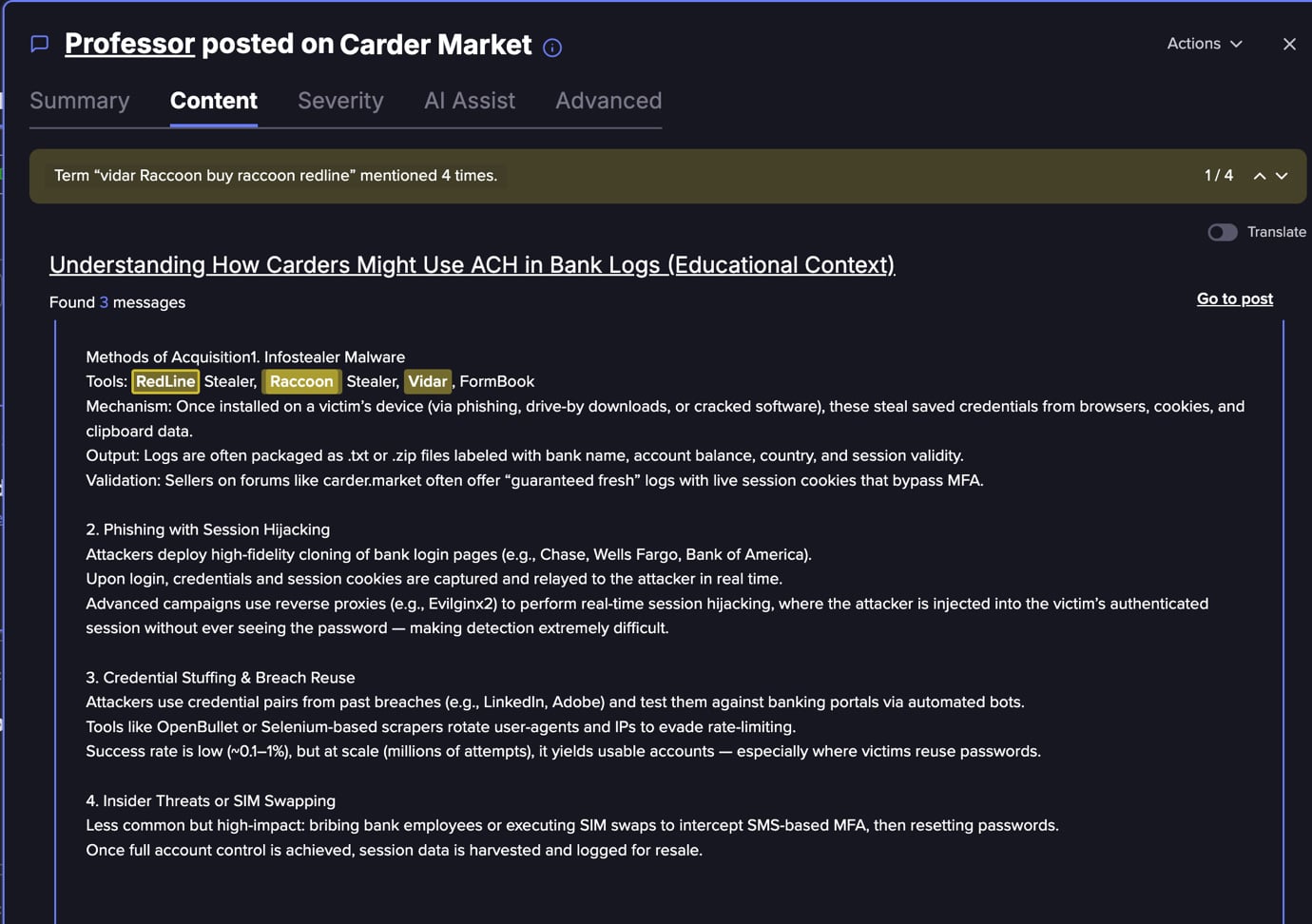
(Flare link to post, sign up for free trial to access if you aren’t already a customer)
This Is Not a “Kid Problem” - It’s an Identity Problem
What makes infostealers so dangerous is not the malware itself, but rather what they steal. Infostealers have effectively turned identity into the primary attack surface.
Instead of:
-
Exploiting software
-
Finding vulnerabilities
-
Writing exploits
Attackers now:
-
Harvest credentials at scale
-
Buy identities in bulk
-
Log in legitimately
-
Bypass MFA with session tokens
-
Blend into normal user behavior
This is why modern breaches increasingly start with:
“Valid credentials were used.”
Not:
“A vulnerability was exploited.”
And this is why infostealers have quietly replaced exploits as the dominant initial access vector.
Learn more by signing up for our free trial.
Sponsored and written by Flare.
如有侵权请联系:admin#unsafe.sh